
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Using 2nd Sight Lab’s aws-deploy to…
Steps to deploy all the things — and summary of how I used AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code. 🔒 Related Stories: Cybersecurity | Penetration Tests 💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ I created a tool simply called

Top 10 Dynamic Application Security Testing…
What is DAST and how does it work? Dynamic application security testing (DAST) is a cybersecurity assessment method that analyzes running applications to identify security vulnerabilities. Unlike static application security testing (SAST), which examines source code before deployment, DAST scanning simulates real-world attacks by probing a web app’s inputs and responses. The term DAST is
Addressing Our ‘Age of Insecurity’ —…
In her award-winning book The Age of Insecurity: Coming Together as Things Fall Apart, Astra Taylor makes the argument that everyone feels insecure. The book’s description discusses our cultural challenges this way: “We are financially stressed and emotionally overwhelmed. The status quo isn’t working for anyone, even those who appear to have it all. What
Integrating SIEM Threat Intelligence for Better…
In today’s cybersecurity environment, businesses face increasingly sophisticated threats that evolve quickly and often bypass traditional defenses. As such, having an effective security strategy in place is no longer just an option—it’s a necessity. One of the most powerful tools for achieving better threat detection is combining Security Information and Event Management (SIEM) with threat

Why Storage Providers Can’t Ignore Cyber…
With the advent of newer technologies, storage providers have increasingly had to rely on digital means for dealing with data, customer information, and administration. This had several benefits but brought with it new perils, mainly in the guise of cyber dangers that can pilfer confidential information and take services offline.

Senator Chides FBI for Weak Advice…
Agents with the Federal Bureau of Investigation (FBI) briefed Capitol Hill staff recently on hardening the security of their mobile devices, after a contacts list stolen from the personal phone of the White House Chief of Staff Susie Wiles was reportedly used to fuel a series of text messages and phone calls impersonating her to

Why Nation-States Are Hacking the Power…
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖, In Part 1 of this series, I shared my personal experience during the Spanish blackout and explored past grid-targeting attacks, including Ukraine 2015. But today’s story goes deeper. It’s not just about outages. It’s about
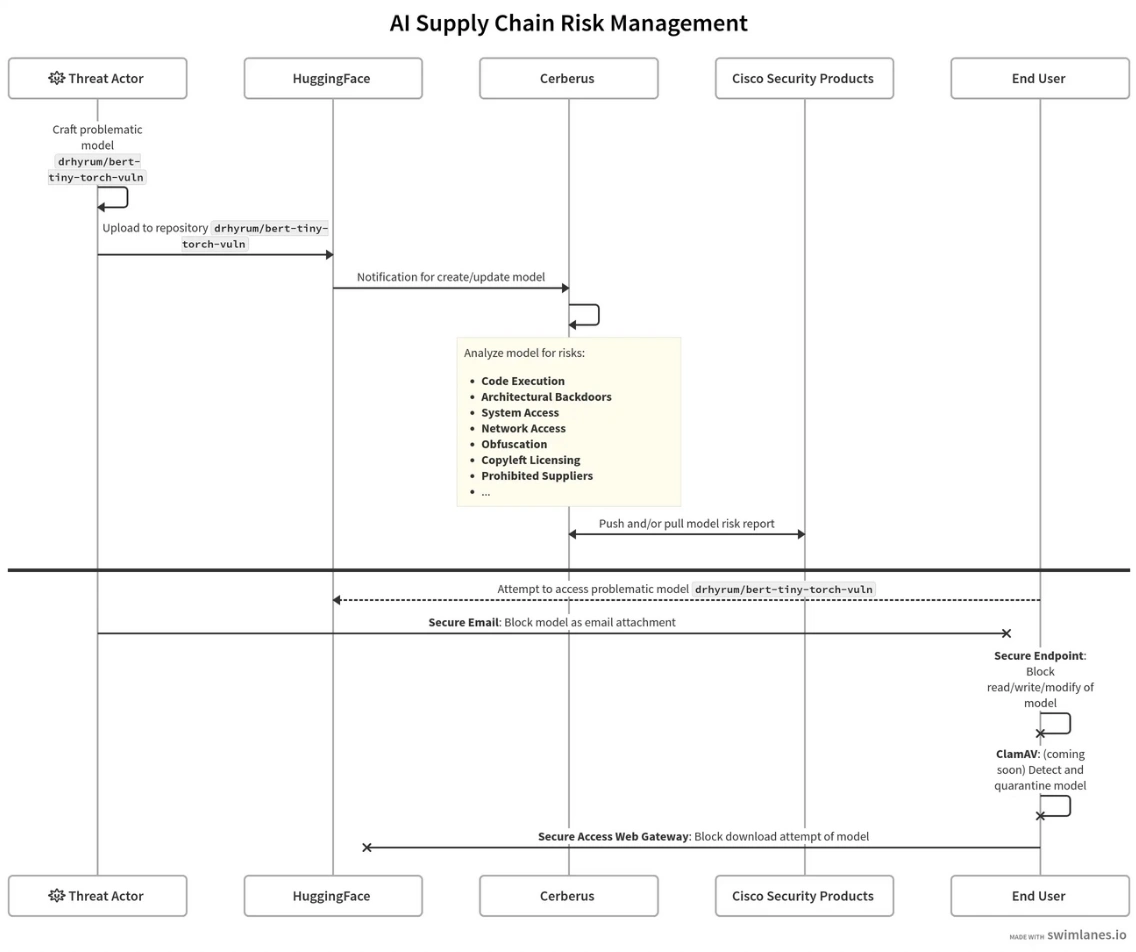
Securing an Exponentially Growing (AI) Supply…
The global AI race is in full swing, and its battleground? HuggingFace It took eight years for the platform to reach 1 million models, but only 9 months later, this figure will likely double (1.8 million at the time of writing). Model providers of all origins – public and private, domestic and foreign, trusted and
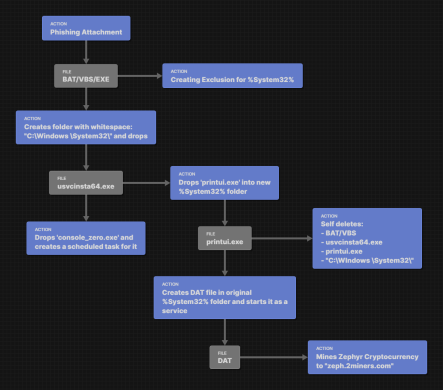
Hijacking Your Resources for Profit
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems, validating transactions on a blockchain network and earning cryptocurrency coins. This activity has gained popularity with the increasing value of digital currencies, leading some malicious actors to exploit users’ devices for their own gain. Cybercriminals
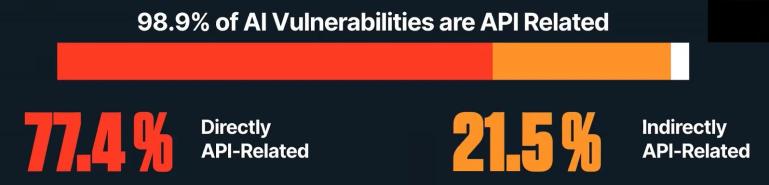
The Rise of AI-Driven API Vulnerabilities
AI has had dramatic impacts on almost every facet of every industry. API security is no exception. Up until recently, defending APIs meant guarding against well-understood threats. But as AI proliferates, automated adversaries, AI-crafted exploits, and business logic abuse have complicated matters. It’s no longer enough to merely patch known flaws; security teams must now










