
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
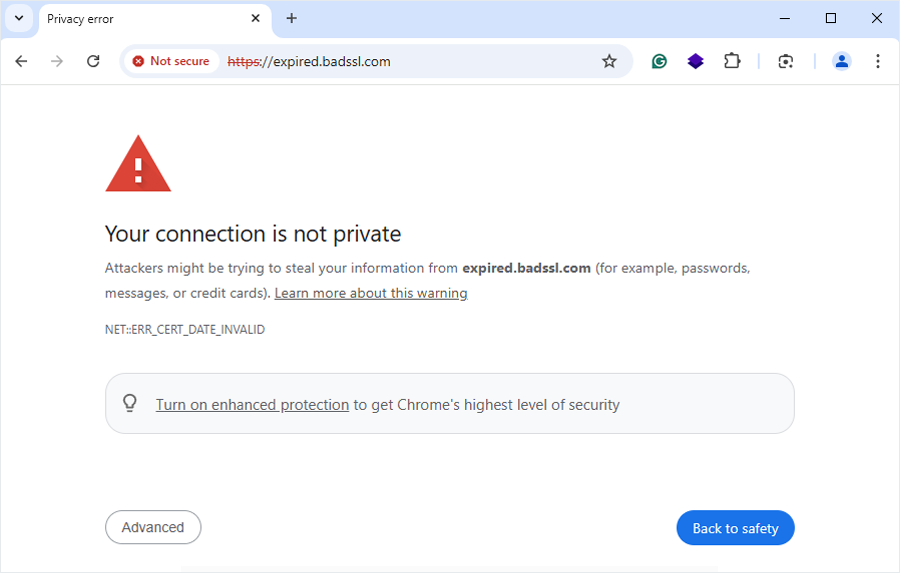
How to Renew SSL Certificate Easily
If you are a website owner, then you must be aware of the importance of keeping your online presence secure using SSL certificates. The connection security that SSL certificates provide between websites and visitors helps instantly enhance site’s credibility. But, like most certificates, SSL certificates also have expiration dates, and when they expire, your site’s
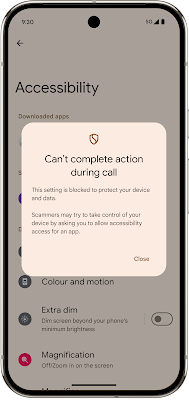
What’s New in Android Security and…
Posted by Dave Kleidermacher, VP Engineering, Android Security and Privacy Android’s intelligent protections keep you safe from everyday dangers. Our dedication to your security is validated by security experts, who consistently rank top Android devices highest in security, and score Android smartphones, led by the Pixel 9 Pro, as leaders in anti-fraud efficacy. Android is

TDF Extends Data-Centric Security Beyond the…
DSPM (Data Security Posture Management) solutions are some of the hottest companies in cybersecurity right now. We’ve written about companies like Cyera, Rubrik, and Varonis, who each create powerful frameworks for protecting data that companies possess internally, surfacing risk and enabling better data governance across enterprise environments.

ESET Threat Report H1 2025: Key…
ESET Chief Security Evangelist Tony Anscombe looks at some of the report’s standout findings and their implications for organizations in 2025 01 Jul 2025 The ESET research team has released the H1 2025 issue of the ESET Threat Report, offering a detailed look at the key trends and developments that defined the cyberthreat landscape from
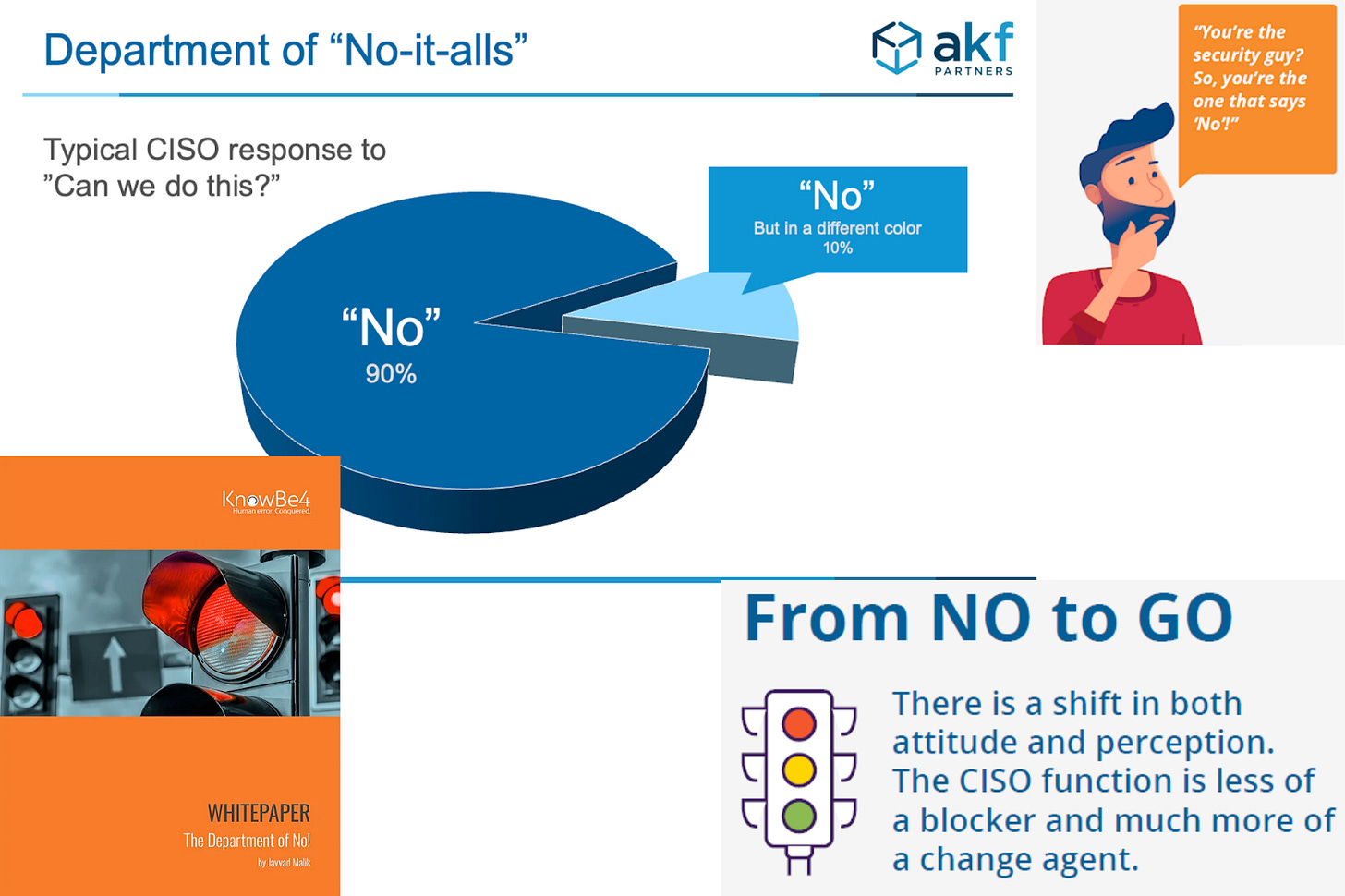
Security is not the department of…
Nearly once a week, I hear someone say that security needs to stop being a department of “No” and that instead, it needs to become a “business enabler”. Every time someone says it, I can’t help but wonder where this idea originated and how it was able to become so widespread. In this piece, I

thank you — Matt Palmer
Thank you to CSOonline for the CSO30 cyber security award this week. It’s much appreciated and a pleasure to be in such good company with so many capable and passionate people. Cybersecurity is still an incredible field where no two roles, or people, are the same. ___ Matt Palmer is an award winning cyber security
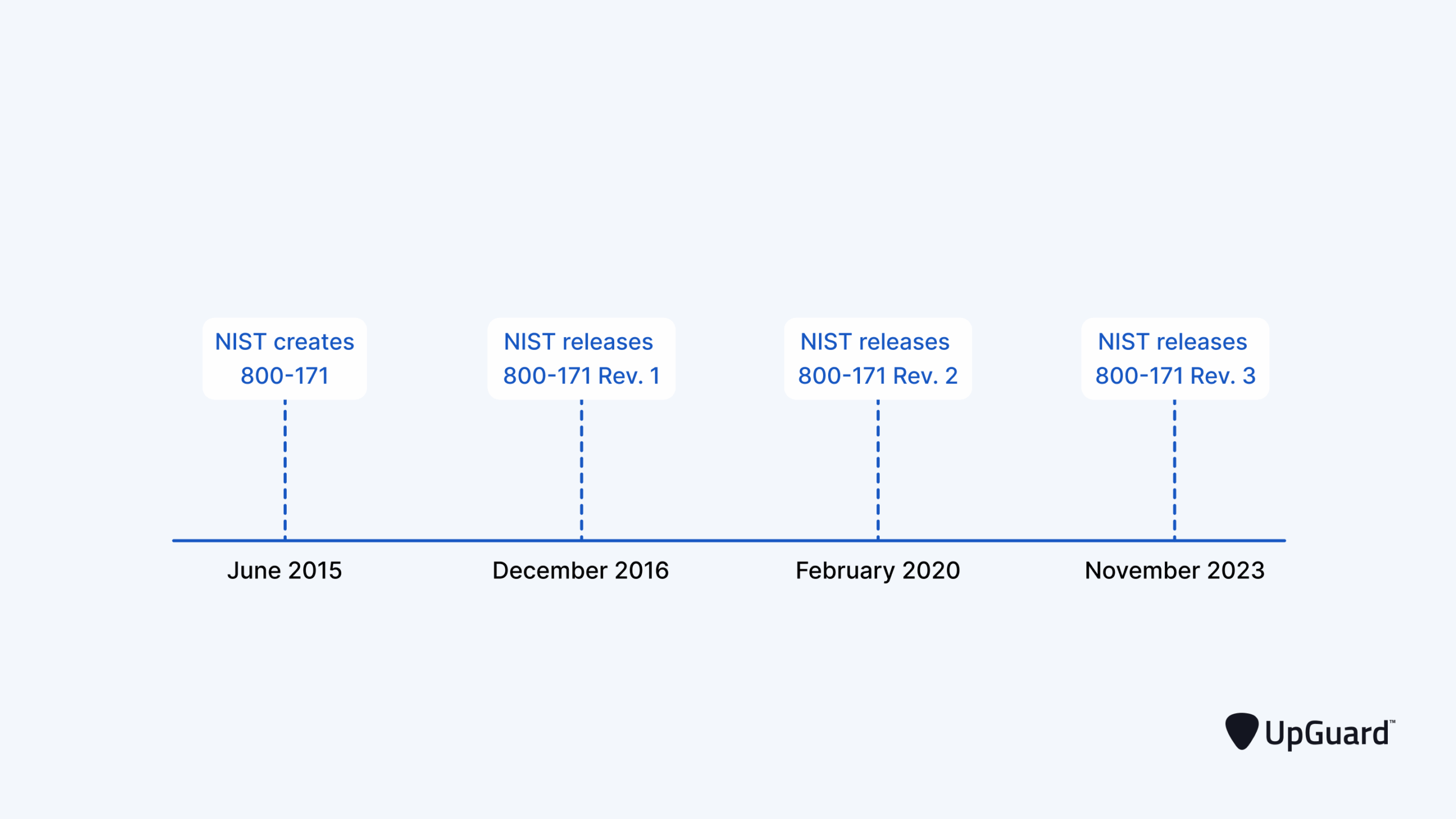
How to Comply with NIST SP…
The National Institute of Standards and Technology (NIST) developed the NIST 800-171 framework to set guidelines and security requirements for protecting controlled unclassified information (CUI). NIST first created the framework in June 2015 but has since revised the publication several times, most recently in November 2023. NIST’s latest revision, known as NIST 800-171 Revision 3,

What is Penetration Testing? Importance, Types…
Penetration testing is a simulated cyberattack to identify security flaws. Learn its types, benefits, process, and why it’s essential for your business. In today’s ever-evolving cyber landscape, cyberattacks are not a matter of “if” but “when.” Businesses, large and small, are constantly under threat from hackers seeking to exploit security vulnerabilities. One of the most

Zero Trust Data Protection: Securing Your…
Zero Trust Data Protection: Securing Your Data in a Perimeterless World The threat landscape for businesses has never been more complex. Hackers are constantly evolving their tactics, making data security a critical priority. In recent years, data exfiltration has become a prime goal of cybercriminals, especially with the rise of double extortion ransomware that not

The State of OSHA Training for…
Introduction OSHA training for healthcare workers has never been more crucial. With regulatory compliance under increased scrutiny, healthcare facilities must ensure that their staff is adequately trained to prevent workplace hazards, ensure patient safety, and comply with federal regulations. Recent trends indicate a heightened focus on compliance violations, while private initiatives are stepping up to










