
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

When the Grid Gets Smart, the…
Hello Cyber Builders 🖖 This is the third and final post in my series on cybersecurity and power grids. Today, I want to explore one of the most underestimated threats: the rise of new, hyper-connected grids and how that’s creating opportunities for attacks through devices you’d never expect. The first two posts explained the basics:
when you don’t respond to a…
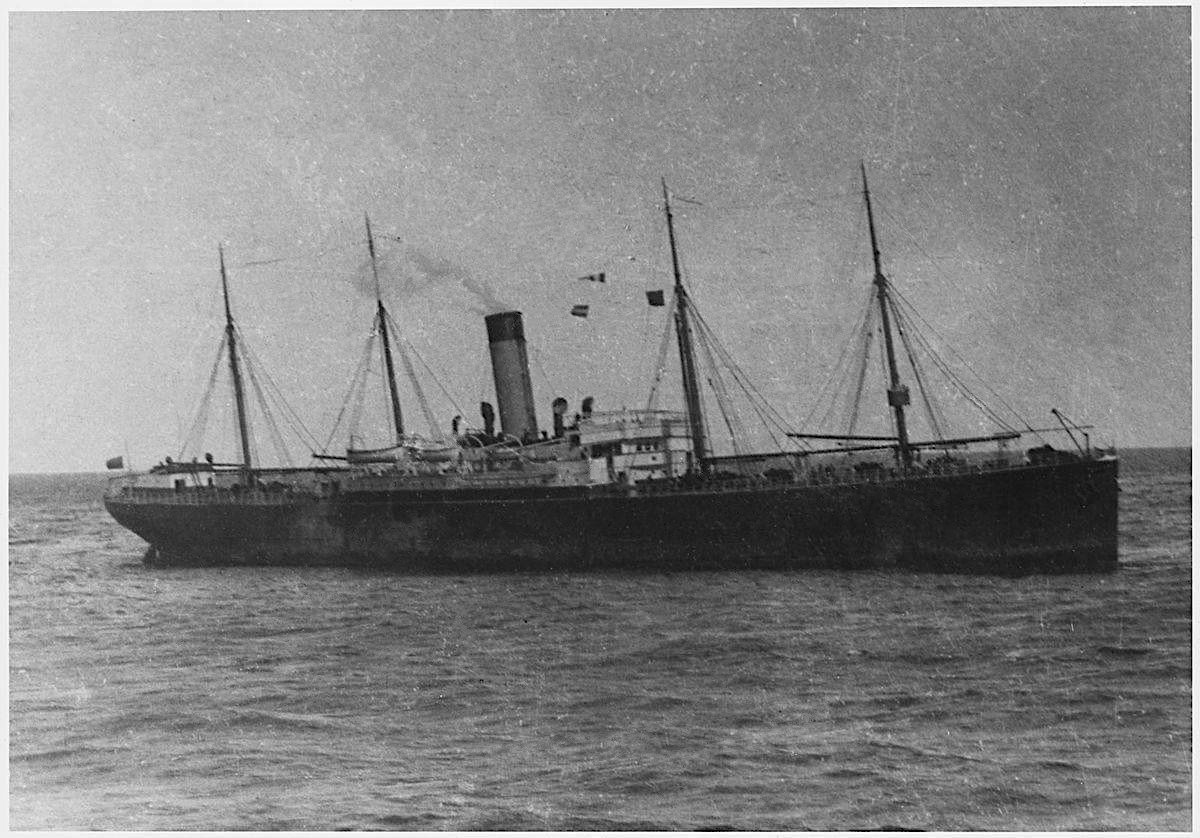
A few years ago I wrote a short article about the Titanic, and the lessons for cyber risk management. However, there’s arguably a far more interesting part to that story. When the RMS Titanic hit an iceberg on 15 April 1912, she set off flares and her wireless operator sent out a distress call. The

Cybercrime crackdown disrupts malware, infostealers, marketplaces…
As spring gives way to summer, a wave of cybercrime crackdowns has taken root, with law enforcement and private security companies directing a surge of takedowns, seizures, indictments and arrests. Prolific infostealers, malware loaders, counter antivirus and crypting services, cybercrime marketplaces, ransomware infrastructure and DDoS-for-hire operations have all been seized, taken offline or severely disrupted
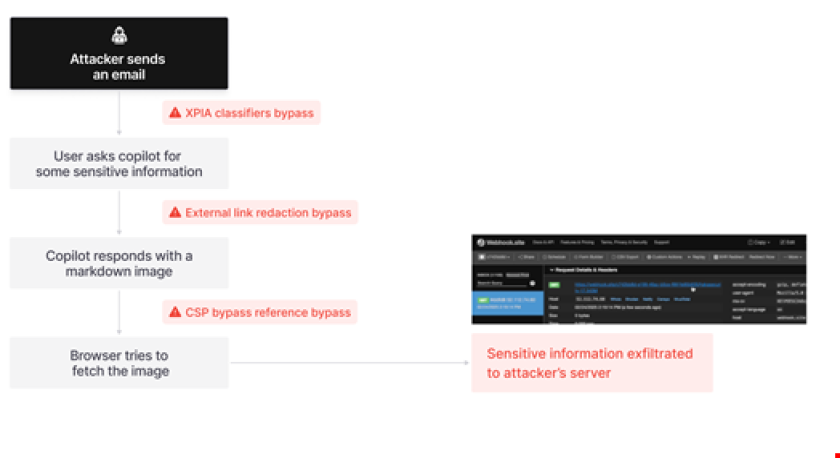
The New Reality of GenAI-Driven Attacks
Just a few years ago, several cybersecurity reports proclaimed that there was minimal evidence that bad actors were using generative AI tools to launch new or more sophisticated cyber attacks. Indeed, statements were commonly made that highlighted the safeguards and guardrails that were being put in place to stop Internet-facing GenAI tools from inappropriate use

SIEM Best Practices for 2025: Optimizing…
As businesses face an increasing number of cyber threats and stricter security regulations, ensuring robust cybersecurity has never been more critical. Security Information and Event Management (SIEM) systems are pivotal for organizations aiming to monitor and respond to potential security incidents. SIEM helps businesses gain better visibility into their IT infrastructure, detect threats in real-time,

Easily Share Large CAD Files with…
Designers, engineers, architects, and manufacturers need to share CAD files to get their jobs done — whether internally across teams, or externally with clients and supply chain partners. When it comes to proprietary designs, it’s vital to ensure those files are handled securely. With projects becoming increasingly complex and teams more distributed, finding the best way

Big Tech’s Mixed Response to U.S….
In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual currency investment scam websites reported to the FBI. But a new report finds the accused continues to operate a slew of established accounts at American tech companies — including Facebook, Github, PayPal and Twitter/X.

UnderDefense Secures Top Honor at the…
We’re proud of being a winner at the 2025 Global Infosec Awards for MDR Service, recognizing our commitment to advancing cybersecurity innovation and delivering industry-leading protection. At the RSAC Conference 2025, Cyber Defense Magazine revealed the recipients of its 13th Annual Information Security Awards. After a six-month evaluation of more than 3,000 security vendors worldwide,

Using AI to Write Deterministic Code…
Avoid blanket statements — use the right tool for the job ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code. 🔒 Related Stories: Cybersecurity | Penetration Tests 💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Using the right tool for the job In the
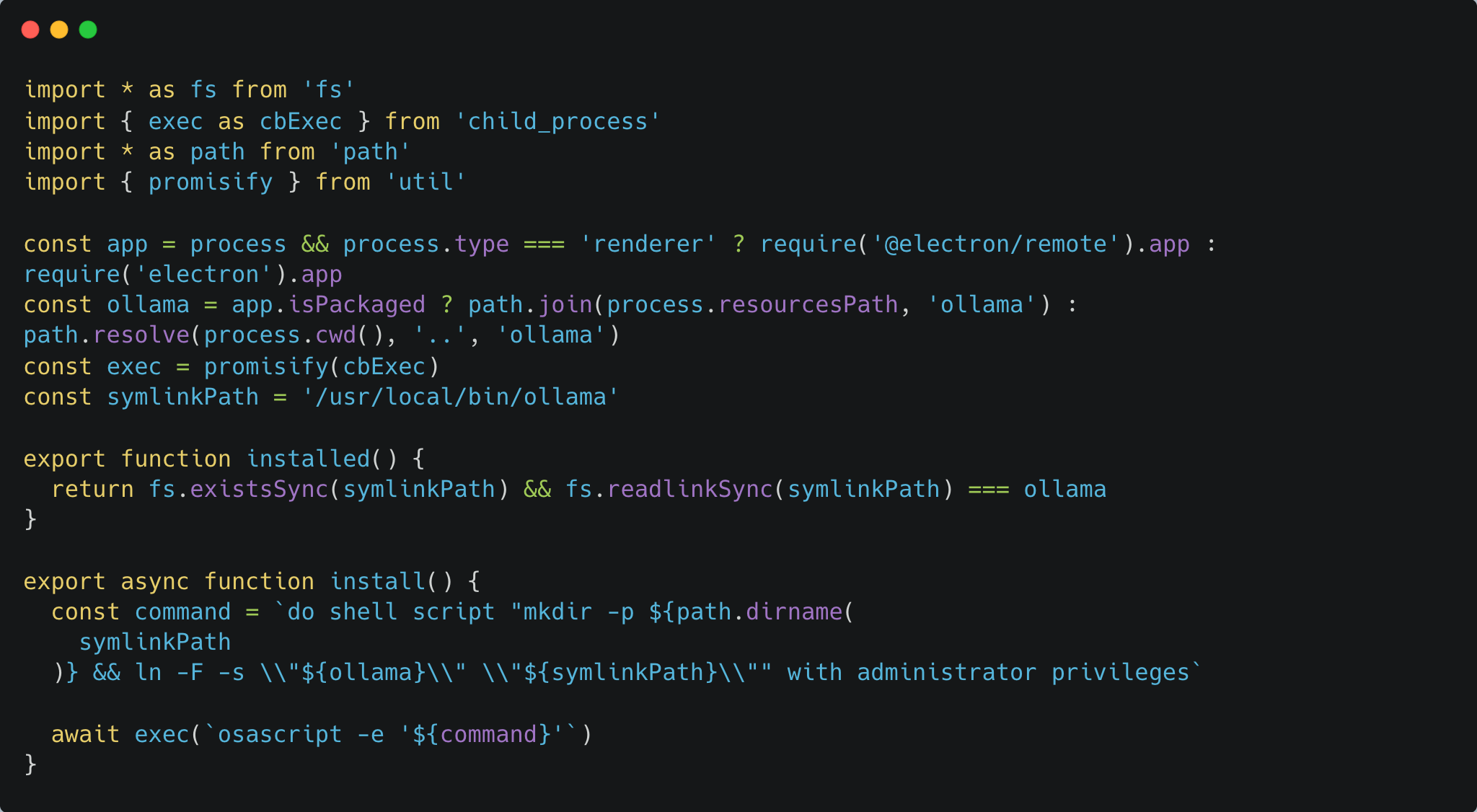
Hijacking Ollama’s Signed Installer for Code…
This blog post is part of an ongoing series exploring how AI related tools aimed at developers can be exploited to compromise their machines. As these tools increasingly integrate deep system access, they also expand the attack surface available to threat actors. In our first post, we outlined a remote code execution vulnerability in Cursor.










