
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

The Impact of Artificial Intelligence on…
Credit: NICE The NICE Workforce Framework for Cybersecurity (NICE Framework) was revised in November 2020 as NIST Special Publication 800-181 rev.1 to enable more effective and rapid updates to the NICE Framework Components, including how the advent of emerging technologies would impact cybersecurity work. NICE has been actively engaging in conversations with: federal departments and

Tips to make your summer travels…
Ready, set, pack! Summer travel season is here and that means family road trips, beach vacations, international adventures and more. While summertime is prime time for getaways, did you know it’s also prime time for online fraud? Scammers are targeting the travel industry, putting millions of travelers at increased risk. Research shows that the travel
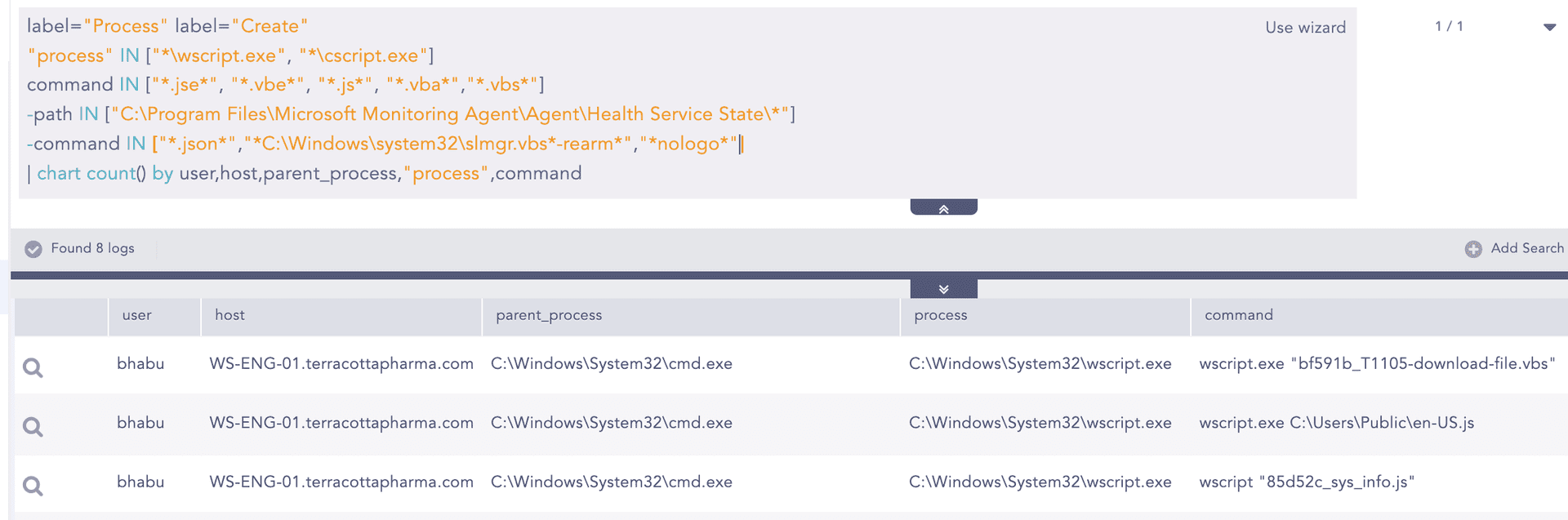
Pinpointing GRU’s TTPs in the Recent…
Introduction Russia’s GRU Unit 26165, also known by several aliases, including APT28, is a name synonymous with cyber espionage, having cast a long shadow over the geopolitical landscape for over two decades. Its target sectors, government institutions, militaries, and security organizations, clearly reflect its motives, which are stealing sensitive information for political and military gain.

HOW TO BECOME CERTIFIED LEAD IMPLEMENTER…
Advertisement ABOUT CERTIFIED LEAD IMPLEMENTER TRAINING AND EXAMINATION FOR INFORMATION SECURITY MANAGEMENT SYSTEM ISO / IEC 27001 Learn and get certified as a professional in implementation of ISO 27001 standard through our self-paced E-learning interactive course which comprises of 4 modules. Upon completion of these modules, you can appear for an examination and get certified

CISA Adds Four Critical Vulnerabilities to…
Jul 08, 2025Ravie LakshmananCyber Attacks / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The list of flaws is as follows – CVE-2014-3931 (CVSS score: 9.8) – A buffer overflow vulnerability in Multi-Router

The Only AI Tool AppSec Needs….
Software quietly runs the systems we rely on—our banks, logistics, communication, and cars. But for many AppSec teams, that software is a tangle of disconnected alerts and late-breaking vulnerabilities. The shift-left movement wasn’t supposed to add noise—it was supposed to make security part of how we build. Now, with liability rising and complexity accelerating, that
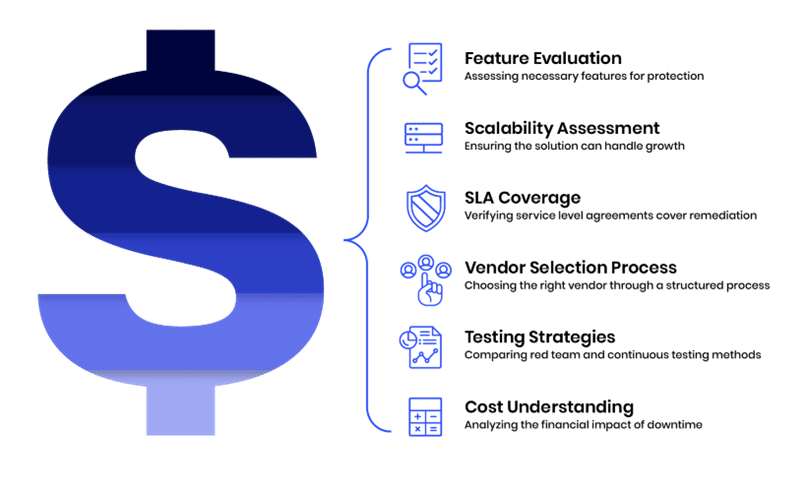
Choosing the Right DDoS Protection: 6…
On March 10, 2025, X experienced multiple outages due to a large-scale DDoS attack. The attack succeeded because the DDoS protection deployed had a vulnerability that was exploited. While Elon Musk did acknowledge the severity of the incident – it remains unclear if X is taking the necessary steps to actively prevent the next DDoS
Shannon Edwards Reveals the Student Data…
As technology is integrated deeper into classrooms, the lines between education and data privacy have been destroyed by for-profit data miners. This week, privacy advocate Shannon Edwards reveals how educational apps harvest sensitive information from children, commodify their data, and what parents can do to fight it.

CyberHoot Newsletter – June 2025
CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to
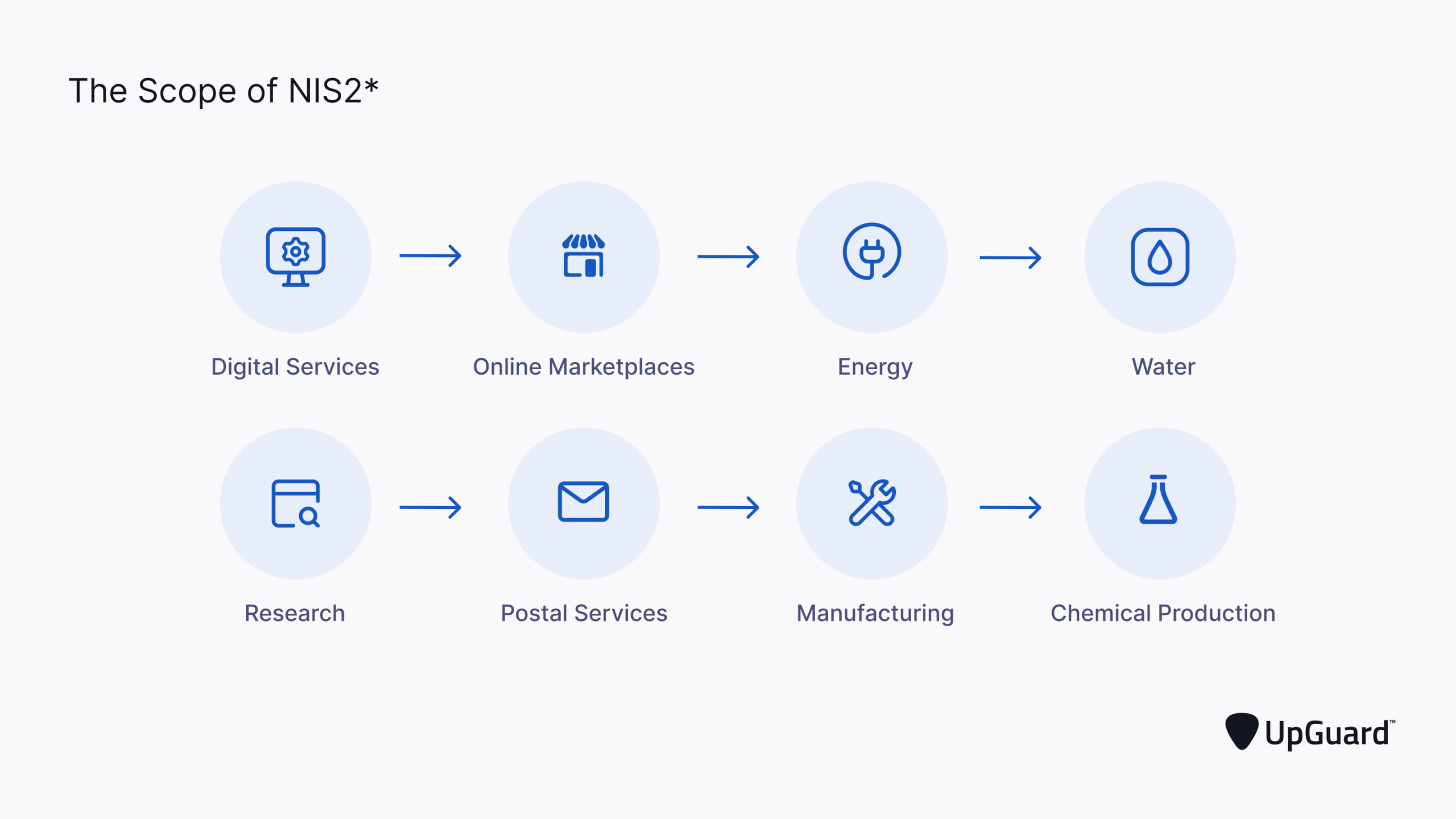
Preparing for NIS2: A Compliance Guide…
In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or










