
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
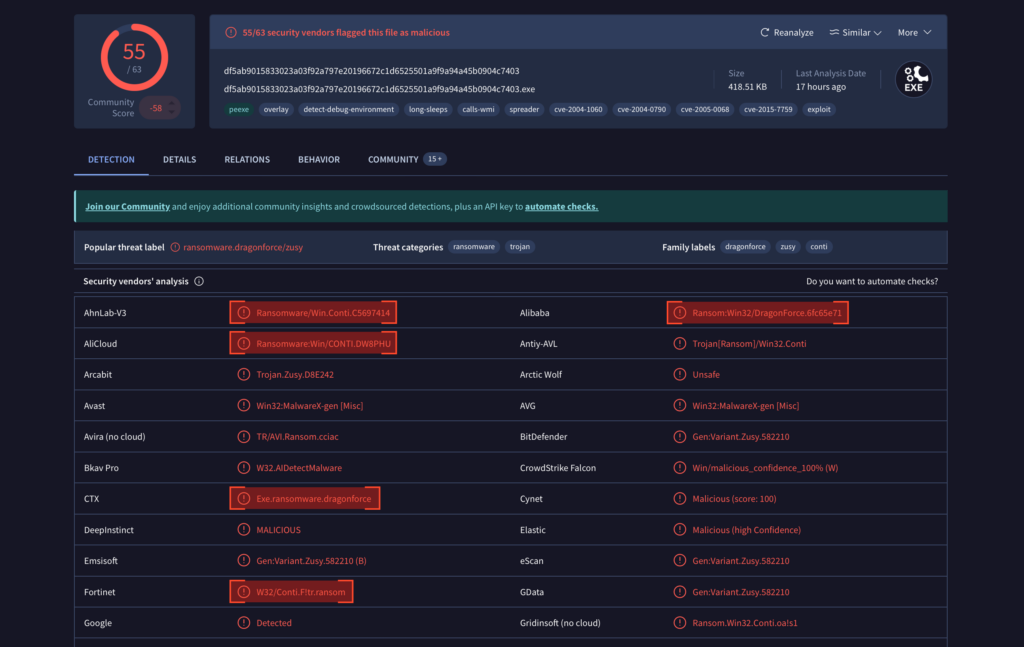
DEVMAN Ransomware: Analysis of New DragonForce…
HomeMalware Analysis DEVMAN Ransomware: Analysis of New DragonForce Variant Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and threat intelligence analyst. You can find Mauro on X. New ransomware strains continue to surface frequently, and many of them are loosely built on or repackaged from existing families. One such case

GUEST ESSAY: The AI illusion: Don’t…
Artificial intelligence is changing everything – from how we search for answers to how we decide who gets hired, flagged, diagnosed, or denied. Related: Does AI take your data? It offers speed and precision at unprecedented scale. But without intention, progress often leaves behind a trail of invisible harm. We are moving fast. Too fast.

11 Key Benefits You Should Know
What is SOC 2 Certification? SOC 2 certification is an audit framework developed by the AICPA that evaluates an organization’s ability to design and operate effective controls related to security, availability, processing integrity, confidentiality, and privacy. It’s a critical assurance tool for service providers managing customer data in the cloud, demonstrating a commitment to robust
Surveillance, spyware, and self-driving snafus •…
A Mexican drug cartel spies on the FBI using traffic cameras and spyware — because “ubiquitous technical surveillance” is no longer just for dystopian thrillers. Graham digs into a chilling new US Justice Department report that shows how surveillance tech was weaponised to deadly effect. Meanwhile, Carole checks the rear-view mirror on the driverless car
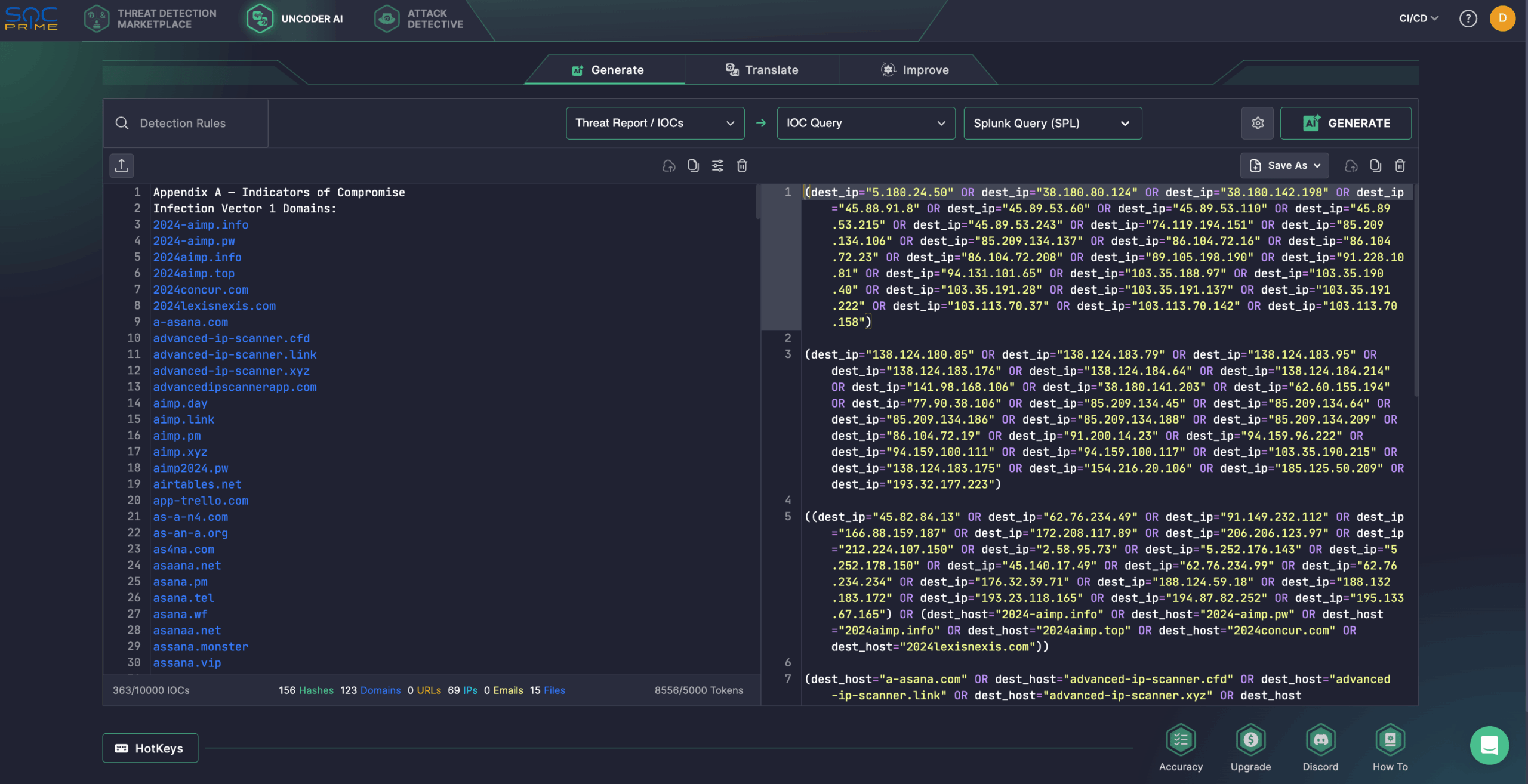
GrayAlpha Operation Detection: The Fin7-Affiliated Group…
Defenders have identified a highly sophisticated campaign orchestrated by the GrayAlpha threat actors. In this campaign, hackers employ fake browser updates and other infection vectors to deliver advanced malicious strains, a newly discovered custom PowerShell loader dubbed PowerNet, and NetSupport RAT. Notably, adversaries behind this campaign are linked to the nefarious, financially motivated group widely

Top Themes at 2025 NASCIO Midyear
“It was the best of times, it was the worst of times.” This famous opening line from Charles Dickens’ novel A Tale of Two Cities of course reflects the contradictory nature of the time period surrounding the French Revolution, juxtaposing moments of great joy and sorrow, hope and sadness. But the line also quickly summarizes

4 Mindset Shifts for Making Zero…
This blog was originally published by Cerby here. Zero Trust has become one of the cybersecurity world’s most misunderstood buzzwords. In theory, it’s simple: never trust, always verify. In practice, it’s often reduced to a check-the-box product deployment or a single vendor’s promise to “solve” it for you. But Zero Trust is not something you

Data Privacy Manager Selected for CyberBoost…
We’re proud to share that Data Privacy Manager has been selected for CyberBoost Catalyse, a prestigious accelerator programme backed by the Cyber Security Agency of Singapore, the CyberSG TIG Collaboration Centre, and innovation powerhouse Plexal. CyberBoost Catalyse is helping the most innovative cyber startups from around the world expand in Singapore, Asia Pacific and beyond. The second

Patch Tuesday, June 2025 Edition –…
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that one of the flaws is already under active attack, and that software blueprints showing how to exploit a pervasive Windows bug patched this month are now public. The sole zero-day flaw this month is
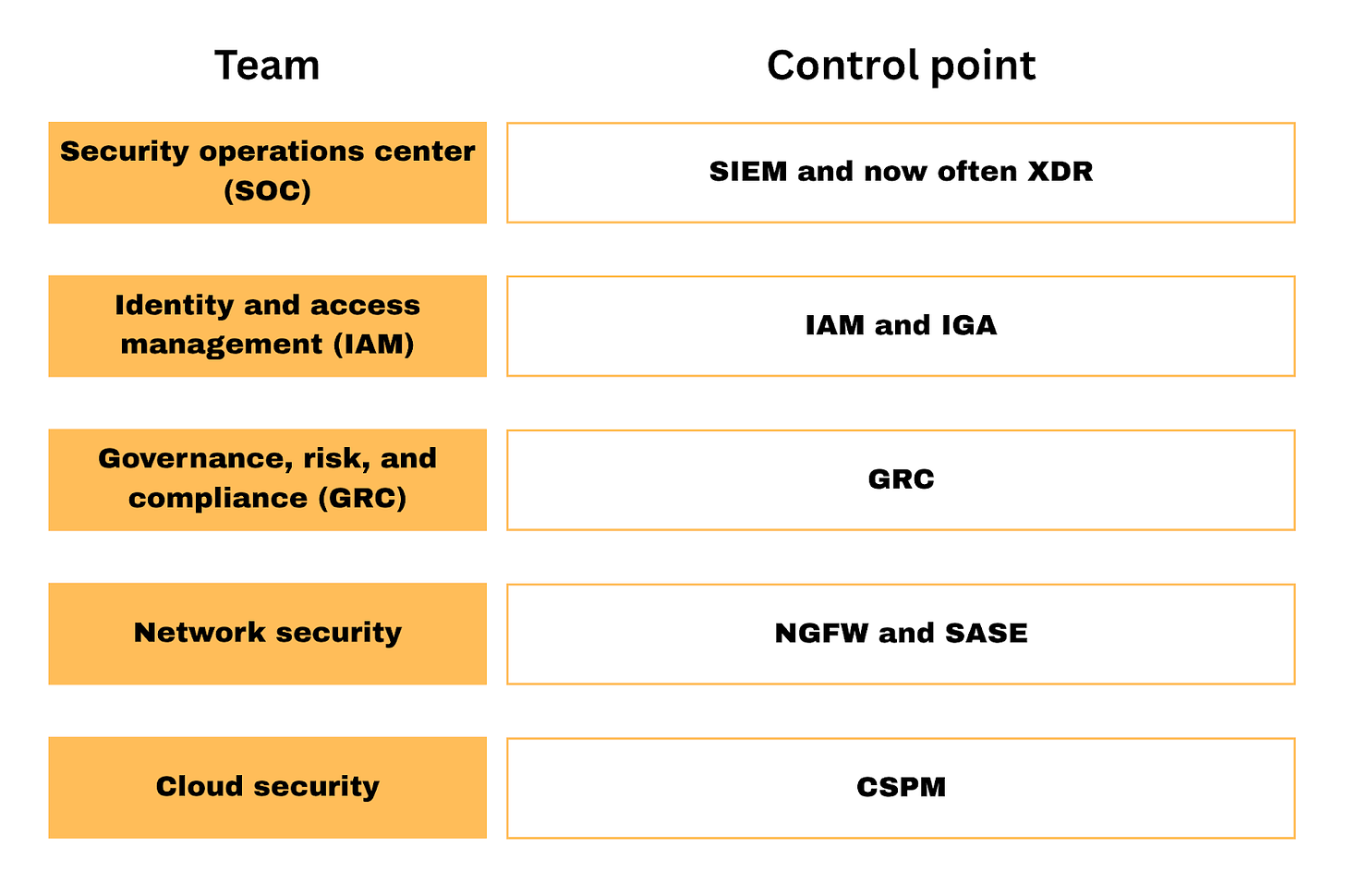
Owning the control point in cybersecurity
Dave Yuan, a venture capitalist at Tidemark who has spent over 20 years investing, likes to discuss the concept of a “control point.” Although I most definitely recommend reading one of his articles or listening to his podcasts, here’s the tl;dr of what it means. This issue is brought to you by… Tines. Not just










