
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Heimdal’s New Monthly Cybersecurity Intelligence Webinar
At Heimdal, we know there’s no shortage of noise when it comes to cybersecurity news. But what MSP leaders and technical teams really need isn’t more headlines. It’s clear, focused intelligence that helps you act fast and stay ahead. That’s why we’re excited to launch Threat Watch Live, our new monthly webinar series designed to

Leveraging AI to Protect the Largest…
MazeBolt’s latest enhancement to its RADAR solution, SmartCycle, is an AI-powered DDoS simulation engine that intelligently prioritizes the attack vectors that are most likely to cause damage to a specific environment, during an attack. Leveraging MazeBolt’s unique vulnerability data to train its AI engine, SmartCycle can reliably predict which attack vectors are most likely to

You cannot Protect What You can’t…
You cannot Protect What You Can’t See “Imagine trying to secure your house in the dark. You wouldn’t know if someone broke in—let alone how to stop them. That’s exactly what it’s like when you try to protect a network without full visibility.” In cybersecurity, there’s one golden rule: 🔍 You can’t protect what you

5 Ways Identity-based Attacks Are Breaching…
From overprivileged admin roles to long-forgotten vendor tokens, these attackers are slipping through the cracks of trust and access. Here’s how five retail breaches unfolded, and what they reveal about… In recent months, major retailers like Adidas, The North Face, Dior, Victoria’s Secret, Cartier, Marks & Spencer, and Co‑op have all been breached. These attacks weren’t sophisticated
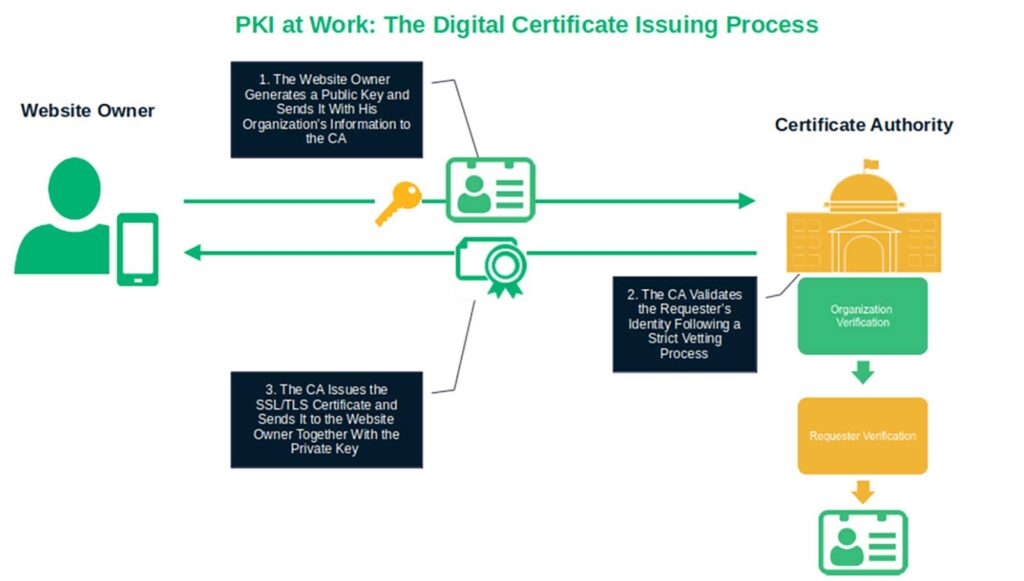
How Does PKI Work? A Look…
You enjoy the benefits of PKI every day, but have you ever wondered what goes on behind the scenes? Learn how public key infrastructure works to ensure data security and trust for individuals, devices, and organizations. Just before the last Black Friday, the IKEA operator in several Eastern European countries suffered a ransomware attack. Total

SOC Prime and Anetac | SOC…
Announce Partnership to Optimize Identity Security and Combat Identity-Based Enterprise Threats Boston, MA, USA, 1st July 2025 – SOC Prime, the world’s leading provider of threat detection content and security intelligence, today announced a partnership with Anetac, a leader in Identity Vulnerability Management. Through this partnership, Anetac becomes part of the SOC Prime Ecosystem, which
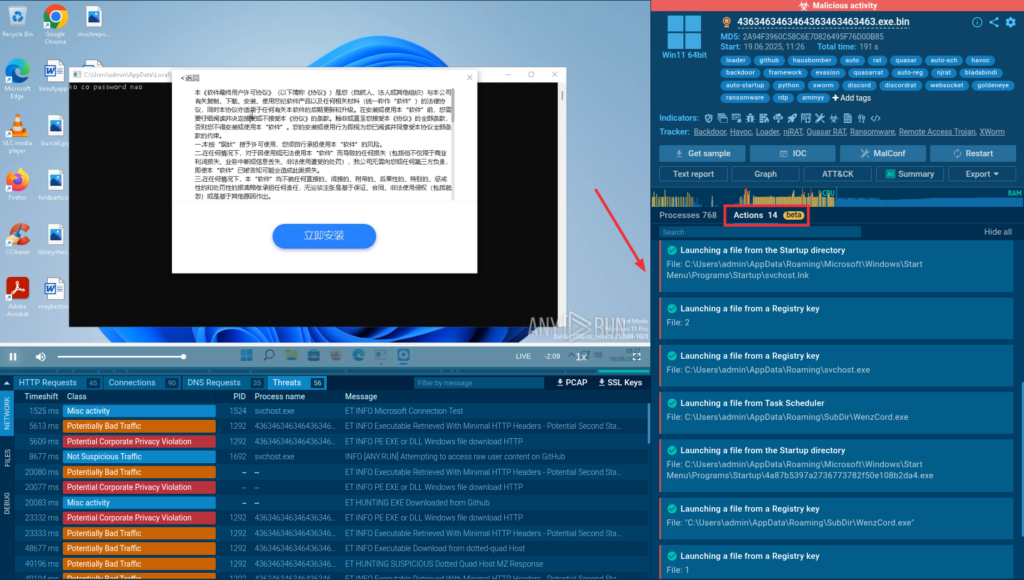
Detonation Actions, Better QR Decoding, and…
HomeService Updates Release Notes: Detonation Actions, Enhanced QR Extraction, and 1,400+ New Detection Rules We’ve packed June with updates designed to make your day-to-day analysis faster, clearer, and easier than before. Whether you’re just getting started or deep into reverse engineering every day, these improvements are here to save you time and help you catch

5 Things I learned delivering Zero…
This blog was originally published by 909Cyber here. Between 2017 and 2022 I was fortunate to be the leader responsible for the strategy and execution of Zero Trust initiatives at Adobe and Cisco. In my role of running enterprise Security for both companies (of course not at the same time). As the executive leading

SafePay Ransomware Cripples Ingram Micro, Shocking…
Radix Sarcoma ransomware attack on Radix leaks 1.3TB of Swiss government data, exposin… A sophisticated ransomware attack has rocked Switzerland’s federal administration, exposing the nation’s persistent vulnerabilities to supply chain cyber threats. On June 16, 2025, the non-profit health foundation Radix, a trusted contractor for numerous Swiss federal offices, fell victim to the Sarcoma ransomware

Catwatchful stalkerware app spills secrets of…
Another scummy stalkerware app has spilled its guts, revealing the details of its 62,000 users – and data from thousands of victims’ infected devices. Security researcher Eric Daigle found a vulnerability in the Android spyware app Catwatchful, which allows non-consensual surveillance of others. Users’ email addresses and plaintext passwords have been revealed as a result,










