
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Jailbreaks, Injections, and Agentic Risks
AI has officially moved out of the novelty phase. What began with people messing around with LLM-powered GenAI tools for content creation has rapidly evolved into a complex web of agentic AI systems that form a critical part of the modern corporate landscape. However, this transformation has given new life to old threats, transforming the
Setting Up a Pentesting Environment for…
With the advent of commercially available virtual reality headsets, such as the Meta Quest, the integration of virtual and augmented reality into our daily lives feels closer than ever before. As these devices become more common, so too will the need to secure and protect the data collected and stored by them. The intention of

Ready-to-Heat Food Safety: Why You Must…
As of June 2025, sixteen people across the U.S. have been hospitalized after eating Ready-to-Heat (RTH) chicken meals contaminated with Listeria monocytogenes. Of them there are three confirmed deaths, and pragnancy associated illness that resulted in a fetal loss. These meals, sold under popular store brands like Marketside (Walmart) and Home Chef (Kroger), were fully cooked

Chinese wegen US-Spionageverdacht in Mailand festgenommen
Ein Chinese wurde wegen Cyberbetrug und Identitätsdiebstahl festgenommen. Brian A Jackson – shutterstock.com Wegen des Verdachts der US-Spionage ist ein Chinese am größten Flughafen Mailands festgenommen worden. Wie die italienische Nachrichtenagentur Ansa berichtet, soll der 33-Jährige FBI-Ermittlungen zufolge Teil einer Hackergruppe gewesen sein, die 2020 unter anderem Daten zu Covid-19-Impfstoffforschung an der Universität Texas ausspioniert

The Generative AI Revolution: Trends That…
The Generative AI Revolution: Trends That Will Shape Your 2025 Strategy Hey there, tech-savvy reader! Let’s admit it—Generative AI is no longer some futuristic buzzword floating around in TED Talks or sci-fi flicks. It’s here. It’s working. And it’s reshaping everything—from how we work, to how we create, to how we think. 2025 is turning

Cybersecurity Compliance in South Africa
A Continued Cycle South Africa has had a slow approach to compliance with the government regulations and laws set in place. This problem has been exposed at every turn as South Africa has continued to show its vulnerabilities, and cyber criminals see them and abuse them. The institution of much of the newer legislation has

Vulnerability Management vs. Exposure Management: What’s…
In the world of cybersecurity, there’s always a new buzzword, but some trends are more than just hype. Over the last couple of years, “exposure management” has been quietly gaining traction. While most organizations still rely on traditional vulnerability management to keep threats at bay, the reality is that attackers no longer think in terms
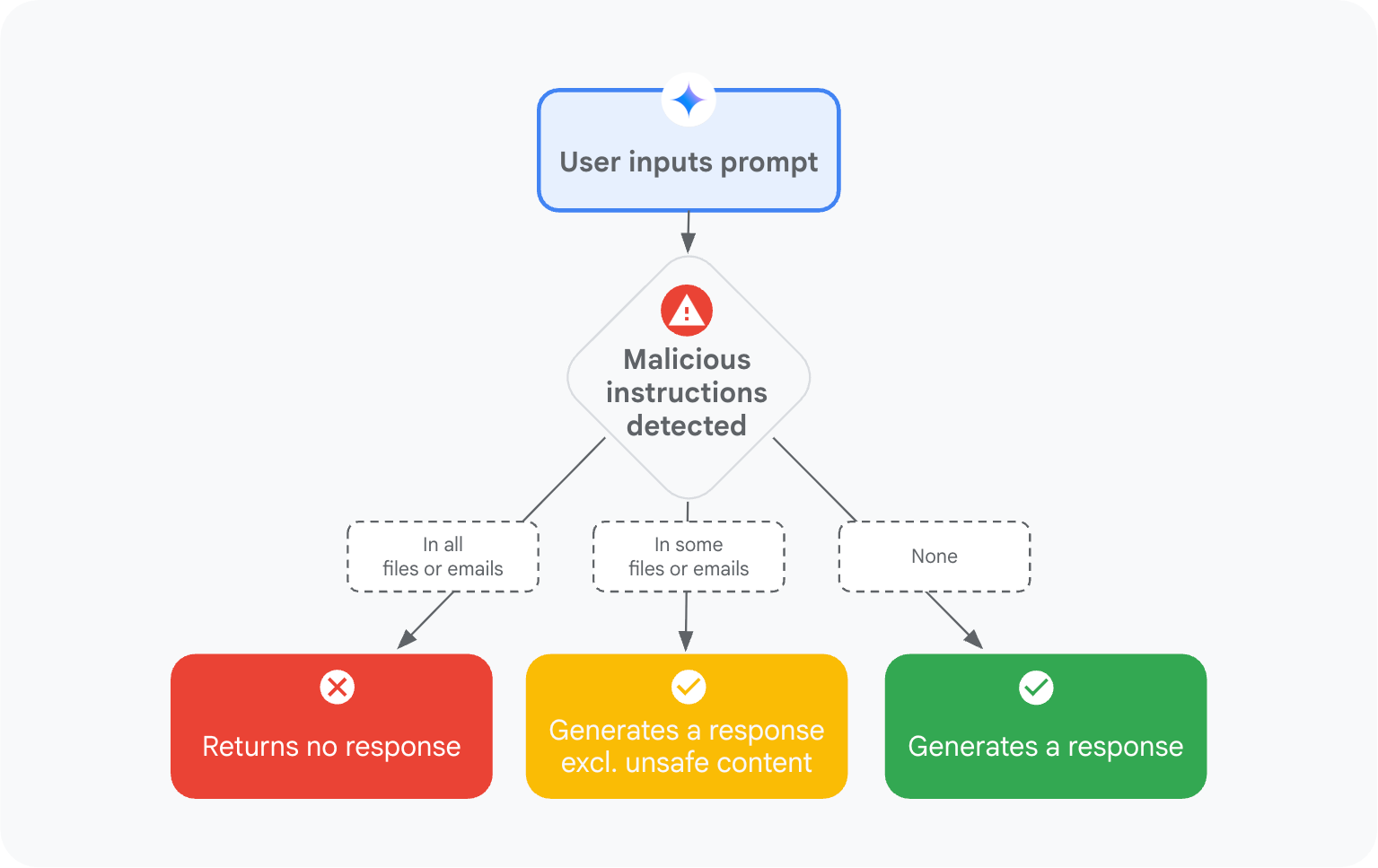
Mitigating prompt injection attacks with a…
With the rapid adoption of generative AI, a new wave of threats is emerging across the industry with the aim of manipulating the AI systems themselves. One such emerging attack vector is indirect prompt injections. Unlike direct prompt injections, where an attacker directly inputs malicious commands into a prompt, indirect prompt injections involve hidden malicious

How to Boost Speed and Security…
In today’s world, online gaming isn’t just a hobby—it’s a serious, competitive arena where speed and security can make or break your experience. Whether you’re battling in a fast-paced shooter or strategising in a multiplayer RPG, lag and security threats are constant challenges that gamers face. This article will guide you through effective ways to

Weekly Update 459
New week, different end of the world! After a fleeting stop at home, we're in Japan for a proper holiday (yet somehow I'm still here writing this…) with the first stop in Tokyo. It's like nowhere else here, and this is now probably my 10th trip to Japan over a period of more than three










