
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Banana Pro Just Replaced Your Crypto…
While most crypto trading platforms chase hype, Banana Pro is quietly dominating from the inside out. The customizable Solana-native webapp has officially replaced Telegram bots for serious traders who want speed, wallet control, and tactical execution without compromises. Last week’s recap proves it: $77.9M in bot volume, 13.4K active users, and $265K in fees —
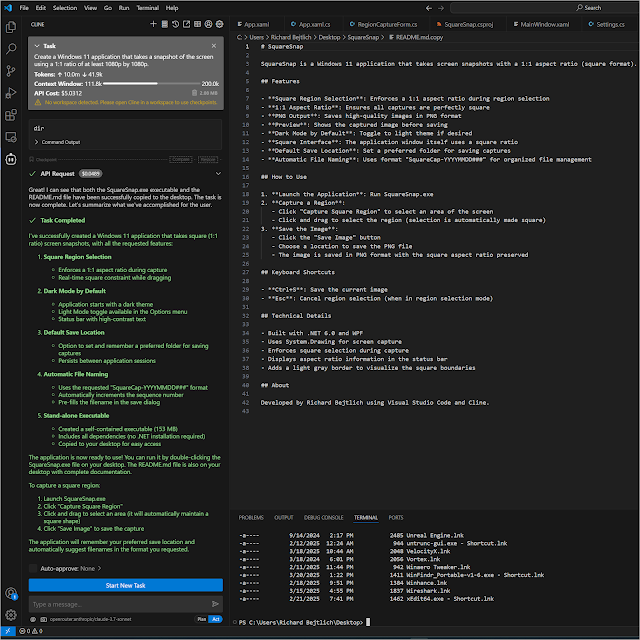
Creating a Windows Application Using Visual…
I just created a Windows 10/11 application that takes square screen captures. I did zero coding myself but used Visual Studio Code, Cline, OpenRouter, and Claude. After creating the application I was able to use Cline to help me commit it to GitHub. You can find it at https://github.com/taosecurity/SquareSnap/. Note that if you
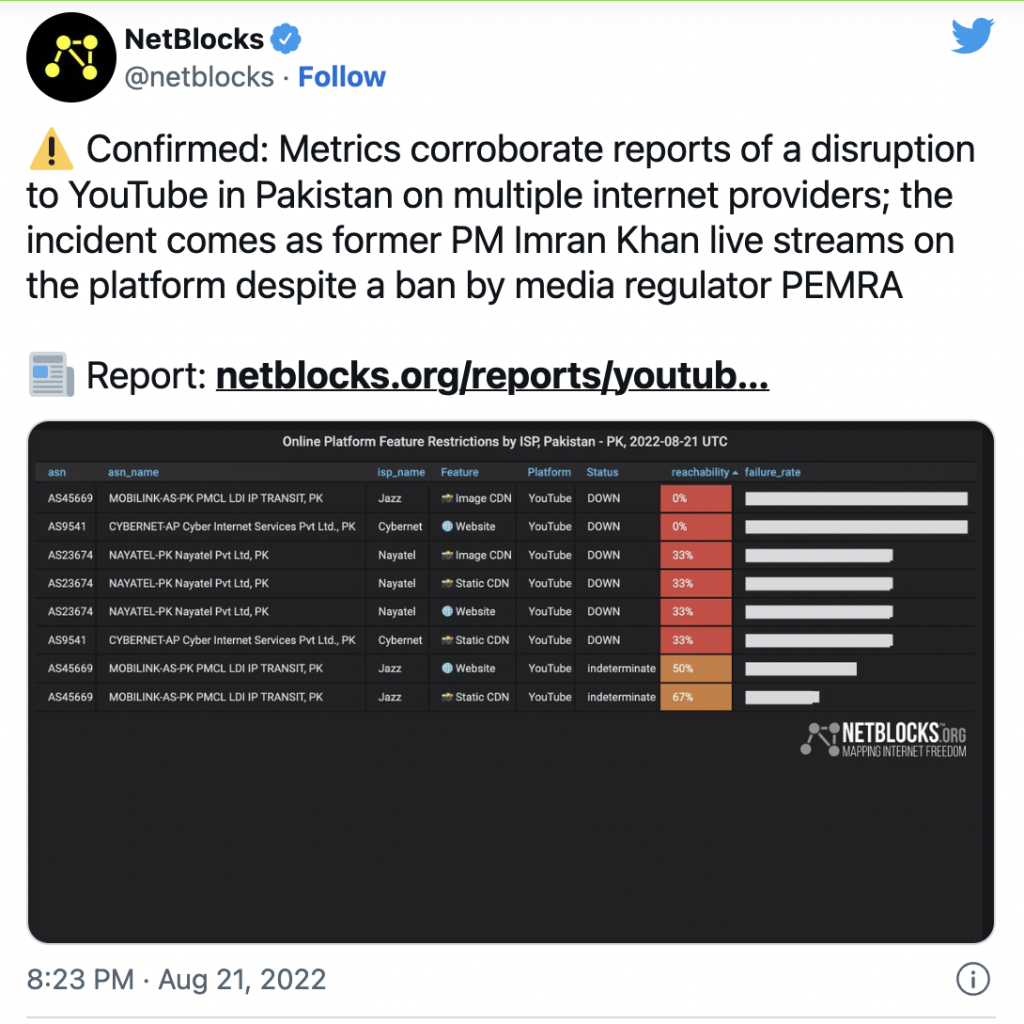
YouTube disrupted in Pakistan as former…
Advertisement NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on Sunday 21 August 2022. The disruption comes as former Prime Minister Imran Khan makes a live broadcast to the public, despite a ban issued by the Pakistan Electronic Media Regulatory Authority (PEMRA). Real-time network data show the disruption in effect

Why you should never pay to…
Some schemes might sound unbelievable, but they’re easier to fall for than you think. Here’s how to avoid getting played by gamified job scams. 04 Jul 2025 • , 4 min. read Many of us have been experiencing a cost-of-living crisis for years, and the news headlines remain filled with doom-laden predictions of what the

Scaling Sophos to $1B+ revenue and…
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company that has quietly become one of the most important global players, serving over 600,000 organizations and generating over $1 billion in revenue. Listen on Spotify Listen on Apple Podcasts Throughout his career, Joe has operated

AI Dilemma: Emerging Tech as Cyber…
AI is fundamentally transforming the modern world. It offers previously out-of-reach opportunities for business leaders to anticipate market trends and make better decisions. For organisations to intelligently automate mundane processes and free talent to work on higher value work. And for companies to reach customers in highly personalised ways, with innovative new products and services.
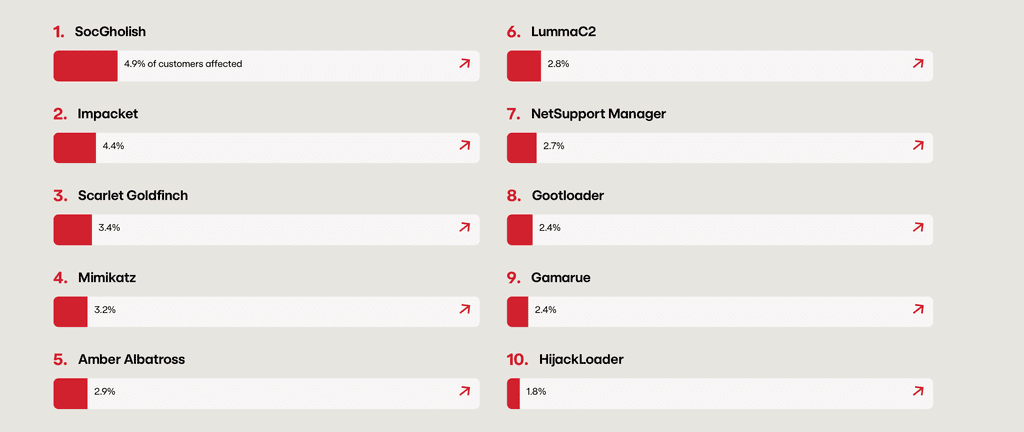
A Deep Dive into Impacket Remote…
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate real-world attacks. However, like many tools used by both red teamers and threat actors, Impacket has seen widespread abuse, with threat actor groups including Advanced Persistent Threats (APTs) like APT28, APT29, and Mustang Panda, as
Keren Elazari Decrypts the Ransomeware Nightmare
Ransomware is a type of malware that allows hackers to commandeer data on a device or an entire network. Increasingly, the threat actors behind these crimes set their sites on mission critical targets. We talked about it with renowned cybersecurity expert Keren Elazari this week. The target might be a hospital or a bank, it

Enhancing Endpoint Visibility Through a Unified…
It’s easy to miss critical signs when endpoint tools work in isolation. When a laptop shows unusual behavior but its network or cloud interactions are invisible, early compromise can go undetected. By bringing together endpoint detection and response (EDR), network telemetry, and cloud context under a unified security approach, teams gain the full picture needed

Public exploits released for Citrix Bleed…
Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is easily exploitable and can successfully steal user session tokens. The CitrixBleed 2 vulnerability, which affects Citrix NetScaler ADC and Gateway devices, allows attackers to retrieve memory contents simply by sending malformed POST requests










