
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
How government cyber cuts will affect…
Deep cuts in cybersecurity spending risk creating ripple effects that will put many organizations at a higher risk of falling victim to cyberattacks 03 Jul 2025 • , 4 min. read We often hear about cybersecurity fatigue, the mental and emotional strain that weighs on individuals and teams on the frontlines and leads to decreased

Android malware Anatsa infiltrates Google Play…
The Anatsa banking trojan has sneaked into Google Play once more via an app posing as a PDF viewer that counted more than 50,000 downloads. The malware becomes active on the device immediately after installing the app, tracking users launching North American banking apps and serving them an overlay that allows accessing the account, keylogging, or automating transactions. According

Password Spraying Attacks Hit Entra ID…
Identity & Access Management , Security Operations Hackers Use TeamFiltration Penetration Testing Tool Prajeet Nair (@prajeetspeaks) • June 12, 2025 Image: Shutterstock A threat actor is using the password spraying feature of the TeamFiltration pentesting tool to launch attacks against Microsoft Entra accounts – and finding success. See Also: Proof of Concept: Rethinking

How OAuth and device code flows…
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and OAuth application abuse. These methods allow attackers to exploit legitimate sign-in flows to steal authentication tokens, often without needing passwords or triggering MFA. This blog focuses specifically on Entra ID token abuse: how adversaries steal

News alert: Halo Security’s attack surface…
Miami, June 18, 2025, CyberNewswire — Halo Security today announced that its attack surface management solution has been named a 2025 MSP Today Product of the Year Award winner by TMC, a leading global media company recognized for building communities in technology and business through live events and digital marketing platforms. The MSP Today Product

Citrix Patch Chaos NetScaler Update Breaks…
Ingram Safepay SafePay ransomware cripples Ingram Micro’s global operations, disrupting IT supp… The technology distribution giant Ingram Micro confirmed on July 6, 2025, that it had fallen victim to a sophisticated ransomware attack by the rapidly emerging SafePay cybercriminal group, marking one of the most significant supply chain disruptions in the IT industry this year.
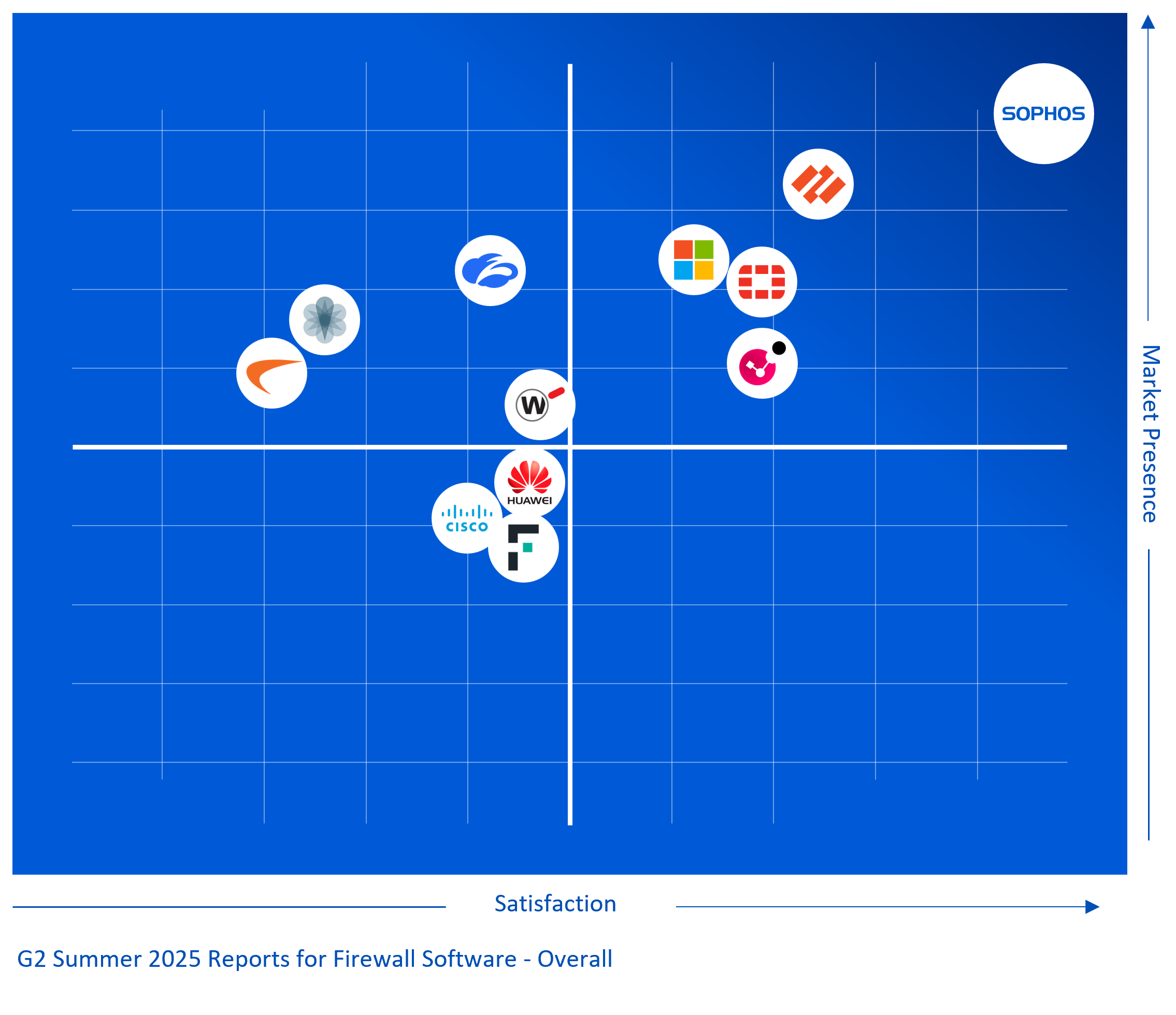
Sophos Firewall Recognized as the #1…
Customers have spoken, and the results are in. G2, a major technology user review platform, has just released their Summer 2025 Reports, where Sophos Firewall was rated the #1 Firewall in the Overall Firewall Grid. This marks the 10th consecutive G2 Seasonal Report where Sophos Firewall is the top-ranked Firewall, dating back to G2’s Spring

10 immutable laws of security, 25…
Back in 2000, the Microsoft Security Response Center released an article titled “10 Immutable Laws of Security“, describing what they believed were some fundamental truths about security, human behavior, and technology operations. Years later, they also released a V2 of this article, which remains relevant to this day. In this piece, I am looking at
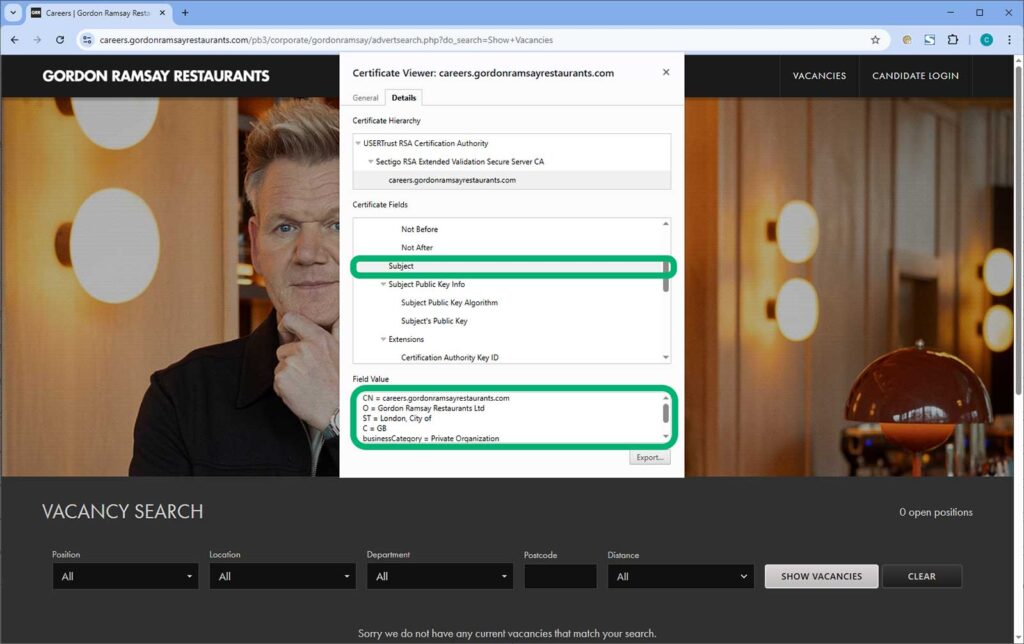
8 Practical PKI Uses & Applications…
More than half of the breaches investigated by Verizon in its 2025 DBIR report stemmed from system intrusions. Discover which PKI use cases every small and mid-size business can implement to minimize these risks (and others) In our previous article, we introduced you to public key infrastructure (PKI), a framework that enables organizations of all

Bridging the Security Knowledge Gap: Introducing…
The challenge of maintaining robust web application security often comes down to communication. Security teams frequently spend countless hours explaining WAF blocking decisions to application developers who may lack security expertise. This communication gap not only creates friction between teams but also consumes valuable time and resources that could be better spent elsewhere. Today, we’re










