
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE
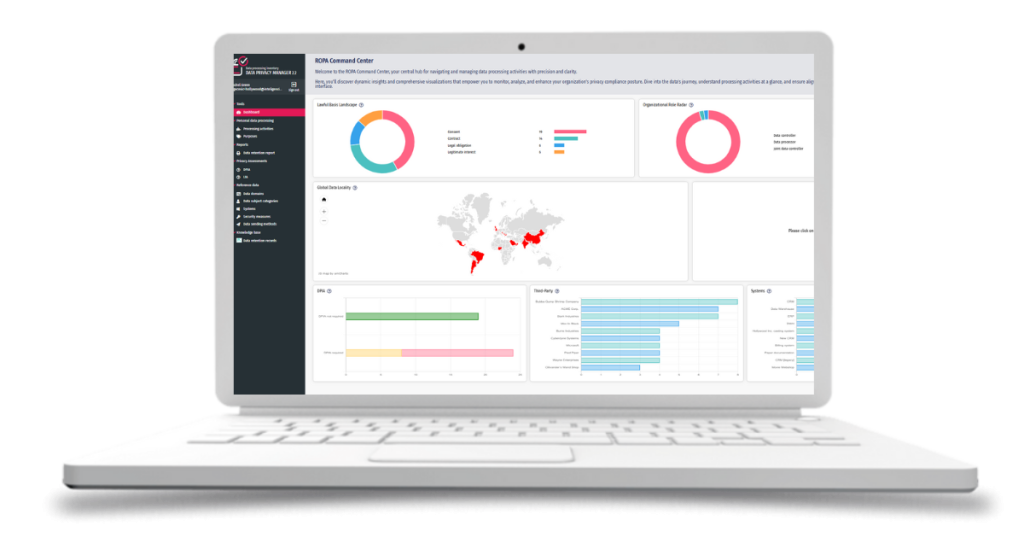
The Role of Automation – Data…
The Saudi Arabian Personal Data Protection Law (PDPL) marks a significant milestone in the kingdom’s efforts to protect individuals’ personal data. For businesses operating in Saudi Arabia or processing data related to Saudi residents, understanding and complying with this law is essential. This article will guide you through the importance of data privacy automation for achieving

July Patch Tuesday: 14 critical Microsoft…
NOTLogon vulnerability Microsoft also issued a patch for CVE-2025-47978, a denial-of-service (DoS) vulnerability in Microsoft’s Netlogon protocol, a core component of all Windows domain controllers. The hole has been dubbed NOTLogon by Dor Segal, senior security researcher at Silverfort, who discovered it. The vulnerability allows any domain-joined machine with minimal privileges to send a specially crafted
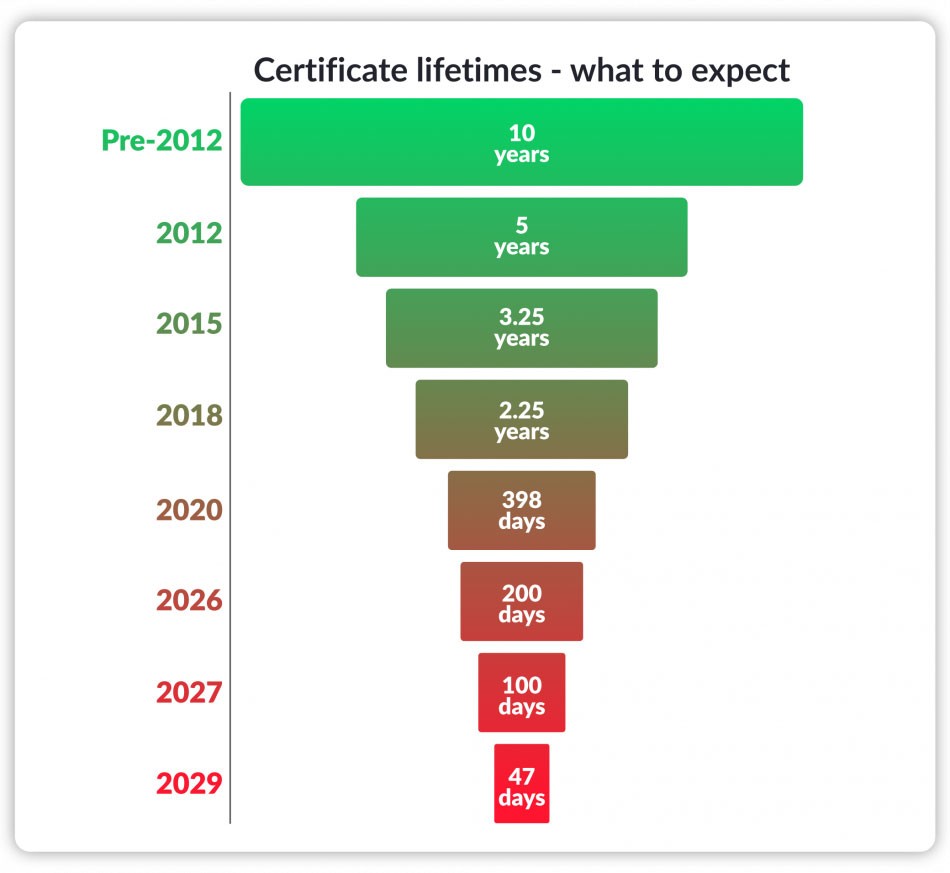
Industry Leaders Approve the Move to…
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate validity period reduction that will begin rolling out in March 2026. If you’ve been around the industry over the past decade, then you’ve seen the writing on the wall: SSL/TLS certificates have been getting shorter.

Webinar: Driving value and security to…
29 April 2025, 10:30 CET As a MSSP, delivering value and security to your customers is at the heart of your business. Do your priorities include: Providing a quality of service offering that meets customer’s need Being competitive on price Having a breadth of services to address a wide range of cyber attacks Addressing

Karen Johnson’s Scam Project Is a…
Karen Johnson is a catfisher-turned-scam avoidance coach turned–you guessed it–catfishing victim. The scam that got her is a classic, opening the door to a Pandora’s Box of the usual advice about avoiding the most common scams out there. But the thing that really got us thinking is the role AI played in almost every aspect
Weekly Update 455
The bot-fighting is a non-stop battle. In this week's video, I discuss how we're tweaking Cloudflare Turnstile and combining more attributes around how bot-like requests are, and… it almost worked. Just as I was preparing to write this intro, I found a small spike of anomalous traffic that, upon further investigation, should have been blocked.
IKEA effect in cybersecurity or why…
Security professionals take a lot of pride in the things they build – playbooks, detections, automations, open source tools, and more. Sharing these isn’t just about showing off; it’s about contributing to the craft, earning peer respect, and pushing the industry forward. What’s not being discussed is the psychology of these behaviors, the “why” behind

Why We Must Embrace Risk and…
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for the thrill of it. We take risks to make progress. Every incident is simply a manifestation of risk—its impact isn’t guaranteed, nor is its probability—but its existence is certain. Without risk, there would have been
What is IEC/ISA 62443-3-3:2013? Cybersecurity &…
The International Society of Automation (ISA) and the International Electrotechnical Commission (IEC) started creating the 62443 series of standards in 2002. The series, which includes IEC/ISA 62443-3-3, was initially referred to as the ISA99 series and contained industrial automation and control systems security (IACS) standards created following the guidance of the American National Standards Institute
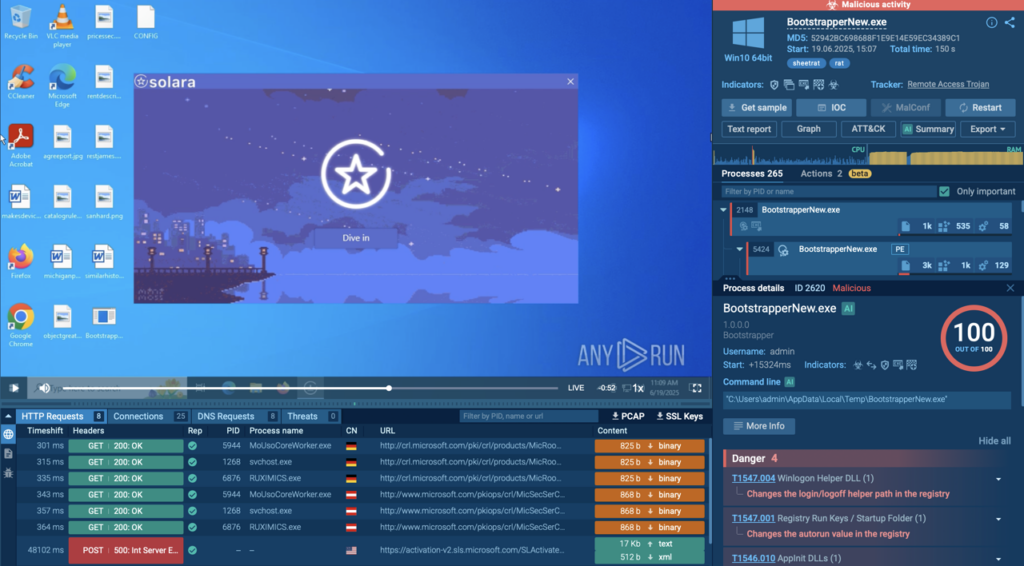
How to Spot Registry Abuse by…
HomeCybersecurity Lifehacks How to Spot Registry Abuse by Malware: Examples in ANY.RUN Sandbox When malware infiltrates a system, it doesn’t always make noise. In fact, some of the most dangerous threats operate quietly embedding themselves deep within the system and ensuring they come back even after a reboot. One of the most common ways they










