
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

Recent Cyberattacks Highlight Network Vulnerabilities –…
Recent Cyberattacks Highlight Network Vulnerabilities The network is a critical component of enterprise security yet it’s often overlooked by CISOs and security teams. Its role can be the difference between a devastating breach or a well-defended organization. In several high-profile cyberattacks across various industries, the network was a key entry point and enabler of exploitation.
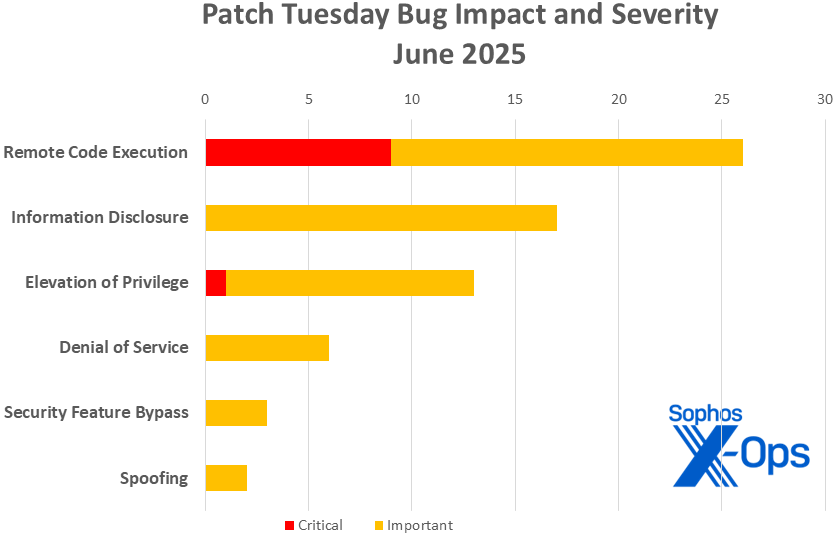
June Patch Tuesday digs into 67…
.Microsoft on Tuesday released 67 patches affecting 12 product families. Ten of the addressed issues, five involving 365 and Office and one involving SharePoint, are considered by Microsoft to be of Critical severity, and 17 have a CVSS base score of 8.0 or higher. One, an Important-severity RCE in Windows related to WEBDAV (CVE-2025-33053), is

The Rise of Agentic AI: Uncovering…
In our first post, we introduced the world of AI web agents – defining what they are, outlining their core capabilities, and surveying the leading frameworks that make them possible. Now, we’re shifting gears to look at the other side of the coin: the vulnerabilities and attack surfaces that arise when autonomous agents browse, click,

Google announces Sec-Gemini v1, a new…
Today, we’re announcing Sec-Gemini v1, a new experimental AI model focused on advancing cybersecurity AI frontiers. As outlined a year ago, defenders face the daunting task of securing against all cyber threats, while attackers need to successfully find and exploit only a single vulnerability. This fundamental asymmetry has made securing systems extremely difficult, time consuming

The Importance of Effective Joint Commission…
The Joint Commission standards play a crucial role in maintaining high levels of care and safety in healthcare settings. These standards provide guidelines that healthcare organizations must follow to ensure the safety of both patients and staff. One of the most effective ways to meet these standards is through comprehensive training programs for healthcare employees.

Over 17,000 Fake News Websites Caught…
A newly released report by cybersecurity firm CTM360 reveals a large-scale scam operation utilizing fake news websites—known as Baiting News Sites (BNS)—to deceive users into online investment fraud across 50 countries. These BNS pages are made to look like real news outlets: CNN, BBC, CNBC, or regional media. They publish fake stories that feature public

A perfect cybersecurity startup idea
Having learned a ton about the state of the industry over the past several years, and having been through the process of ideation, customer discovery, and figuring out what areas are worth focusing on myself, I ended up collecting a bunch of notes about different problem areas. In this piece, I am discussing a variety
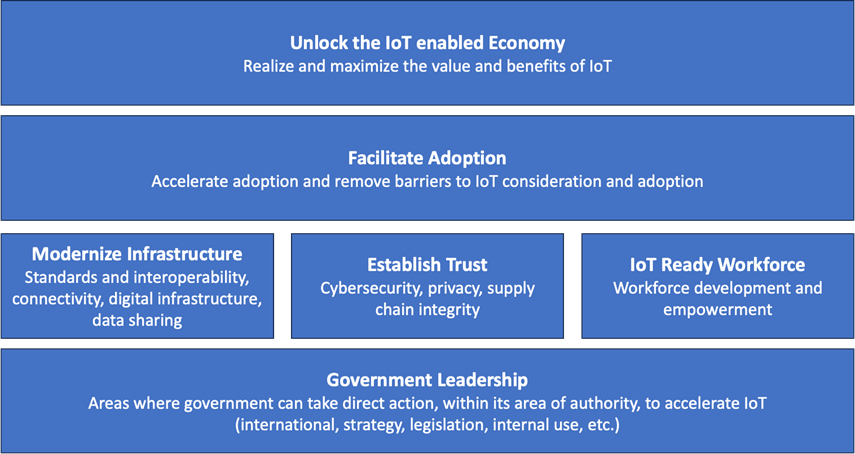
IoT Assignment Completed! Report on Barriers…
The 16 members of the NIST-managed Internet of Things (IoT) Advisory Board have completed their report on barriers to the U.S. receiving the benefits of IoT adoption, along with their recommendations for overcoming those barriers. As Benson Chan (Chair) and Dan Caprio (Vice Chair) of the IoT Advisory Board state in the report: “The United
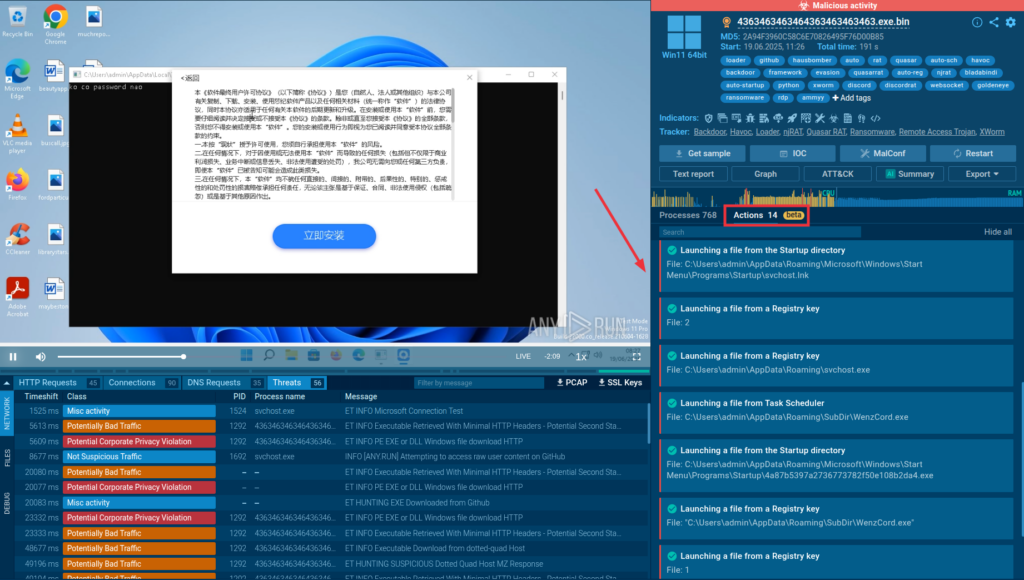
Simplify Threat Analysis and Detection with…
HomeService Updates Simplify Threat Analysis and Boost Detection Rate with Detonation Actions Threat analysis is a complex task that demands full attention, especially during active incidents, when every second counts. ANY.RUN’s Interactive Sandbox is designed to ease that pressure with an intuitive interface and fast threat detection. Our new feature, Detonation Actions, takes this further

Zero Day Security Exploits: How They…
Zero Day Security Exploits: How They Work and How to Stay Safe Zero day vulnerabilities are among the most dangerous threats businesses face today. These unknown or unpatched software flaws give cybercriminals a hidden path into systems, often leading to devastating data breaches, financial losses and reputational damage. With attacks growing more sophisticated and frequent,










