
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

What to Know Before You Commit
When it comes to cybersecurity, protecting your business from evolving threats is a top priority. One of the most effective ways to secure your systems is by partnering with a Security Operations Center (SOC) service provider. These providers offer security operations center (SOC) services that include continuous monitoring, threat detection, and incident response. What Is
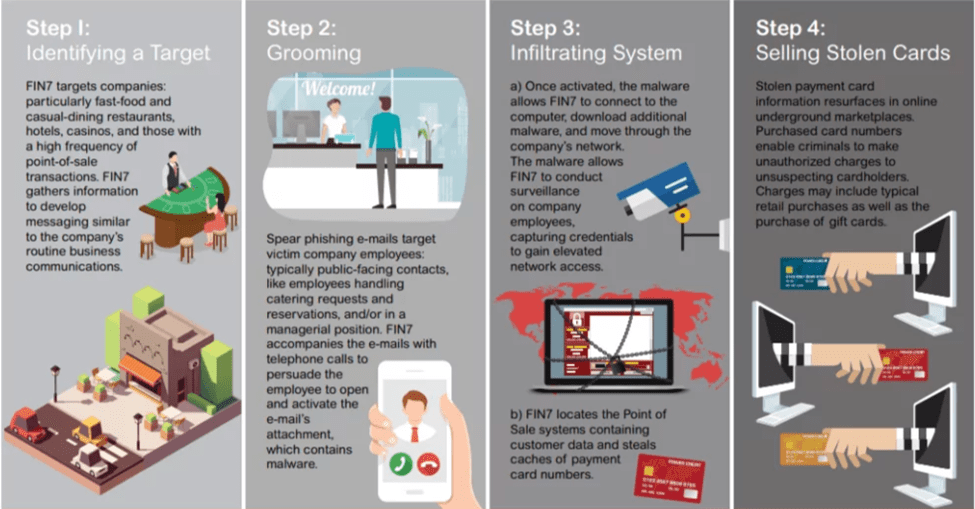
Automated DFIR Rethinking the SOC
Automated DFIR Rethinking the SOC This article is brought to you by Binalyze and is also available on their web site In December 2020, the SolarWinds cyberattack sent shockwaves across the globe. Threat actors infiltrated U.S. government agencies and private companies using a supply chain compromise so stealthy that it went undetected for months. This
Malware sharing, data wiping and exploits
ESET experts discuss Sandworm’s new data wiper, relentless campaigns by UnsolicitedBooker, attribution challenges amid tool-sharing, and other key findings from the latest APT Activity Report 01 Jul 2025 • , 2 min. read In the latest episode of the ESET Research Podcast, ESET Distinguished Researcher Aryeh Goretsky is joined by ESET Security Awareness Specialist Rene

How to Migrate SVN to GIT…
Today I’d like to share my solution for a common problem a lot of IT companies experience when finally moving from Subversion (SVN) to Git as their central version control system (VCS): Converting a SVN repository into a Git repo including its commit history and authors. To achieve this, I decided to split this issue
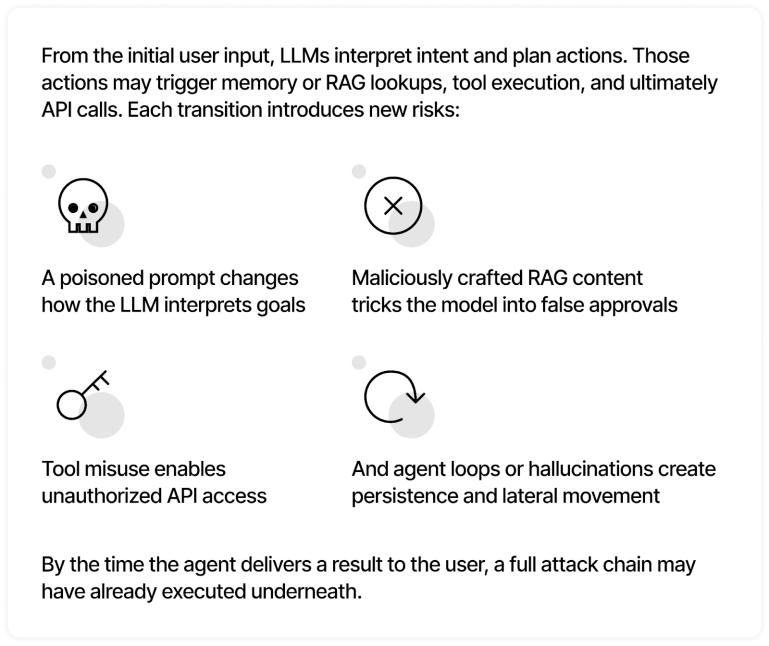
Mapping the Future of AI Security
AI security is one of the most pressing challenges facing the world today. Artificial intelligence is extraordinarily powerful, and, especially considering the advent of Agentic AI, growing more so by the day. But it is for this reason that securing it is so important. AI handles massive amounts of data and plays an increasingly important
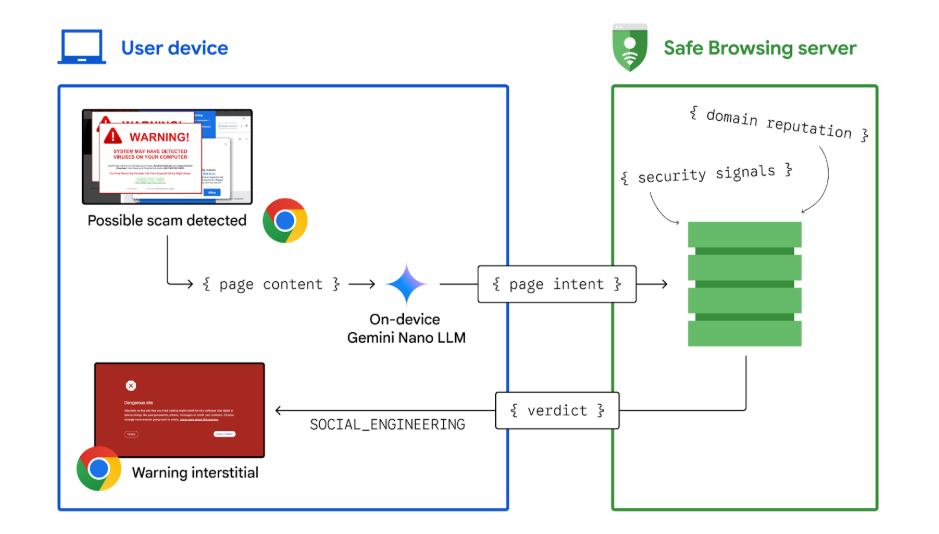
Using AI to stop tech support…
Posted by Jasika Bawa, Andy Lim, and Xinghui Lu, Google Chrome Security Tech support scams are an increasingly prevalent form of cybercrime, characterized by deceptive tactics aimed at extorting money or gaining unauthorized access to sensitive data. In a tech support scam, the goal of the scammer is to trick you into believing your computer
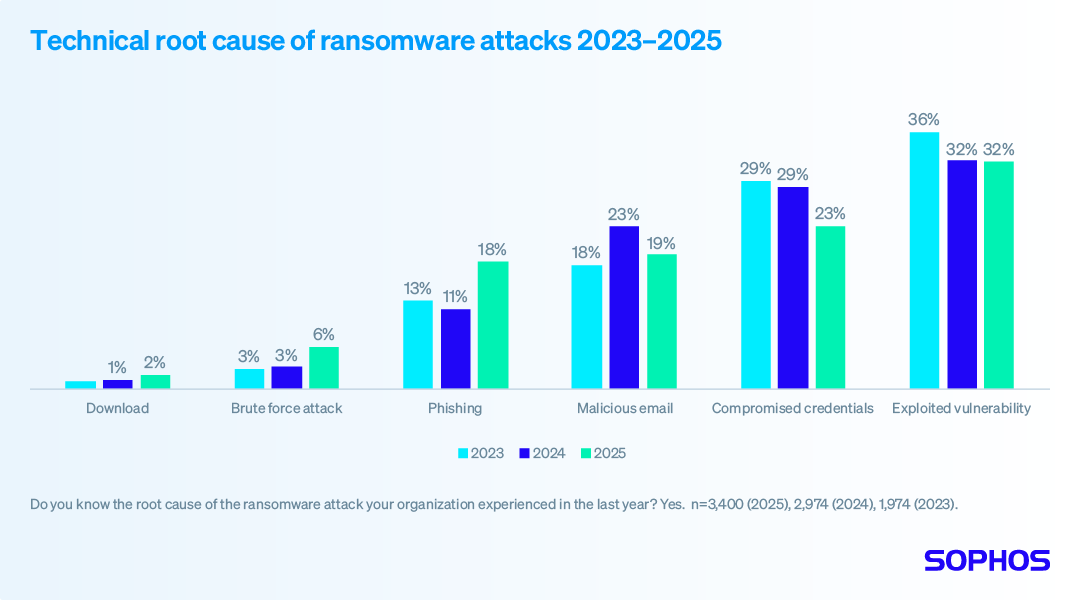
The State of Ransomware 2025 –…
The sixth annual Sophos State of Ransomware report provides fresh insights into the factors that led organizations to fall victim to ransomware and the human and business impacts of an attack. Based on insights from a vendor-agnostic survey of 3,400 IT and cybersecurity leaders across 17 countries whose organizations were hit by ransomware in the

Not Every Task Deserves One
Hello CyberBuilders 🖖 This week, I’m diving into a brilliant video from Mr. Zhang at Anthropic. You might know him as the guy behind that must-read post on what AI workflows and agents are. If you haven’t seen the video yet, I’ve dropped the link at the end of the post —it’s worth every minute.
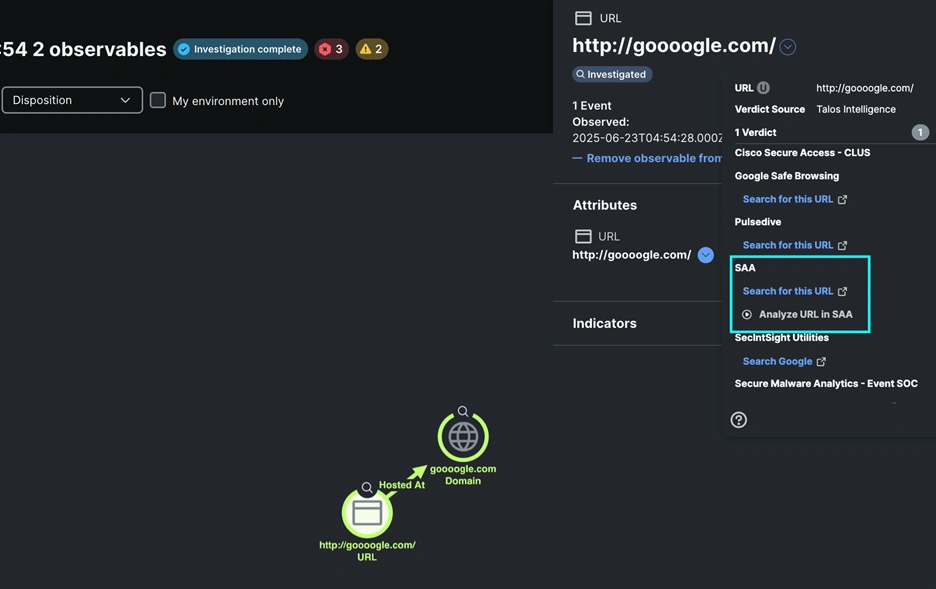
Building an XDR Integration With Splunk…
Cisco XDR is an infinitely extensible platform for security integrations. Like the maturing SOCs of our customers, the event SOC team at Cisco Live San Diego 2025 built custom integrations to meet our needs. You can build your own integrations using the community resources announced at Cisco Live. It was an honor to work with
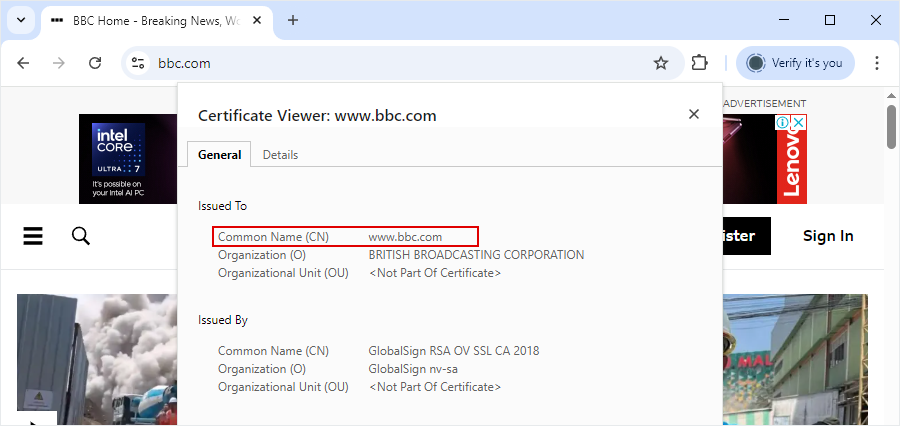
Standard SSL vs. Wildcard SSL Certificate
Securing your domain is a priority – whether you run a personal website, a business site, an e-commerce store, or even a government portal. So the real question isn’t if you need SSL, but which one is right for your business? Website owners handling a single domain may find a Standard SSL certificate sufficient, while










