
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

6 Dimensions to Cut Through the…
Hello CyberBuilders 🖖 Let’s talk AI security (don’t stop reading here, give me 2 mins!) It’s the new obsession in the cybersecurity startup world. In the past two years, funding has poured into companies claiming to protect, secure, or safeguard AI. Articles go into every flashy point exploit, then pitch simplistic one-size-fits-all fixes. But while

Windows 10 KB5062554 cumulative update released…
Microsoft has released the KB5062554 cumulative update for Windows 10 22H2 and Windows 10 21H2, with thirteen new fixes or changes. The Windows 10 KB5062554 update is mandatory as it contains Microsoft’s July 2025 Patch Tuesday security updates, which fix one zero-day vulnerability and 136 other flaws. Windows users can install this update by going into Settings, clicking

Putting Together a Disaster Recovery Plan…
Here, I will be discussing putting together a disaster recovery plan for your business. Planning ahead is crucial for your business in various areas. Whether you’re attempting to predict what your competitors are doing or creating a financial safety net for your business, the more prepared you are, the more resilient and capable your business

Layered Security – How a Defense-in-Depth…
Layered Security – How a Defense-in-Depth Approach Guards Against Unknown Threats Today’s rapidly-evolving cybersecurity landscape means businesses are under more pressure than ever. A sophisticated range of threats now aim to bypass traditional defenses, which leaves organizations vulnerable if they’re still relying on legacy tools like antimalware software. These often aren’t able to spot advanced

Cisco Patches Critical Unified CM Backdoor…
Ingram Safepay SafePay ransomware cripples Ingram Micro’s global operations, disrupting IT supp… The technology distribution giant Ingram Micro confirmed on July 6, 2025, that it had fallen victim to a sophisticated ransomware attack by the rapidly emerging SafePay cybercriminal group, marking one of the most significant supply chain disruptions in the IT industry this year.
Cranking out spearphishing campaigns against Ukraine…
ESET Research analyzes Gamaredon’s updated cyberespionage toolset, new stealth-focused techniques, and aggressive spearphishing operations observed throughout 2024 02 Jul 2025 • , 6 min. read Since Russia’s full-scale invasion of Ukraine in February 2022, cyberespionage has played a crucial role in the broader threatscape. Russia-aligned advanced persistent threat (APT) groups have relentlessly targeted Ukrainian entities,

Best MSSP Providers You Can Trust
Managed security services providers, or MSSP providers for short, have become essential allies to businesses in the face of soaring cyber attacks. These third-party experts step in to fill the critical cybersecurity gaps, delivering managed security services—all backed by deep expertise that many in-house teams simply can’t afford. To help you find the right security
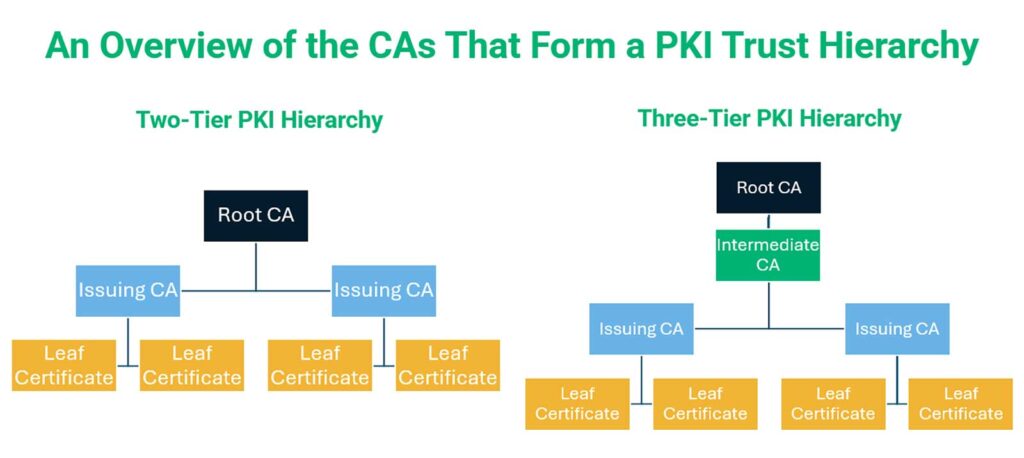
Demystifying PKI Technology: An Essential Guide…
Learn everything you need to know about PKI technology in IT security that enables organizations to establish trust in a digital world where the physical verification of identities is impossible When you open a website, make an online payment, or binge your favorite series on Netflix, PKI technology is the hidden force that makes these

Understanding Injection Attacks in Application Security:…
How Injection Attacks Exploit Web Application Vulnerabilities Injection attacks occur when malicious input is inserted into a web application, exploiting vulnerabilities in unvalidated user input to execute unintended commands. Attackers craft payloads that manipulate how the application processes data, often leading to unauthorized access, data leaks, or system compromise. This article explores the most prevalent

Webinar: Elevate your security with Microsoft…
21 May 2025, 10:00 – 11:00 CET We’re excited to invite you to an exclusive webinar, where we introduce the new Microsoft Defender XDR integration with Logpoint — built for security teams who need faster, smarter, and more scalable threat detection. Discover how easily you can: Deploy quickly with template-driven integration — no heavy










