
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
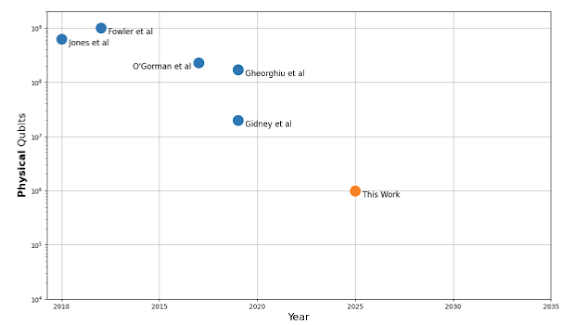
Tracking the Cost of Quantum Factoring
Google Quantum AI’s mission is to build best in class quantum computing for otherwise unsolvable problems. For decades the quantum and security communities have also known that large-scale quantum computers will at some point in the future likely be able to break many of today’s secure public key cryptography algorithms, such as Rivest–Shamir–Adleman (RSA). Google

Minimize Cybersecurity Threats by Making Smart…
Hosting is critical in defending websites from modern cyber threats, yet it’s often overlooked in basic security strategies. Different types of hosting offer varying levels of protection, with dedicated and VPS hosting typically offering stronger isolation. Evaluating provider transparency, support quality, and built-in security tools is key to making a smart, long-term hosting decision. Avoid

ClickFix-Attacken bedrohen Unternehmenssicherheit
Cyberkriminelle greifen immer häufiger auf ClickFix-Angriffe zurück. NAJA x -shutterstock.com Weniger bekannt als Phishing ist die Social-Engineering-Methode ClickFix. Ziel solcher Attacken ist es, die Opfer dazu zu bewegen, bösartige Befehle in Tools wie PowerShell oder die Windows-Eingabeaufforderung einzufügen. Die Angriffe beginnen in der Regel, nachdem ein Benutzer eine kompromittierte oder bösartige Website besucht oder einen
Best SOC as a Service Providers…
When cyber threats strike from every corner of your infrastructure, turning to experienced SOC as a service providers equips your business with the full strength and expertise of a Security Operations Center (SOC). With these external experts by your side, you benefit from all the critical SOCaaS services—like 24/7 security monitoring, threat detection, and incident
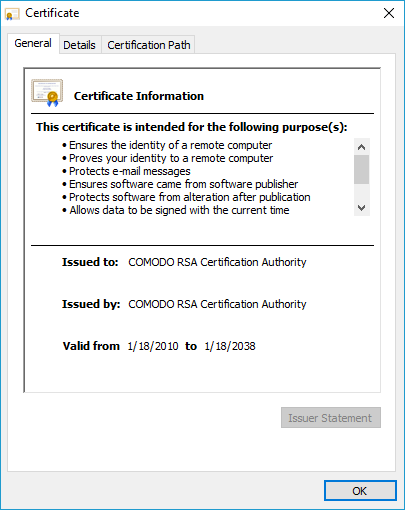
Comodo RSA Certification Authority: Trusted Root…
The COMODO RSA Certification Authority is one of the most widely distributed root CAs in the world. Its certificates form the foundation of security for millions of websites, applications, and digital services. But what makes COMODO RSA Certification Authority one of the most trusted names in web security? Let’s explore. Overview of Comodo RSA Certification
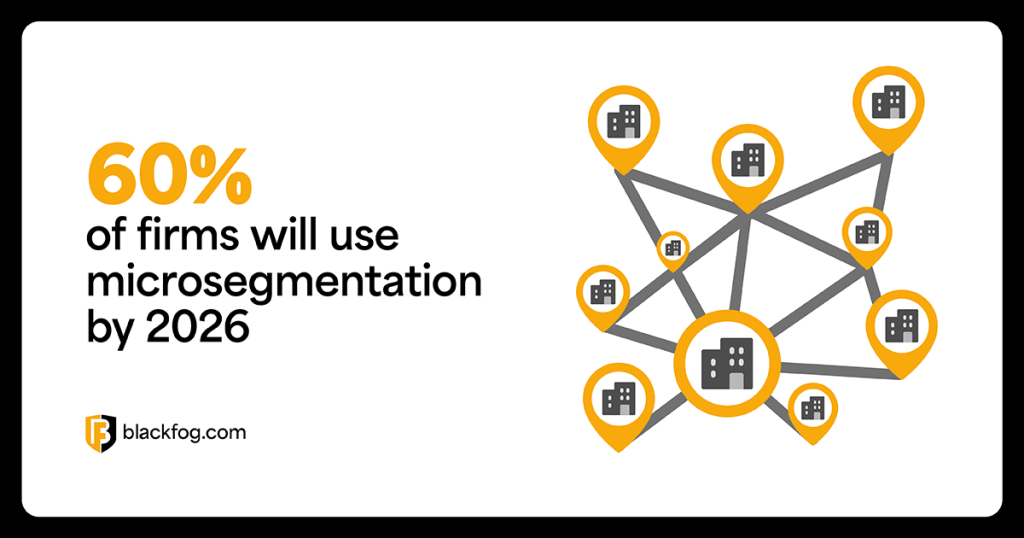
Microsegmentation: Strengthening Network Security Against Zero…
Microsegmentation: Strengthening Network Security Against Zero Day Exploits The challenge of how businesses respond to an ever-evolving cybersecurity landscape is a complex one. Threats like zero day exploits make it easier for cybercriminals to breach defenses and access sensitive data, leading to costly ransomware incidents. These vulnerabilities are especially hard to manage as networks expand

PDPA Compliance Checklist for Singapore Businesses…
A Practical Blueprint for PDPA Compliance The Personal Data Protection Act (PDPA) is not just a legal formality — it’s a core requirement for doing business in Singapore. Whether you’re a startup, a SME, or a large organization, your customers expect you to take their data seriously. However, figuring out how to comply with PDPA
Welcoming Truyu to Have I Been…
I always used to joke that when people used Have I Been Pwned (HIBP), we effectively said “Oh no – you’ve been pwned! Uh, good luck!” and left it at that. That was fine when it was a pet project used by people who live in a similar world to me, but it didn’t do

Small Businesses Create Big Impact: NIST…
This week we’re celebrating National Small Business Week—which recognizes and celebrates the small and medium-sized business (SMB) community’s significant contributions to the nation. SMBs are a substantial and critical part of the U.S. and global economic and cybersecurity infrastructure. According to the U.S. Small Business Administration’s Office of Advocacy,[1] there are 34.8 million SMBs in the
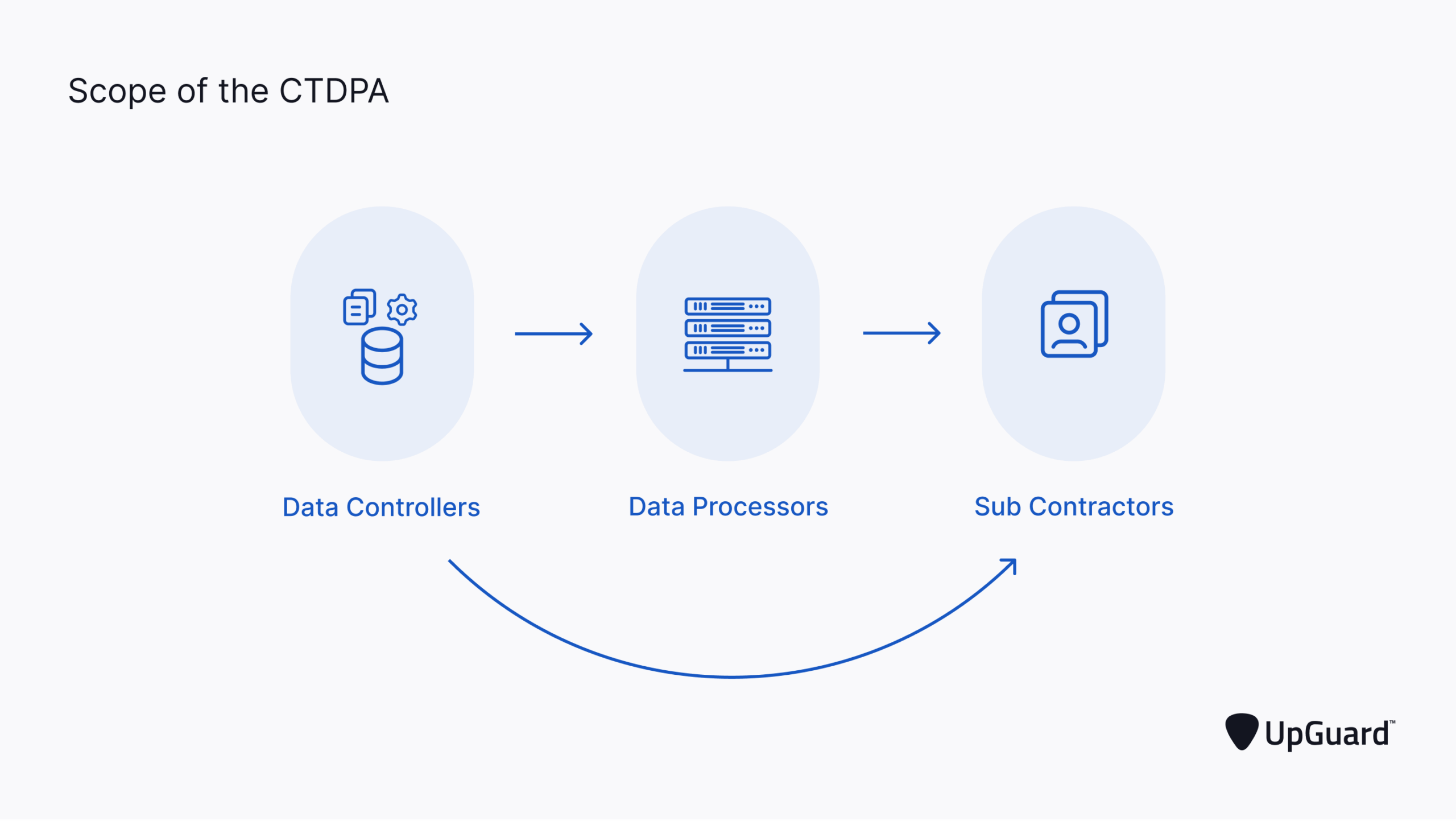
What is the Connecticut Data Privacy…
The Connecticut State Government signed the Connecticut Data Privacy Act (CTDPA) into law on May 10, 2022, and the law became effective on July 1, 2023. The CTDPA joins the ranks of other US state privacy laws, like the California Consumer Privacy Act (CCPA) and the Colorado Privacy Act, providing Connecticut consumers with robust data










