
PDPA Compliance Checklist for Singapore Businesses...
A Practical Blueprint for PDPA Compliance The Personal Data Protection Act (PDPA) is not just a legal formality — it’s a core requirement…
Read More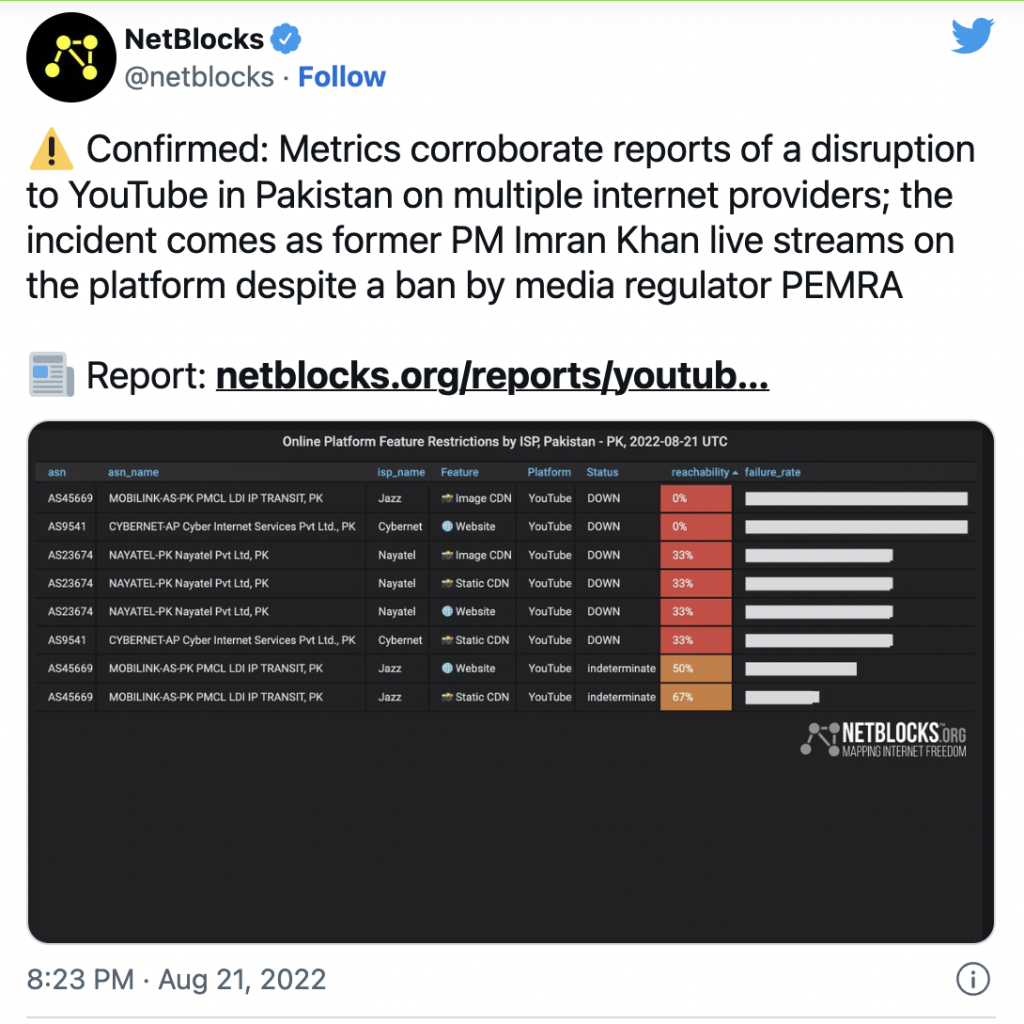
YouTube disrupted in Pakistan as former...
Advertisement NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on Sunday 21 August 2022. The disruption comes as…
Read More
Keren Elazari Decrypts the Ransomeware Nightmare
Ransomware is a type of malware that allows hackers to commandeer data on a device or an entire network. Increasingly, the threat actors…
Read More
You cannot Protect What You can’t...
You cannot Protect What You Can’t See “Imagine trying to secure your house in the dark. You wouldn’t know if someone broke in—let…
Read More
SafePay Ransomware Cripples Ingram Micro, Shocking...
Radix Sarcoma ransomware attack on Radix leaks 1.3TB of Swiss government data, exposin… A sophisticated ransomware attack has rocked Switzerland’s federal administration, exposing…
Read More
Easily Share Large CAD Files with...
Designers, engineers, architects, and manufacturers need to share CAD files to get their jobs done — whether internally across teams, or externally with…
Read More
Ready-to-Heat Food Safety: Why You Must...
As of June 2025, sixteen people across the U.S. have been hospitalized after eating Ready-to-Heat (RTH) chicken meals contaminated with Listeria monocytogenes. Of…
Read More
How to Boost Speed and Security...
In today’s world, online gaming isn’t just a hobby—it’s a serious, competitive arena where speed and security can make or break your experience.…
Read More
Top 10 Influencers to Follow In...
If you’re in the cybersecurity world — whether you’re a CISO, ethical hacker, compliance pro, or just love staying ahead of cyber threats…
Read More
Why Most Privacy Programs Fail Audits...
In privacy, what you don’t know can hurt you. Your Records of Processing Activities (ROPA) may be up to date. Your data flows…
Read MoreCategories
Latest Articles