
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

The Real Meaning Behind the Jargon…
Cyber security is often conflated with the term confidentiality, but that is not correct. Traditionally, professionals tend to define it as being about confidentiality, integrity and availability (known as the CIA triad), but that’s not quite right either. So what is it? In the process of advising on our new cyber security legislation, I’ve had
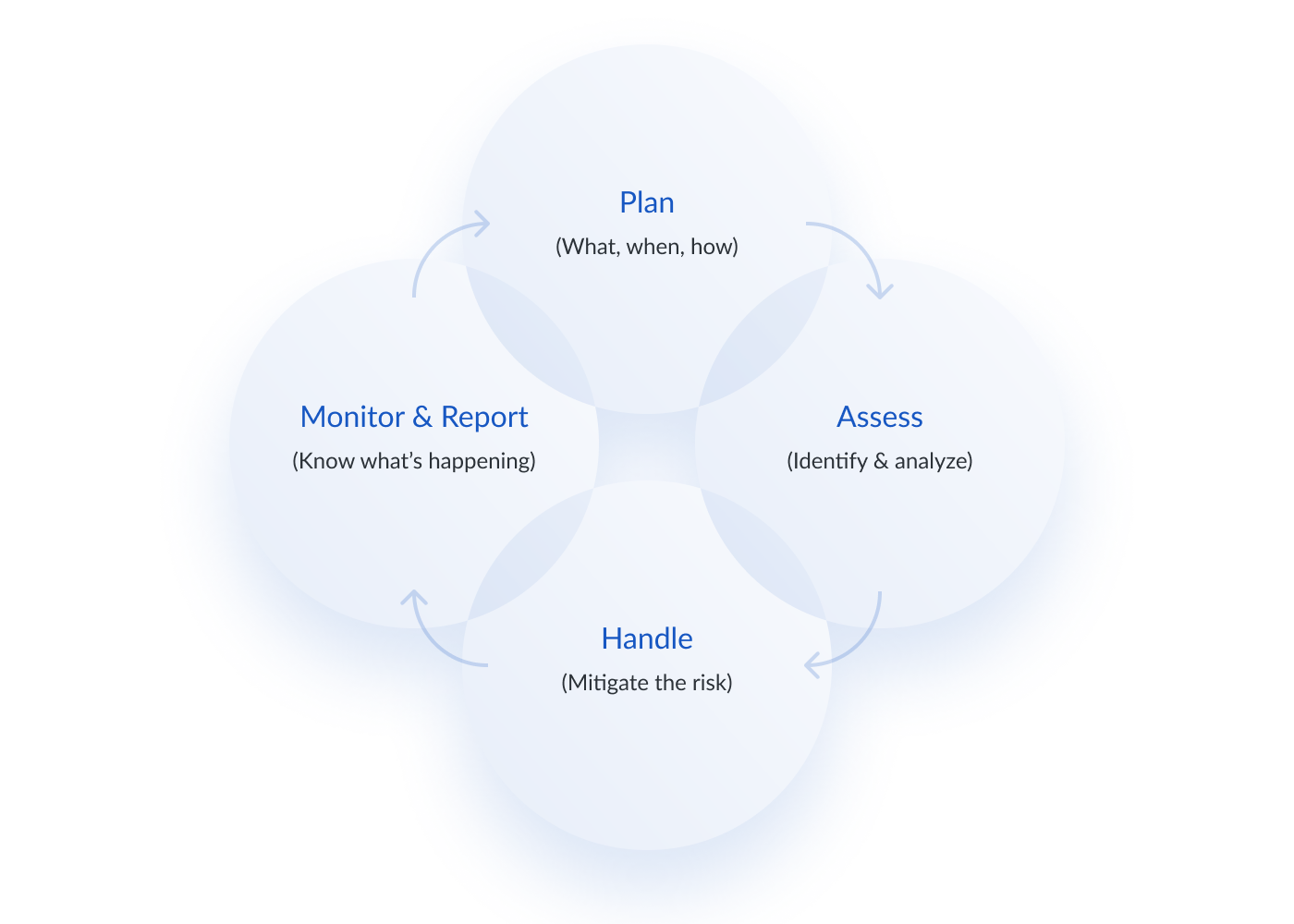
What is Information Risk Management?
Information Risk Management (IRM) is a form of risk mitigation through policies, procedures, and technology that reduces the threat of cyber attacks from vulnerabilities and poor data security and from third-party vendors. In this article, we outline how you can think about and manage your cyber risk from an internal and external perspective to protect your most sensitive data. Additionally,
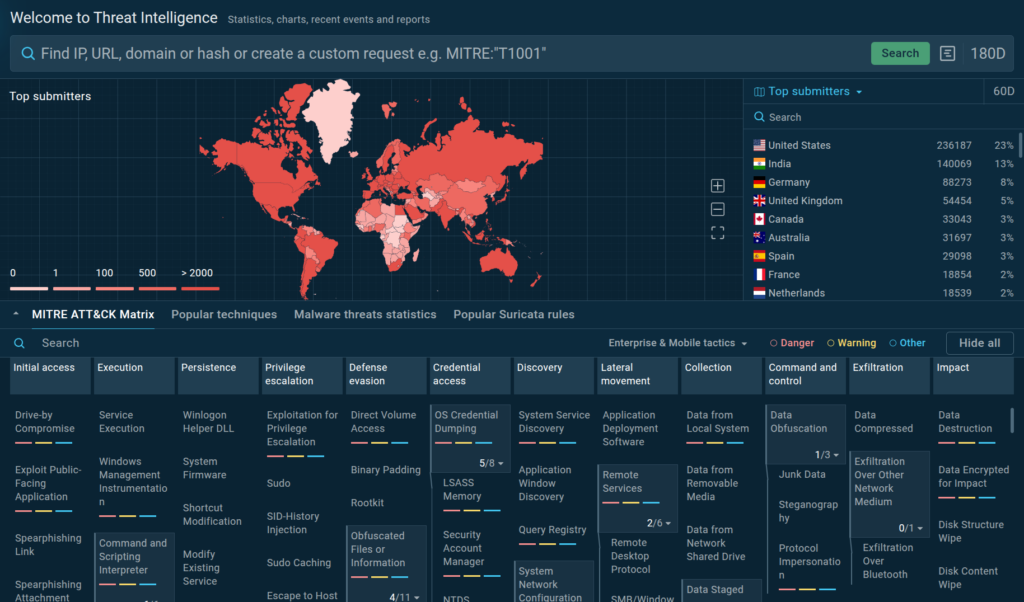
Threat Hunting: Hands-on Tips for SOC…
HomeCybersecurity Lifehacks Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs Editor’s note: The current article is authored by Clandestine, threat researcher and threat hunter. You can find Clandestine on X. Threat actors today are continuously developing sophisticated techniques to evade traditional detection methods. ANY.RUN’s Threat Intelligence Lookup offers advanced capabilities for threat data gathering and analysis.

RSAC Fireside Chat: Operationalizing diverse security…
Catastrophic outages don’t just crash systems — they expose assumptions. Related: Getting the most from cyber insurance At RSAC 2025, I met with ESET Chief Security Evangelist Tony Anscombe to trace a quiet but growing convergence: endpoint defense, cyber insurance, and monoculture risk are no longer separate concerns. They’re overlapping — and reshaping how security

PCI Key Management Operations (KMO) v1.0…
From 16 June to 18 July, eligible PCI SSC stakeholders are invited to review and provide feedback on the draft PCI Key Management Operations (KMO) v1.0 Standard during a 30-day request for comments (RFC) period.
Max McCoy Investigates $47 Million That…
Max McCoy stumbled on a $47 million swindle that starts just north of the Oklahoma panhandle and bounces to Australia before things get really confusing in a haze of small town corruption, secretive law enforcement and competing theories. On the surface, this story is just another pig butchering scam, but is that because it’s actually

How to Get the Most from…
Hello CyberBuilders 🖖 Next week, I am heading to Forum InCyber 2025, and I want to give you a quick preview of what to expect from us there. Whether you’re a startup founder, CISO, policy maker, student, or just deeply curious about the future of cybersecurity, the whole team at CyGO Entrepreneurs would love to
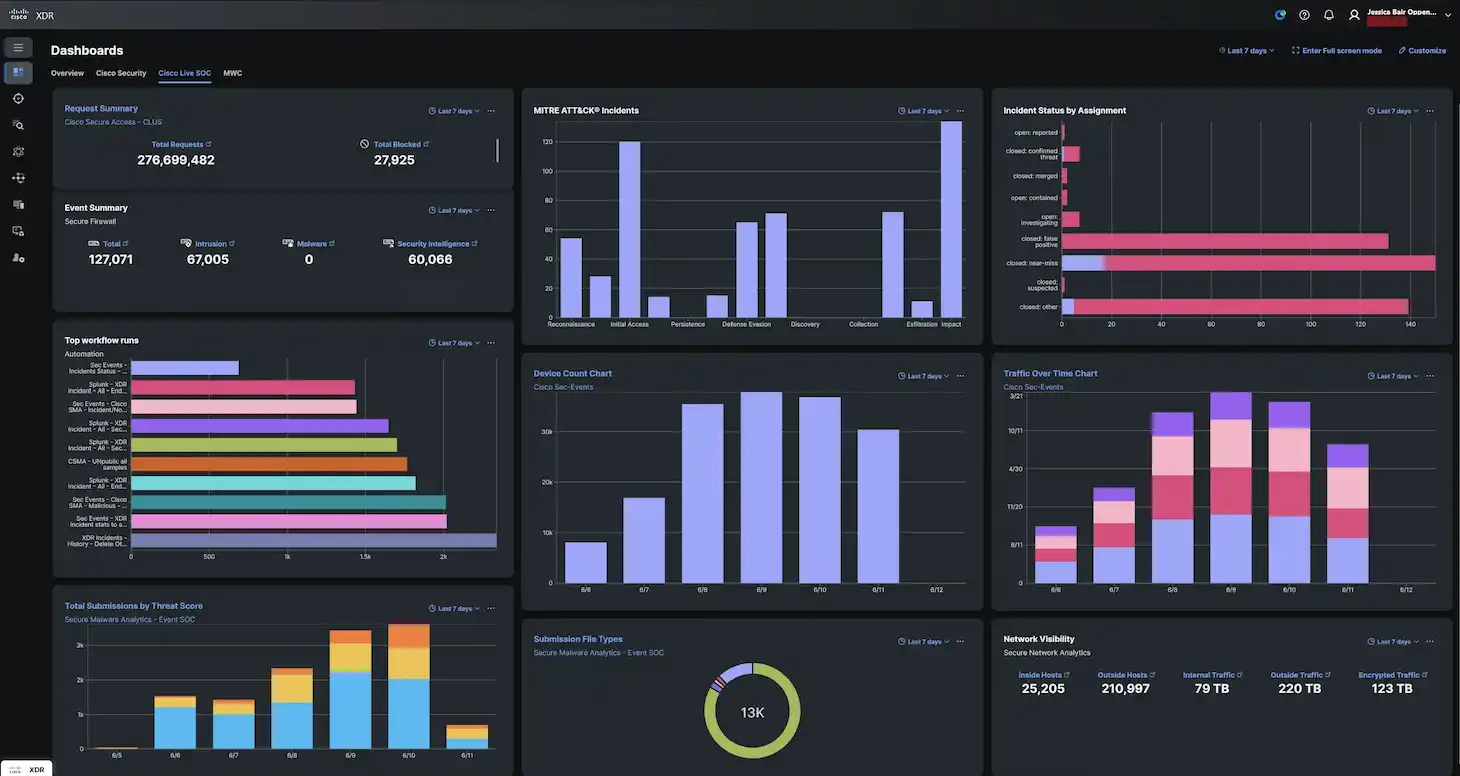
Cisco Live San Diego Case Study:…
Additional Post Contributors: Mindy Schlueter On June 11, the Cisco Live San Diego SOC received a Cisco XDR Incident triggered by two Cisco Secure Firewall events. Both pointed to a Zeek detection: SNIFFPASS::HTTP_POST_Password_Seen. This is a clear sign that credentials were transmitted in unencrypted HTTP traffic. This detection is a red flag: Usernames and passwords

Deep Fake Detection: Safeguarding Digital Media…
In this post, I will discuss deep fake detection. This will help you in safeguarding digital media authenticity in an AI-generated world. The emergence of deepfake technology represents one of the most significant challenges to digital media authenticity in the modern era. As artificial intelligence becomes increasingly sophisticated, the ability to create convincing fake videos,

Key Features for Business Protection
As the threat landscape for businesses continues to grow more complex, ensuring robust cybersecurity has become a critical priority. With an increase in sophisticated cyberattacks and growing regulatory requirements, companies need effective and proactive security measures. One solution that is gaining popularity is outsourced SOC services. By partnering with a specialized provider, businesses can access










