
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
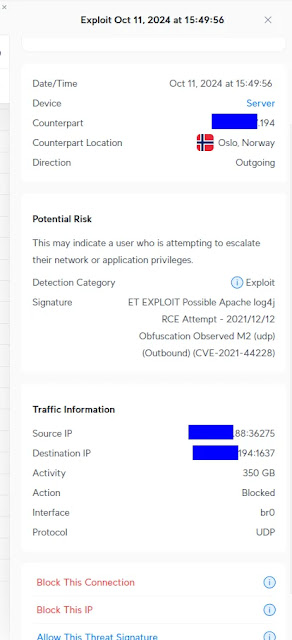
What Are Normal Users Supposed to…
Probably once a week, I see posts like this in the r/Ubiquiti subreddit. Ubiquiti makes network gear that includes an “IDS/IPS” feature. I own some older Ubiquiti gear so I am familiar with the product. When you enable this feature, you get alerts like this one, posted by a Redditor: This is everything you get
Everything You Need to Know
The business world runs on email. It’s our primary method of communication, both internally and externally, which makes it both a necessity and a risk to manage. Because we share information via email — some of it sensitive — it’s important to ensure that information remains protected, secure, and compliant.
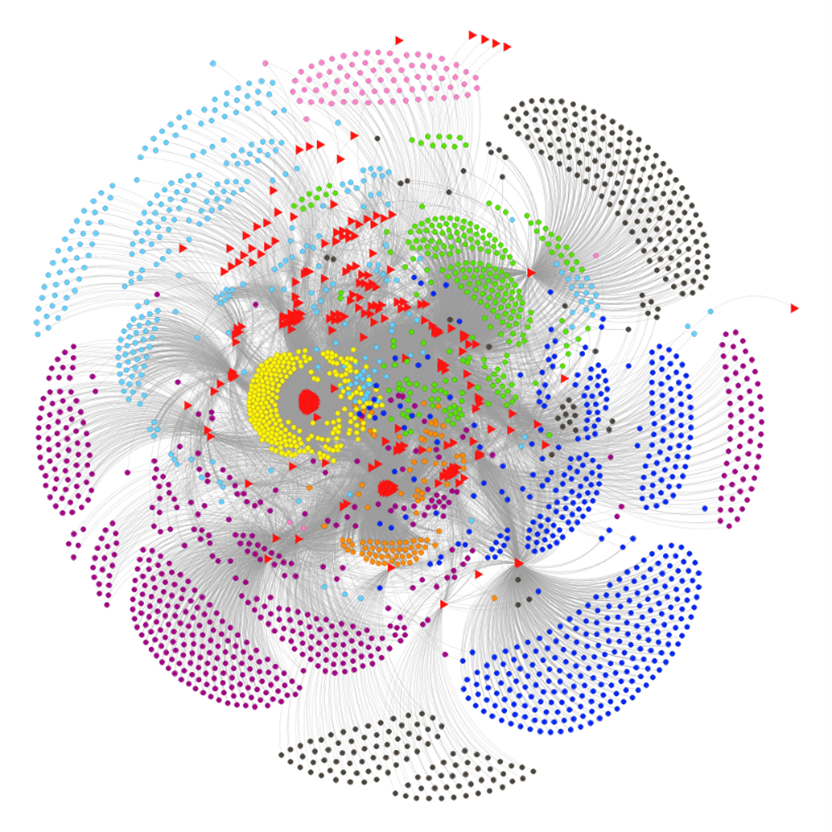
Using AI to identify cybercrime masterminds…
Online criminal forums, both on the public internet and on the “dark web” of Tor .onion sites, are a rich resource for threat intelligence researchers. The Sophos Counter Threat Unit (CTU) have a team of darkweb researchers collecting intelligence and interacting with darkweb forums, but combing through these posts is a time-consuming and resource-intensive task,
Is hacktivism acceptable? — Matt Palmer
This week I attended CSO Online’s CSO Security Summit in London, which was tracked into protection and culture tracks. One of the most interesting aspects of this was the focus on mental heath. As any incident responder (professional or accidental!) will know, these can be very stressful. We ignore these issues at our peril. However

How To Save Your Children From…
If you’re a parent and haven’t been in touch with gaming for a while, you’d be surprised at how much it has changed. Gaming is no longer the single-user experience that you may remember from the 1990s or the early 2000s. Today’s games are full-blown experiences centred around communities that see players participating in the

Cybersecurity Advisory: Hackers Exploit Zoom’s Remote…
A newly uncovered cyberattack campaign is exploiting Zoom’s Remote Control feature to infiltrate the systems of cryptocurrency traders and venture capitalists. Named “Elusive Comet,” this campaign employs sophisticated social engineering tactics to trick users into granting remote access during Zoom meetings, leading to the deployment of infostealer malware and unauthorized access to sensitive data. How

MY TAKE: Microsoft takes ownership of…
Last week at Microsoft Build, Azure CTO Mark Russinovich made headlines by telling the truth. Related: A basis for AI optimism In a rare moment of public candor from a Big Tech executive, Russinovich warned that current AI architectures—particularly autoregressive transformers—have structural limitations we won’t engineer our way past. And more than that, he acknowledged

Bridging the Nursing Workforce Skills Gap…
The US is facing a critical nursing workforce challenge, with increasing shortages and evolving skill demands. As healthcare facilities scramble to fill gaps, technology-driven solutions are proving essential in streamlining recruitment and ensuring nurses have the right qualifications. One such innovation is the use of online skills checklists, which allow recruiters to assess candidates efficiently,

Hackers Use Leaked Shellter Tool License…
Jul 08, 2025Ravie LakshmananMalware / Cybercrime In yet another instance of threat actors repurposing legitimate tools for malicious purposes, it has been discovered that hackers are exploiting a popular red teaming tool called Shellter to distribute stealer malware. The company behind the software said a company that had recently purchased Shellter Elite licenses leaked their

Competing with layer zero in cybersecurity
I am not aware of anyone who has previously attempted to define the concept of layer zero in security. Chances are, you will be able to point out many holes in this idea, but having seen how the industry operates and how the products are built, I strongly feel the concept of layer zero needs










