
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
Taking the shine off BreachForums –…
On June 25, 2025, French authorities announced that four members of the ShinyHunters (also known as ShinyCorp) cybercriminal group were arrested in multiple French regions for cybercrime activities and involvement in the English-language underground forum known as BreachForums. The coordinated global law enforcement effort targeting the ‘ShinyHunters’, ‘Hollow’, ‘Noct’, and ‘Depressed’ personas followed the February

A Script to Query for EC2…
Using Amazon Q helped write the script in < 3 hours (2 if you don’t count the security rabbit hole) ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code. 🔒 Related Stories: Cybersecurity | Penetration Tests 💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~

Welcome Our Newest Associate Participating Organizations
We are pleased to welcome the newest organizations that have joined as Associate Participating Organizations of the PCI Security Standards Council (PCI SSC). These organizations play a crucial role in supporting the evolution of the PCI security standards and programs and promoting the implementation of PCI security standards worldwide to protect payment data. We

Webinar on demand: The ROI of…
Join cybersecurity leaders from G’Secure Labs and Logpoint as they break down what truly defines SOC success. Discover how to shift your focus from alert management to business impact. In this session, you will get: Actionable insights into measuring SOC effectiveness Proven strategies to reduce alert fatigue and optimize security outcomes Real-world examples of
My First Book Is 20 Years…
On this day in 2004, Addison-Wesley/Pearson published my first book, The Tao of Network Security Monitoring: Beyond Intrusion Detection. This post from 2017 explains the differences between my first four books and why I wrote Tao. Today, I’m always thrilled when I hear that someone found my books useful. I am done writing books on

What are the Benefits of a…
Date: 7 July 2025 What is the benefit of a Cyber Tabletop Exercise in 2025? That question can be answered with one single line – Have you checked out our recent monthly list of the top cyber attacks, data breaches and ransomware attacks? If you so much as skim through it, you’ll know just how

Anatsa Android Banking Trojan Hits 90,000…
Jul 08, 2025Ravie LakshmananMalware / Mobile Security Cybersecurity researchers have discovered an Android banking malware campaign that has leveraged a trojan named Anatsa to target users in North America using malicious apps published on Google’s official app marketplace. The malware, disguised as a “PDF Update” to a document viewer app, has been caught serving a
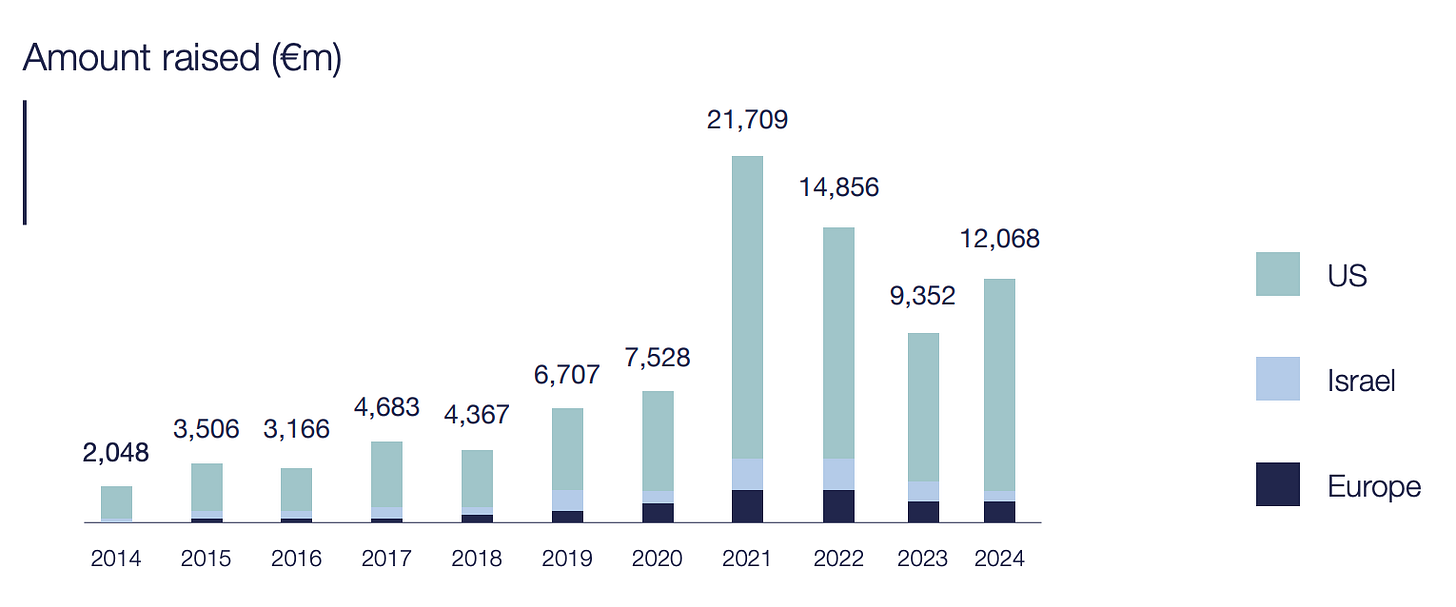
Fewer Cheques, Tougher Checks: Cyber VC…
Hello Cyber Builders 🖖 Cybersecurity is at the top of everyone’s mind, and AI brings more opportunities and threats at the same time. Therefore, we would expect funding levels to be high and investors to be eager to seize opportunities… That would be great, wouldn’t it? While investment levels are still solid, the number of

Using AI to Battle Phishing Campaigns…
The Cisco Live Network Operations Center (NOC) deployed Cisco Umbrella for Domain Name Service (DNS) queries and security. The Security Operations Center (SOC) team integrated the DNS logs into Splunk Enterprise Security and Cisco XDR. To protect the Cisco Live attendees on the network, the default Security profile was enabled, to block queries to known

Heimdal Partners with Portland to Deliver…
Amsterdam, Netherlands – July 3, 2025 – Heimdal, a leading European provider of unified, AI-driven cybersecurity solutions, today announced a strategic distribution partnership with Portland, a top-tier IT channel specialist in the Benelux region. The collaboration gives Managed Service Providers (MSPs) across Belgium, the Netherlands, and Luxembourg streamlined access to Heimdal’s award-winning Extended Detection and










