
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Apple Alert: Critical AirPlay Vulnerabilities Expose…
A recent discovery by cybersecurity firm Oligo Security has unveiled a series of critical vulnerabilities in Apple’s AirPlay protocol and SDK, collectively termed “AirBorne.” These flaws pose significant risks to a vast array of devices, including iPhones, iPads, Macs, Apple TVs, and numerous third-party gadgets like smart speakers, TVs, and CarPlay systems. Understanding the Threat

Is Your Network Configured to Prevent…
Many enterprises allocate significant resources to prevent damaging DDoS attacks – only to discover that critical gaps still exist. MazeBolt’s latest eBook explores some of the different aspects of network configuration that can leave organizations highly exposed to damaging downtime – even if they have premium DDoS protections deployed. One example of a network configuration
Ad-Hoc Encrypted File Sharing for Teams,…
We have so many business apps for sharing information: Email, Slack, Teams, Google Drive, SharePoint. But when it comes to securely sharing large files outside your organization, each of these applications can fall short due to size and sharing limitations.
Malicious Pull Request Targets 6,000+ Developers…
Cybersecurity researchers have flagged a supply chain attack targeting a Microsoft Visual Studio Code (VS Code) extension called Ethcode that has been installed a little over 6,000 times. The compromise, per ReversingLabs, occurred via a GitHub pull request that was opened by a user named Airez299 on June 17, 2025. First released by 7finney in

How to Achieve DDoS Defense with…
DDoS Defense with up-to-the-minute network analysis has become crucial as these attacks have disrupted network security for almost 20 years. The landscape changed dramatically in 2018 when the first multi-terabyte per second DDoS attacks crippled major organizations. GitHub experienced a massive 1.3TB/s attack that year, which dwarfed the previous record – a 602GB/s attack on

Introducing Guernsey Cyber Security Centre —…
Since 2021, I’ve been building Jersey Cyber Security Centre (JCSC). As a cyber defence capability for an island state and leading International Finance Centre, we’re a small team with a big task. We’re also just one of hundreds: teams in countries from all around the world, all united by a mission to defend people and
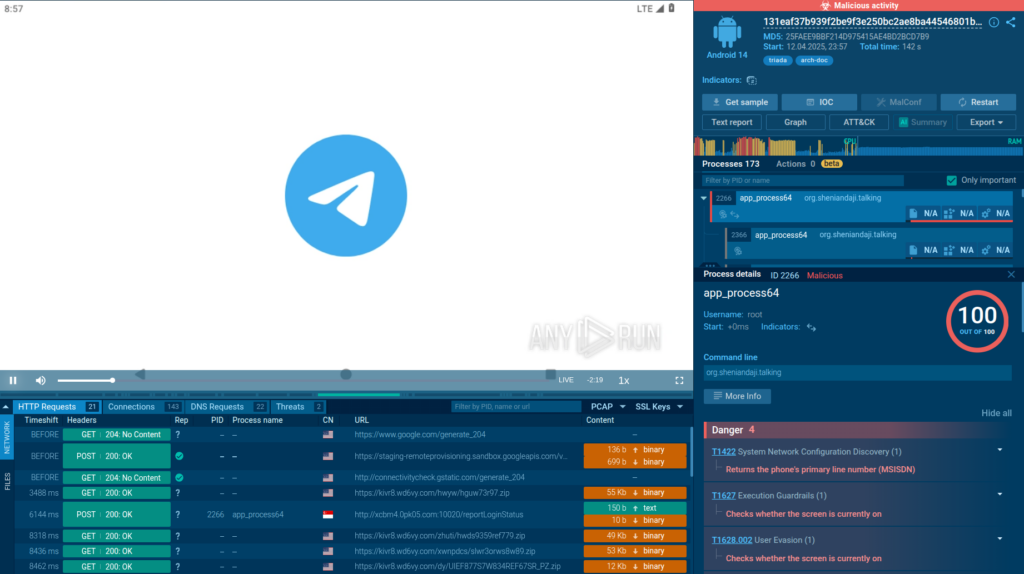
Packer of Triada Android Malware
HomeMalware Analysis Technical Analysis of Ducex: Packer of Triada Android Malware Many have probably heard of the modular malware for mobile devices called Triada. Even nine years after its first mention in 2016, it remains one of the most advanced Android trojans out there. Recently, our team at ANY.RUN came across an interesting sample of

Why Identity Automation Fails at 96%…
This blog was originally published by Cerby here. Enterprise security teams have invested billions in identity security infrastructure over the past decade, building sophisticated systems to manage access and monitor risk. But when it comes to executing identity processes and decisions, our latest research reveals that 96% of organizations still rely on manual workflows.

HIPAA Just Got Tougher—Here’s How Small…
Securing Patient Data: New HIPAA rules explained for Small Clinics in 2025 Electronic records have changed the face of healthcare. For patients, they mean faster service, better coordination, and safer treatment. For doctors and nurses, they simplify charting and make it easier to track progress. For clinics, they help manage patient care more efficiently while
An AI runs a shop into…
In episode 58 of “The AI Fix” podcast, our hosts discover a pair of AI headphones that don’t electrocute you, Microsoft invents “medical superintelligence”, Chucky opens a hotel, some robot footballers fall over, Jony Ive invents a $6 billion pen, and Malcolm Gladwell fears a dystopian future full of children playing joyfully in the street.










