
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
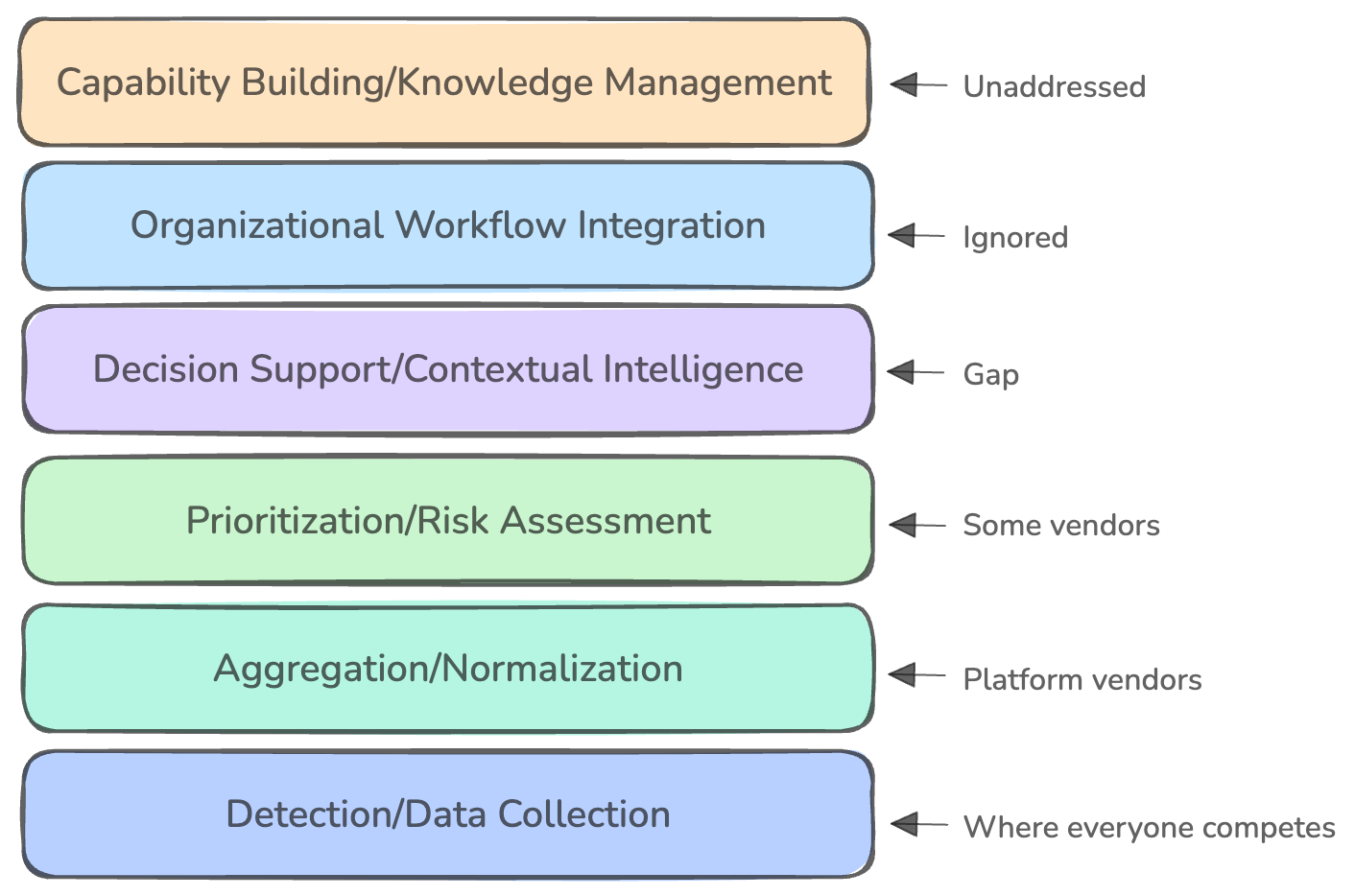
why theory doesn’t match practice
This week, Venture in Security is excited to feature a guest article from Nielet D’Mello. Nielet is a security engineer with nearly a decade of experience designing and scaling secure systems across the software development lifecycle. She has held roles at McAfee, Intel, and currently Datadog, working across consumer, enterprise, and cloud-native security domains. Her
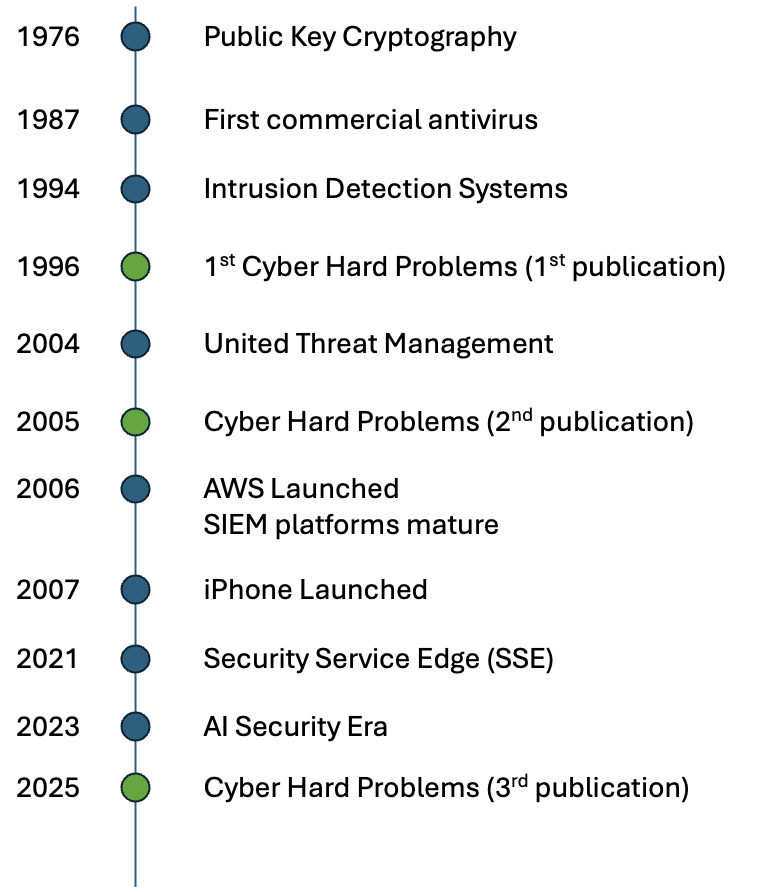
Cisco Contributes to Cyber Hard Problems…
While Cisco often focuses on business growth and market leadership, our most rewarding work happens when we set those metrics aside. These projects aren’t about driving profits — they’re about using our expertise to tackle challenges that benefit everyone. I want you to meet Dr. Hyrum Anderson, a senior director of AI & security in

Iran Hacked Trump Campaign: A Deep…
In a confirmed act of state-sponsored hacking in U.S. elections, Iran hacked Trump campaign in 2020. The attackers, tied to Iran’s Islamic Revolutionary Guard Corps (IRGC), used spear-phishing and coordinated disinformation to breach systems and influence voters. This wasn’t a one-off situation. It was a full-spectrum cyber operation targeting political infrastructure. Understanding how it happened

Top 10 Influencers to Follow In…
If you’re in the cybersecurity world — whether you’re a CISO, ethical hacker, compliance pro, or just love staying ahead of cyber threats — following the right voices can make all the difference. From founders and educators to threat hunters and security journalists, the people on this list are shaping the way we think about

Endpoint Vulnerability Remediation: From Alert to…
With the boom of cloud usage and AI, organizations have been facing an increase in cybersecurity challenges due to which they realize the need for endpoint vulnerability remediation. Many organizations failed to see the endpoint security vulnerabilities lying unfixed in their endpoint devices, and the risk of exploitation by threat actors grows the longer a

India’s First Global Computer Virus
In the cinematic tapestry of cybersecurity, where tales of intrigue and innovation collide, one story emerges from the shadows of the past. It’s a story that began in the early 1990s, during the DOS era, when computer viruses were still a novel and mysterious menace. This is the tale of Joshi, a virus of Indian

Unlocking Engagement: Creative Trade Show Exhibit…
Here, I’ll show you the creative trade show exhibit designs for magnetic marketing strategies. The trade show aspect of marketing can be competitive, and a well-designed booth can do more than look good. A well-designed booth can be the perfect place to draw in visitors, build brand awareness, and create an experience that is memorable
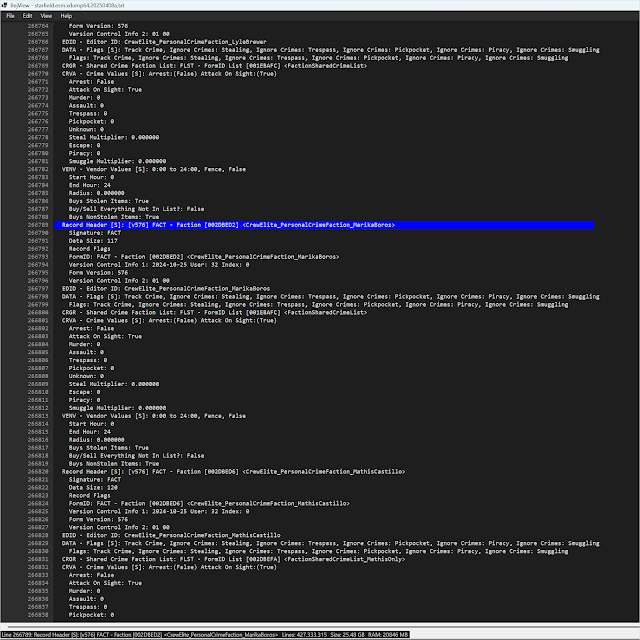
Creating a Large Text File Viewer…
The problem I was trying to solve this time was opening and searching extremely large text files. I used to use the old Mandiant Highlighter program for this, but it was last updated in 2011 and couldn’t handle the 26 GB text file I wanted to open. If you’re wondering what that

Why Most Privacy Programs Fail Audits…
In privacy, what you don’t know can hurt you. Your Records of Processing Activities (ROPA) may be up to date. Your data flows may look airtight. But if your privacy team doesn’t have visibility into all the personal data processed in your organization—including the documents, emails, images and forgotten folders —then your program is built
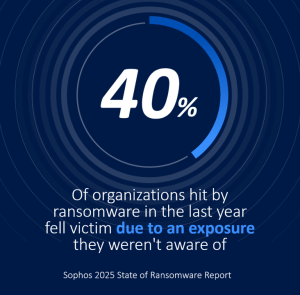
Introducing Internal Attack Surface Management (IASM)…
Cyber threats continue to evolve, and organizations must stay ahead by fortifying their defenses. While external attack surface management (EASM) identifies vulnerabilities that could be exploited from outside the network, many organizations face an internal blind spot: hidden vulnerabilities within their environments. 40% of organizations hit by ransomware in the last year said that they










