
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
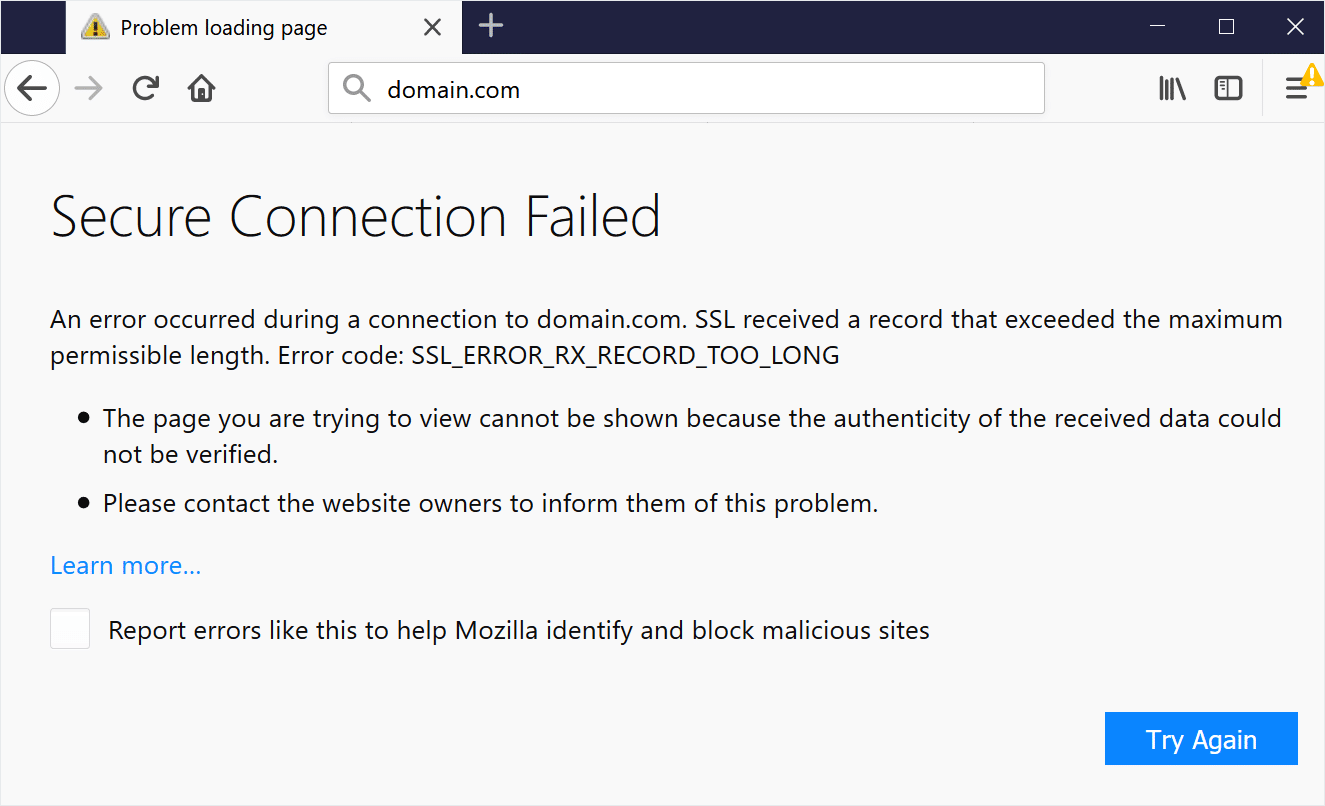
Fix SSL_ERROR_RX_RECORD_TOO_LONG in Firefox – Quick…
When Firefox throws up the error SSL_ERROR_RX_RECORD_TOO_LONG, it’s not just a random glitch. It’s Firefox’s way of protecting you when something’s off in the SSL/TLS connection between your browser and the website’s server. This error usually points to a deeper issue on the server side: misconfigured SSL/TLS settings, incorrect ports, or outdated encryption libraries. But

Patch Management: An Essential Part of…
Patch Management: An Essential Part of Data Security Outdated software is one of the biggest security risks facing modern businesses. It creates serious vulnerabilities that cybercriminals can exploit, leading to data breaches, ransomware attacks and other cybersecurity issues that can damage reputations and cause financial losses. To counter this, organizations need a comprehensive patch management
The Wild West of the Loophole…
We’ve all been there. You see something perfect online, you do all the clicks and then think, “Wait, was that legit?” Scam-lite transactions are the way of the web these days, whether it’s direct-from-manufacturer or super-sticky subscriptions, we have your back. In this episode we’re joined by consumer advocates Bob Sullivan, Gerri Detweiler, and Herb

Weekly Update 458
I'm in Austria! Well, I was in Austria, I'm now somewhere over the Aussie desert as I try and end this trip on top of my "to-do" list. The Have I Been Pwned Alpine Grand Tour was a great success with loads of time spent with govs, public meetups and users of this little data

G2 Spring 2025 Report Awards UnderDefense…
We’re proud to share exciting news! UnderDefense has been recognized as a trustworthy, first-rate cybersecurity service provider with 12 new badges from G2. They reflect what matters most to us — our clients’ trust, satisfaction, and robust protection. Every badge is grounded in the positive feedback from our customers and their confidence in our team.

How to Build an Effective Security…
Organizations invest in advanced tools to secure their assets, but humans are still the most persistent attack vector. Each year, this is reinforced by the overwhelming number of breaches that stem from human behaviour. Ultimately, employees are being asked to be hypervigilant all the time – despite their best efforts, everybody makes mistakes, and you
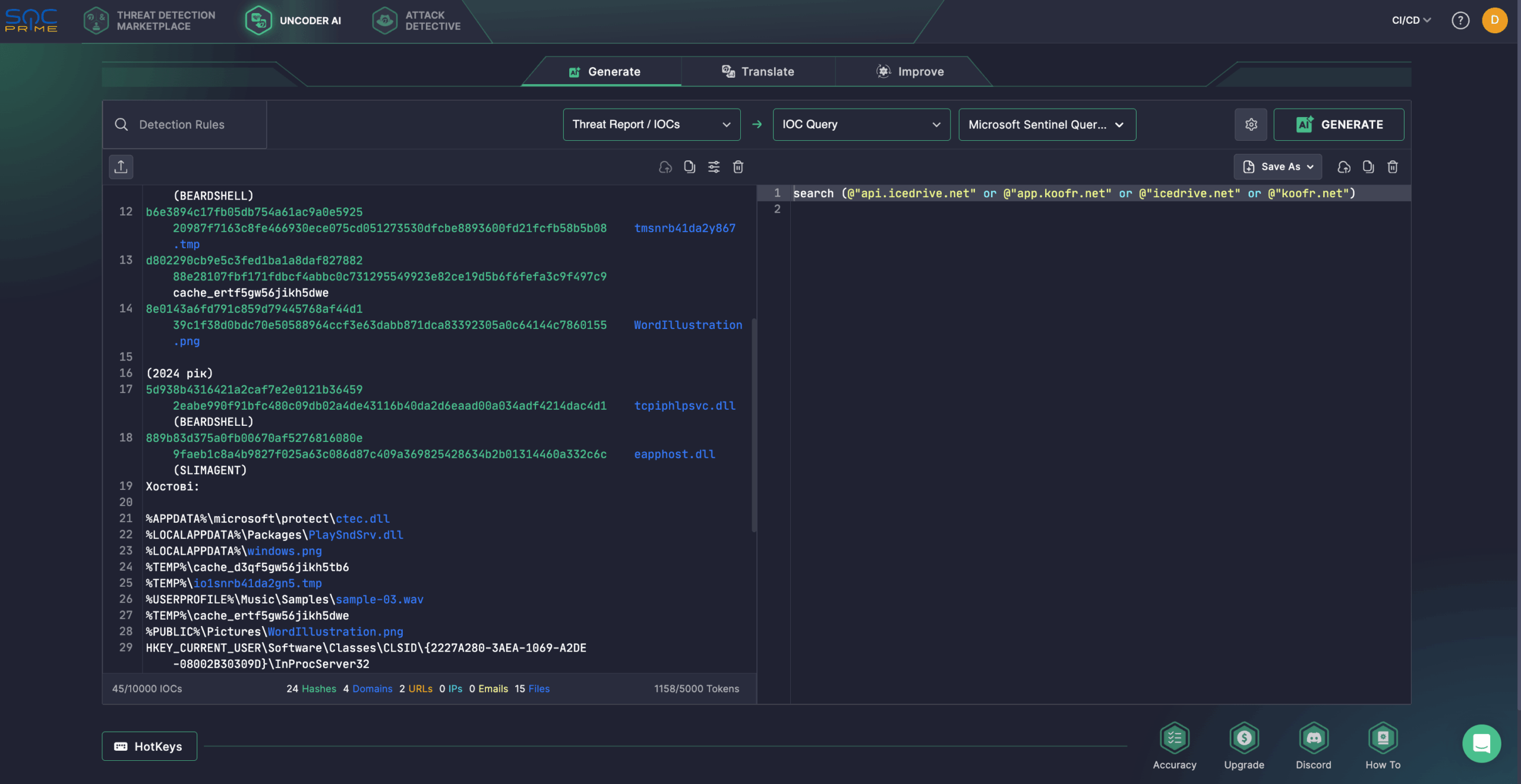
UAC-0001 (APT28) Activity Detection: The russian…
The nefarious nation-backed russian hacking collective known as UAC-0001 (aka APT28) reemerges in the cybersecurity spotlight. Over a year ago, in the spring of 2024, the CERT-UA team was investigating an incident targeting state executive bodies and identified a Windows-based server. In May 2025, ESET shared timely intelligence indicating unauthorized access to an email account
How To Record Your Screen Securely…
Learn how to record your screen securely with Recordit in this post. Screen recording has become an essential tool for professionals, educators, developers, and support teams. Whether you’re creating a software demo, reporting a bug, or recording a walkthrough for a colleague, screen recording offers a fast, visual way to communicate. However, recording and sharing

Happy 22nd Birthday TaoSecurity Blog
Happy birthday TaoSecurity Blog, born on this day in 2003! The best way to digest the key lessons from this site is to browse my four volume Best of TaoSecurity Blog book series, published in 2020. It’s available in print as seen here, or as a properly formatted HTML-based digital book — none of that

Mastering Windows Server 2025 – Book…
Mastering Windows Server 2025 For IT professionals and system administrators navigating the evolving landscape of server management, “Installing and Configuring Windows Server 2025: A practical guide to management and optimization of Windows Server environment” by Bekim Dauti emerges as a timely and valuable resource. This book, published by BPB Publications, offers a systematic and practical










