
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

What Are SWIFT Security Controls? Framework,…
SWIFT, the global backbone for secure financial messaging, plays a critical role in enabling fast and reliable cross-border transactions. But as cyber threats grow more advanced, financial institutions must implement robust SWIFT security controls to safeguard their systems and prevent fraud. The SWIFT Customer Security Programme (CSP) was established to enhance cybersecurity hygiene across its
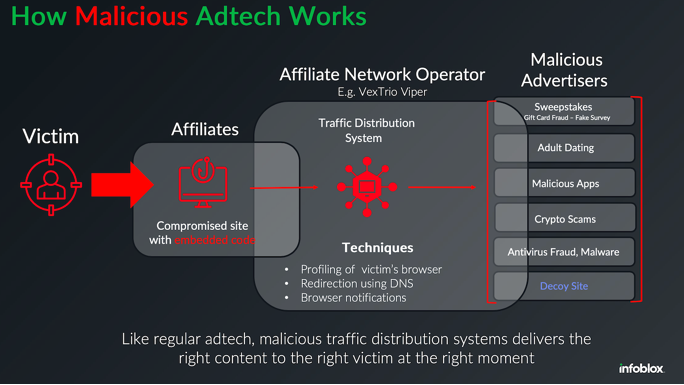
Inside a Dark Adtech Empire Fed…
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising technology that powers a sprawling ecosystem of online hucksters and website hackers. A new report on the fallout from that investigation finds this dark ad tech industry is far more
Meet This Year’s North America Community…
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our podcast series, Coffee with the Council. I’m Alicia Malone, Director of Communications and Public Relations for the PCI Security Standards Council. Today, I am so excited to bring you a sneak peek interview with PCI
Five Uncomfortable Truths About LLMs in…
Many tech professionals see integrating large language models (LLMs) as a simple process -just connect an API and let it run. At Wallarm, our experience has proved otherwise. Through rigorous testing and iteration, our engineering team uncovered several critical insights about deploying LLMs securely and effectively. This blog shares our journey of integrating cutting-edge AI
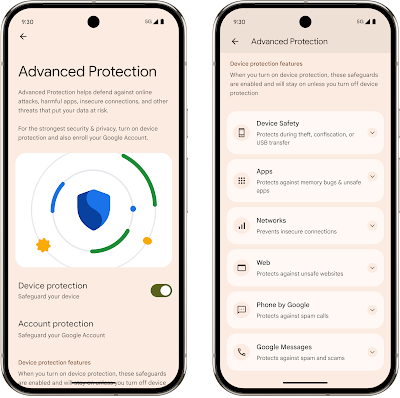
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment at Google, which is why we have our Advanced Protection Program that provides Google’s strongest protections against targeted attacks. To enhance these existing device defenses, Android 16 extends Advanced Protection with a device-level security setting
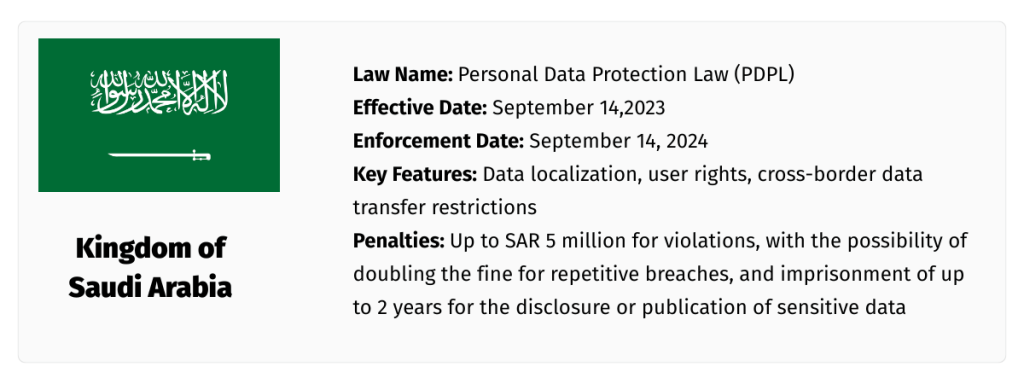
How the Middle East Is Defining…
Middle East Privacy A new chapter in data privacy is being written across the Middle East—one that’s defined by momentum, modernization, and a growing emphasis on digital sovereignty. In just a few short years, countries across the region have gone from having limited regulatory frameworks to implementing—or actively drafting—comprehensive data protection laws designed to govern

How a 12-year-old bug in Sudo…
The vulnerability, with a critical CVSS rating of 9.3 out of 10, affects Sudo versions 1.9.14 through 1.9.17, and Stratascale researchers said they verified the exploitation on Ubuntu 24.04.1 and the Fedora 41 server. “CVE-2025-32463 involves a local privilege escalation vector that doesn’t require the user to be in the sudoers file,” said Marc England,

My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power infrastructure during early cyberattacks (see doc at the end). At that time, only a few cybersecurity companies were truly exploring the risks tied to power grids and generation plants. But this April, while visiting Spain,
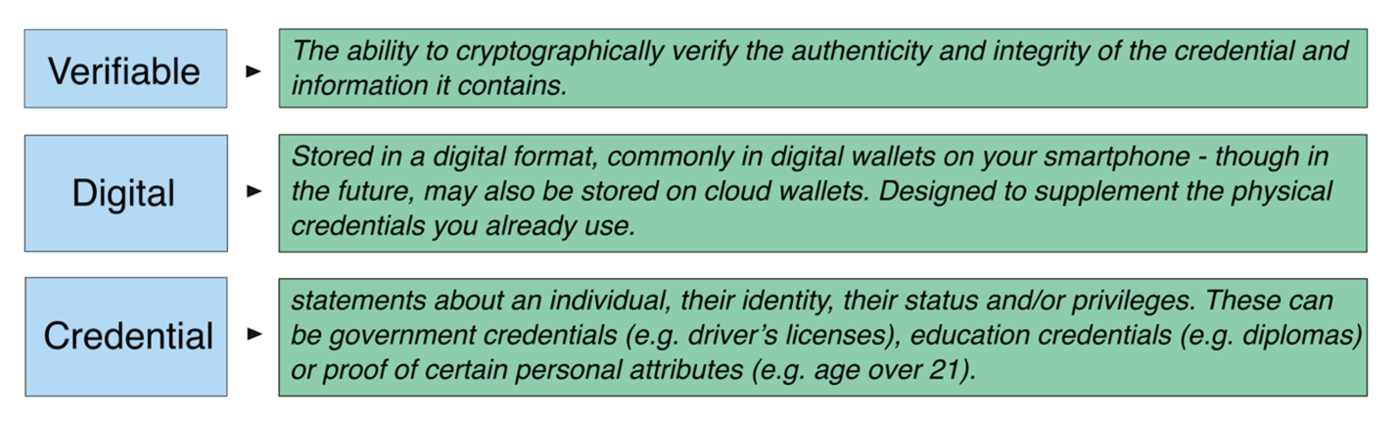
Digital Identities: Getting to Know the…
If you are interested in the world of digital identities, you have probably heard some of the buzzwords that have been floating around for a few years now… “verifiable credential,” “digital wallet,” “mobile driver’s license” or “mDL.” These terms, among others, all reference a growing ecosystem around what we are calling “verifiable digital credentials.” But

Scattered Spider Attacks US Airlines –…
From courtroom breaches to cockpit infiltration, here’s this week’s Cyber Snapshot. Five critical stories you need on your radar, with safety advice included. We’ve got insider revenge, MFA manipulation, rogue browser extensions, and state-sponsored email theft, all in one rapid-fire rundown. Whether you’re in IT, cybersecurity compliance, or just trying to keep your team one










