
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Staff Stories Spotlight Series: Cybersecurity Awareness…
This blog is part of a larger NIST series during the month of October for Cybersecurity Awareness Month, called ‘Staff Stories Spotlight.’ Throughout the month of October this year, Q&A style blogs will be published featuring some of our unique staff members who have interesting backgrounds, stories to tell, and projects in the world of

Researchers Detail Bitter APT’s Evolving Tactics…
Jun 05, 2025Ravie LakshmananThreat Intelligence / Network Security The threat actor known as Bitter has been assessed to be a state-backed hacking group that’s tasked with gathering intelligence that aligns with the interests of the Indian government. That’s according to new findings jointly published by Proofpoint and Threatray in an exhaustive two-part analysis. “Their diverse
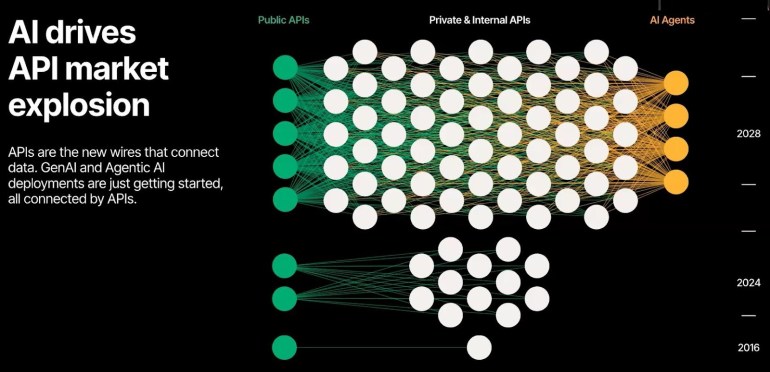
Addressing API Security with NIST SP…
According to the Wallarm Q1 2025 ThreatStats report, 70% of all application attacks target APIs. The industry can no longer treat API security as a sidenote; it’s time to treat it as the main event. NIST seems to be on board with this view, releasing the initial public draft of NIST SP 800-228, a set

What to Know Before Implementation
In today’s cybersecurity landscape, protecting your business from sophisticated cyberattacks is more critical than ever. As cyber threats continue to evolve, traditional antivirus solutions are often inadequate. That’s where EDR (Endpoint Detection and Response) solutions come in. EDR solutions provide advanced protection by detecting, investigating, and responding to threats at the endpoint level. However, selecting
Cory Doctorow Makes Us Wonder if…
Think you’re too savvy to get scammed? Author and activist Cory Doctorow explains how we’re all one muffaletta and a malfunctioning jet door away from falling prey to the most basic of cons. He joins us this week to talk about that and to fill us in about his new book, “The Bezzle.” From Ponzi

The trust crisis in the cloud…and…
As a cybersecurity consultant guiding organizations across the globe through digital transformation, I’ve observed one recurring pattern: We place immense trust in cloud services without fully questioning the fragility of their trust foundations. While cloud computing delivers undeniable benefits like agility, scalability and cost efficiency, it also introduces a new class of security risks rooted

Why Trend Micro Continues to be…
We’re pleased to share that Trend Micro has been named a Leader in the IDC MarketScape: Worldwide Cloud-Native Application Protection Platform 2025 Vendor Assessment, We believe this recognition affirms our vision to deliver a cloud security solution that predicts, protects, and responds to threats across hybrid and multi-cloud environments. Highlights from the evaluation: “Trend Vision
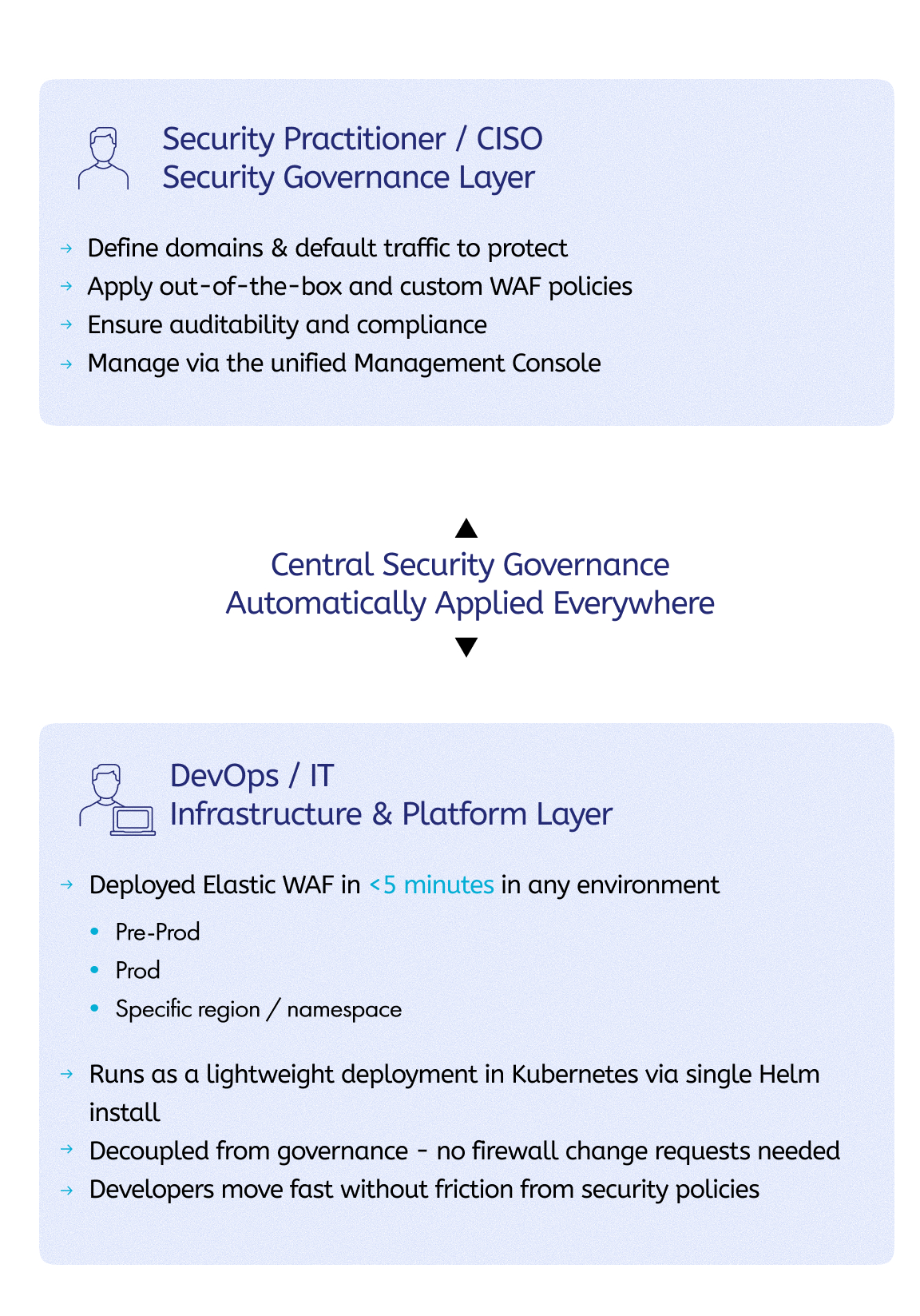
Elastic WAF: Reshaping Application Security for…
We recently discussed Imperva’s vision for the future of application security, where we also covered the Imperva Security Engine. This innovative application security framework is powering up the next generation of Imperva solutions, the first of which is Imperva Elastic WAF. This blog is the first in a series of deep-dive blogs into Elastic WAF.
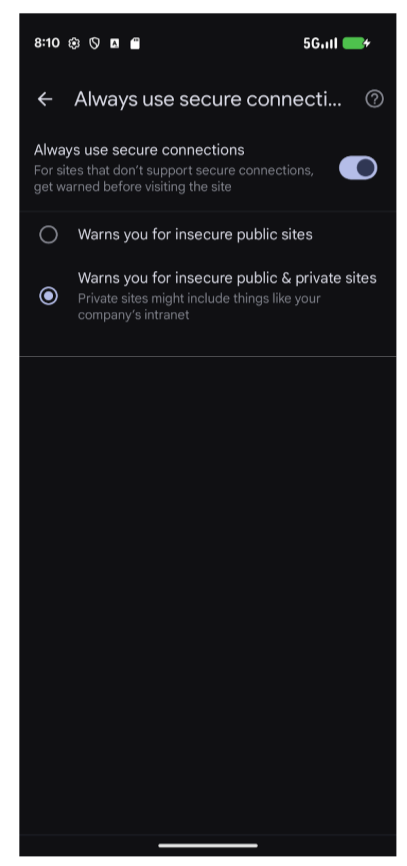
Advancing Protection in Chrome on Android
Posted by David Adrian, Javier Castro & Peter Kotwicz, Chrome Security Team Android recently announced Advanced Protection, which extends Google’s Advanced Protection Program to a device-level security setting for Android users that need heightened security—such as journalists, elected officials, and public figures. Advanced Protection gives you the ability to activate Google’s strongest security for mobile

Key Components of an Incident Response…
Key Components of an Incident Response Plan A robust incident response plan is imperative for organizations seeking to mitigate the impact of contemporary cyber threats. This document must be dynamic, subject to regular review and adaptation to address emerging vulnerabilities and attack vectors. The following outlines essential components for a comprehensive plan: 1. Preparation Preparation










