
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Amazon Q For Code to Deploy…
WARNING: Do not blindly create IAM resources with AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code. 🔒 Related Stories: Cybersecurity | Penetration Tests 💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ TLDR; A lot when sideways creating this script. Although I find
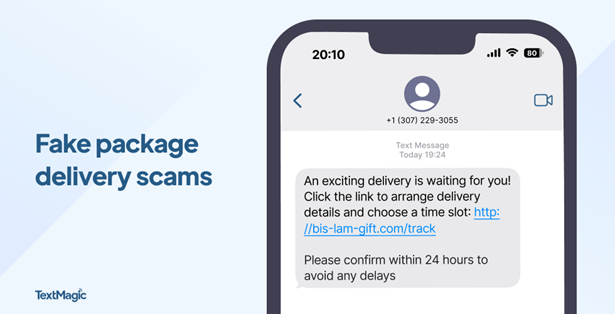
Mobile security matters: Protecting your phone…
It all starts so innocently. You get a text saying “Your package couldn’t be delivered. Click here to reschedule.” Little do you know, clicking that link could open the door for scammers to steal your identity, empty your bank account, or even plant malicious software (malware) on your device. Unless you know what to look out

A Guide to Developing Security-First Culture…
HomeCybersecurity Lifehacks A Guide to Developing Security-First Culture Powered by Threat Intelligence Security-First Culture (SFC) is an organization-wide commitment where security considerations influence decision-making at every level, from strategic planning to daily operational tasks. It’s not just about having fancy tech or a dedicated IT team; it’s about making security a core part of how

The Impact of Security Breaches on…
This blog was originally published by Bravura here. Educational institutions oversee hundreds or thousands of students and faculty members daily. Therefore, it’s no surprise they deal with large volumes of valuable data, like: Student and educator login information. Home addresses. Birthdays. Full names. Social security numbers. Credit card information and other financial records. Education

The Importance of Cybersecurity Training for…
Cybersecurity stopped being an IT issue a long time ago. It took precedence as a business priority as cyber attackers began evolving their tactics and persistence. However, it’s now quickly becoming a boardroom imperative given how damaging recent cyber attacks have been to business operations, stock value and the reputation of the Board.
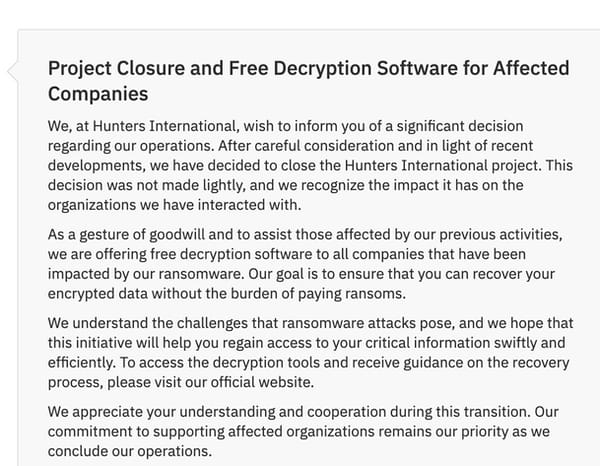
Hunters International ransomware group shuts down
The notorious Hunters International ransomware-as-a-service operation has announced that it has shut down, in a message posted on its dark web leak site. In a statement on its extortion site, the ransomware group says that it has not only “decided to close the Hunters International project” but is also offering free decryption tools to its

How Modern XDR Platforms Spot Insider…
Most people imagine hackers, ransomware, or harmful software when they hear about cybersecurity threats. However, a quieter danger often comes from within — insider threats. These might include upset employees, external contractors, or even innocent users tricked by scams like credential phishing. Detecting insider threats is one of the toughest and most vital parts of
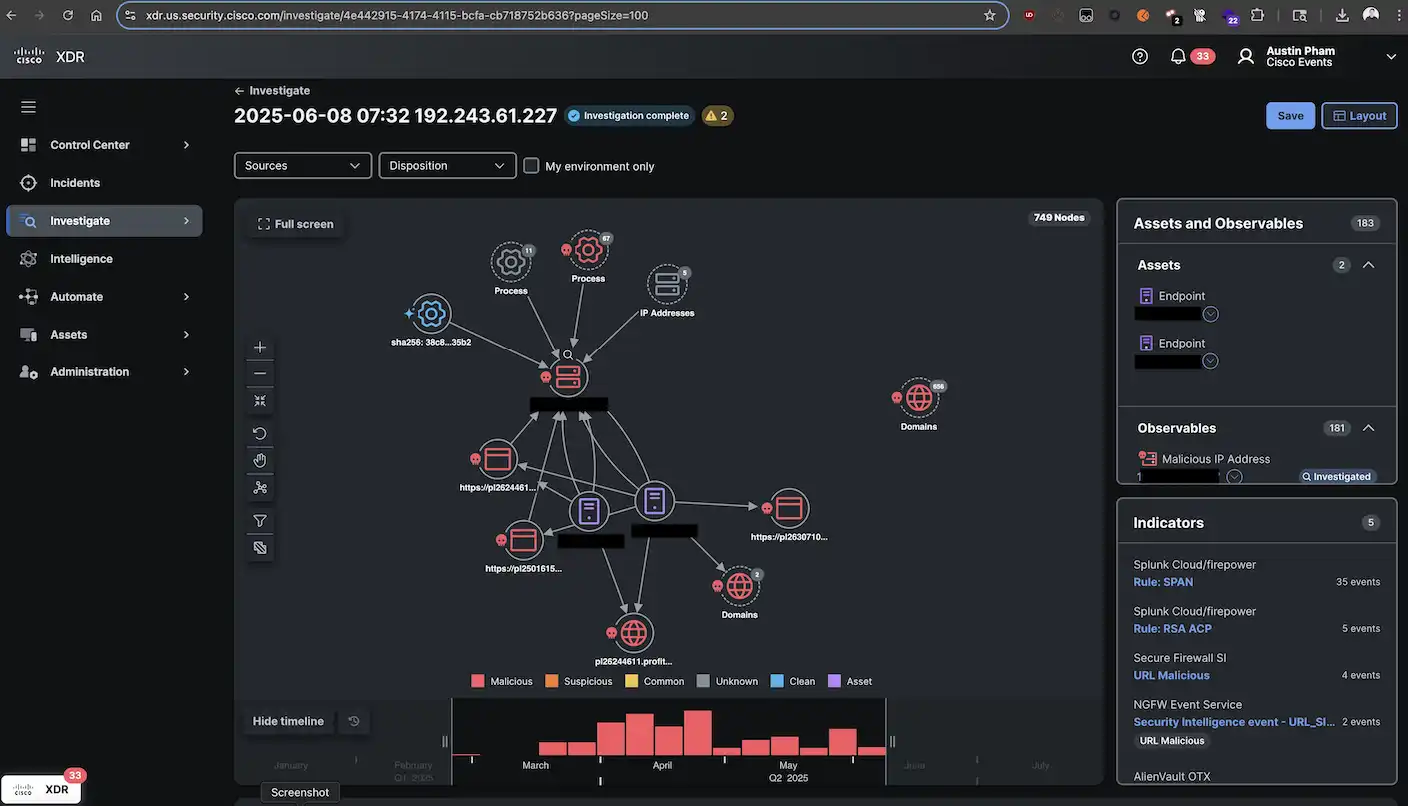
Splunk in Action at the Cisco…
Additional Post Contributors: Austin Pham, Tony Iacobelli Cisco and Splunk, together, elevate the SOC’s Incident Detection and Response experience to the next level by combining technologies from both sides that provide an even greater single pane of glass view to threats in real time. Technologies such as Cisco XDR and Security Cloud and Splunk Enterprise

Fairfax County, Va., CISO Michael Dent…
I have known Michael Dent, the Fairfax County, Va., chief information security officer, for more than a decade, and his knowledge, expertise, insights, perspectives and accomplishments never cease to impress me. Michael is a seasoned cybersecurity executive and military veteran with over 30 years of experience in public-sector information security. As the CISO for Fairfax
EDR Providers vs Traditional Security Tools:…
With ever-changing cyber threats, businesses need to redefine their security strategy. Although traditional security tools like antivirus software and firewalls have long been the backbone of cybersecurity, organizations are now moving towards EDR providers (Endpoint Detection and Response) for enhanced protection. But how do EDR solutions vary from conventional security appliances? In this article, we’ll










