
Welcome From Antifingerprints
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, and damage.
Protecting digital systems and data from cyber threats.
Cybersecurity is the practice of protecting computers, servers, networks, and data from malicious attacks.
It involves tools, technologies, and processes to detect, prevent, and respond to cyber threats.
Its goal is to ensure the confidentiality, integrity, and availability of digital information.
Protects data and prevents cyber threats.
Keeps data safe from cyber attacks.
Protects against data breaches.
Prevents cyber threats.
Secures digital assets.
Protects online privacy.

LATEST
- Technical difficulties or cyber attack? Ingram…There’s no official word on what the problem is, but Ingram Micro’s website has been down since Thursday morning. They claim to be “currently experiencing technical difficulties…” Are you thinking what I’m thinking? I really hope I’m wrong, but it’s not at all unusual for … Read more
- Alleged Chinese hacker tied to Silk…A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible for cyberattacks against American organizations and government agencies. According to Italian media ANSA, the 33-year-old man, Xu Zewei, was arrested at Milan’s Malpensa Airport on July 3rd after arriving on a flight … Read more
- The Art of Leadership in TechThe Art of Leadership in Tech In today’s fast-paced technology landscape, leadership isn’t just about being technically brilliant. It’s about self-awareness, inspiring others, making smart decisions, and constantly growing—both as a professional and as a person. Whether you’re a new team lead, a seasoned engineering manager, or aspiring to become a CIO / CTO or … Read more
- Preparing for NIS2: A Compliance Guide…In January 2023, the European Commission (EC) released the second version of the European Union (EU) Network and Information Security Directive (NIS2) to enhance cybersecurity risk management across Europe. NIS2 builds upon the original NIS directive and emphasizes regulations on cloud infrastructure, internet exchanges, domain service providers, and digital service providers. Organizations offering goods or … Read more
- CyberHoot Newsletter – June 2025CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up to speed on the latest cybersecurity threats and best practices to protect your organization. This month, we’re spotlighting several critical developments that demand your attention—from newly discovered Apple AirPlay vulnerabilities impacting millions of users, to … Read more
POST

New Android TapTrap attack fools users…
View Article
Don’t Be a Victim! Blackmail Scam…
View Article
Incogni Vs DeleteMe – Which Is…
View ArticleKNOW MORE

New Android TapTrap attack fools users…
A novel tapjacking technique can exploit user interface animations to bypass Android’s permission system and allow access to sensitive data or trick users into performing destructive actions, such as wiping the device. Unlike traditional, overlay-based tapjacking, TapTrap attacks work even with zero-permission apps to launch a harmless transparent activity on top of a malicious one, a behavior

Don’t Be a Victim! Blackmail Scam…
Sextortion scam emails have become a disturbingly common occurrence in people’s inboxes. These menacing messages claim the sender has hacked your computer, recorded you visiting adult websites or engaging in compromising acts via your webcam, and will share the embarrassing video with all your contacts unless you pay a ransom in Bitcoin. But here’s the
Incogni Vs DeleteMe – Which Is…
Read on for the Incogni vs DeleteMe comparison. Your data on data brokers and people search websites is a huge risk. Anyone can get hold of it and do anything with it. For example, hackers can steal your identity and carry out malicious activities. But there’s good news! You can easily remove your information from
AI in Cybersecurity: The Good, the…
The Good – How AI Is Strengthening Cybersecurity AI systems are helping security teams with faster, smarter threat detection and response. New AI platforms in 2025 continuously analyze network traffic, user behavior, and system logs to spot anomalies that human analysts would miss. For example, AI threat detection uses machine learning and behavioral analytics to

U.S. Sanctions Cloud Provider ‘Funnull’ as…
Image: Shutterstock, ArtHead. The U.S. government today imposed economic sanctions on Funnull Technology Inc., a Philippines-based company that provides computer infrastructure for hundreds of thousands of websites involved in virtual currency investment scams known as “pig butchering.” In January 2025, KrebsOnSecurity detailed how Funnull was being used as a content delivery network that catered to
How to Use Google Cloud KMS…
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a Sectigo Code Signing Certificate Google Cloud KMS users can now enjoy the security and familiarity of managing their Sectigo Code Signing Certificate keys. This article will walk you setting up and storing your secure code
Key Network Questions
I wrote this on 7 December 2018 but never published it until today. The following are the “key network questions” which “would answer many key questions about [a] network, without having to access a third party log repository. This data is derived from mining Zeek log data as it is created, rather than storing

Reinventing Cyber Defence with Proper Licensing
Date: 1 July 2025 Once business goals are set and the appropriate SAP product suite is selected, the next step is to consider the licensing type. In today’s computerised environment, safeguarding a dynamic SAP environment is no longer about blocking external threats but also guaranteeing internal controls, especially in the case of licensing models. SAP

Was ist ein Botnet?
Ein Botnetz besteht aus vielen “Zombie”-Rechnern und lässt sich beispielsweise einsetzen, um DDoS-Attacken zu fahren. Das sollten Sie zum Thema wissen. FOTOKINA | shutterstock.com Kriminelle Hacker suchen stets nach Möglichkeiten, Malware in großem Umfang zu verbreiten oder Distributed-Denial-of-Service (DDoS)-Angriffe zu fahren. Ein Botnet eignet sich dazu besonders gut. Botnet – Definition Ein Botnet ist eine
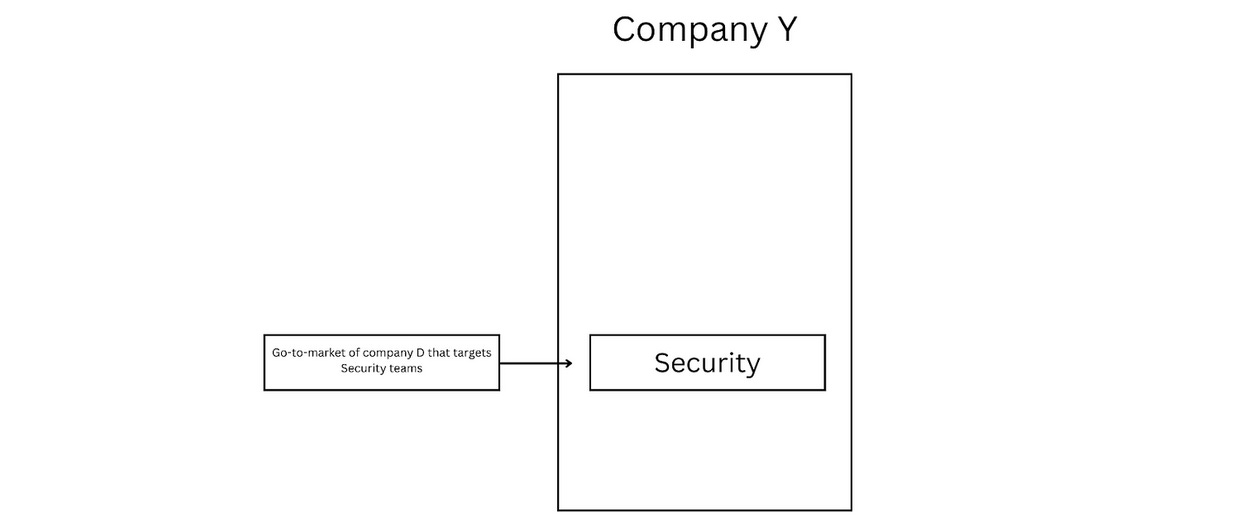
a field guide for security people
If you were to ask me three years ago if I think that security professionals should understand how startups work, I’d have answered something like a generic “It depends”. I thought that while the percentage of people in the industry who care about business, startups, and the broader ecosystem isn’t that big, people who do










