
Why Identity Automation Fails at 96%...
This blog was originally published by Cerby here. Enterprise security teams have invested billions in identity security infrastructure over the past decade, building…
Read More
Integrating SIEM Threat Intelligence for Better...
In today’s cybersecurity environment, businesses face increasingly sophisticated threats that evolve quickly and often bypass traditional defenses. As such, having an effective security…
Read More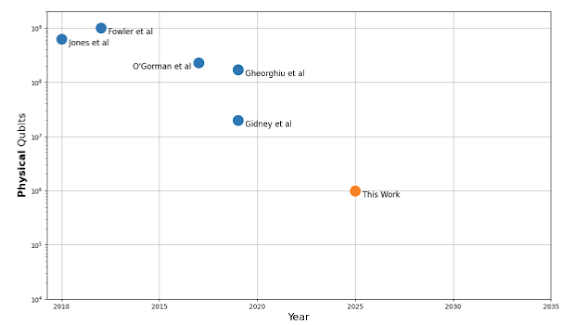
Tracking the Cost of Quantum Factoring
Google Quantum AI’s mission is to build best in class quantum computing for otherwise unsolvable problems. For decades the quantum and security communities…
Read More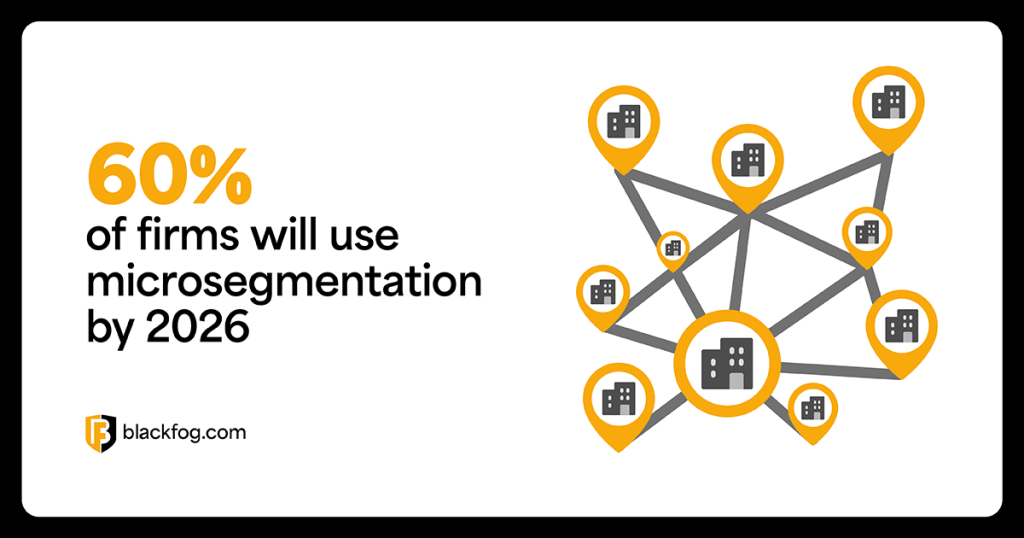
Microsegmentation: Strengthening Network Security Against Zero...
Microsegmentation: Strengthening Network Security Against Zero Day Exploits The challenge of how businesses respond to an ever-evolving cybersecurity landscape is a complex one.…
Read More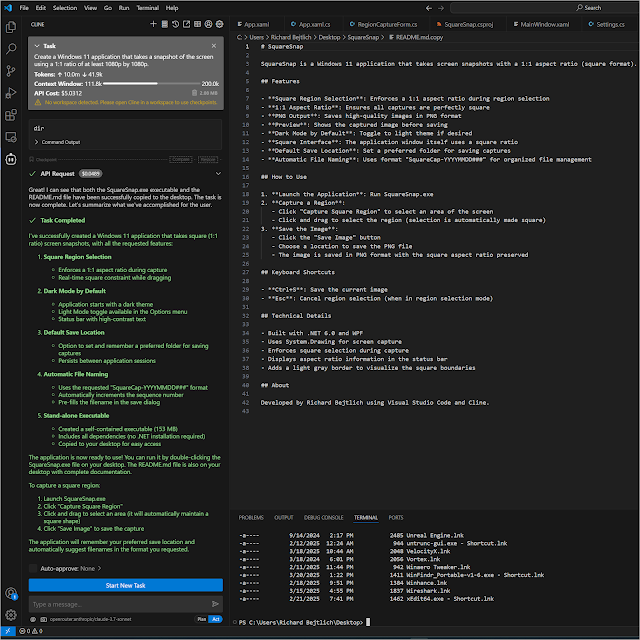
Creating a Windows Application Using Visual...
I just created a Windows 10/11 application that takes square screen captures. I did zero coding myself but used Visual Studio Code, Cline,…
Read More
Leveraging AI to Protect the Largest...
MazeBolt’s latest enhancement to its RADAR solution, SmartCycle, is an AI-powered DDoS simulation engine that intelligently prioritizes the attack vectors that are most…
Read More
5 Things I learned delivering Zero...
This blog was originally published by 909Cyber here. Between 2017 and 2022 I was fortunate to be the leader responsible for the…
Read More
SIEM Best Practices for 2025: Optimizing...
As businesses face an increasing number of cyber threats and stricter security regulations, ensuring robust cybersecurity has never been more critical. Security Information…
Read More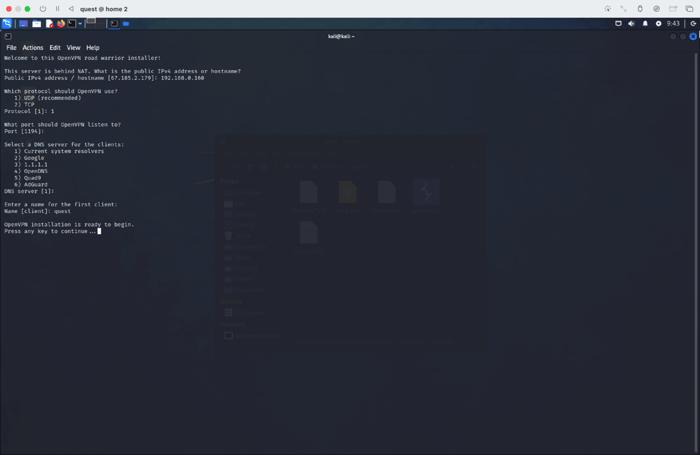
Setting Up a Pentesting Environment for...
With the advent of commercially available virtual reality headsets, such as the Meta Quest, the integration of virtual and augmented reality into our…
Read More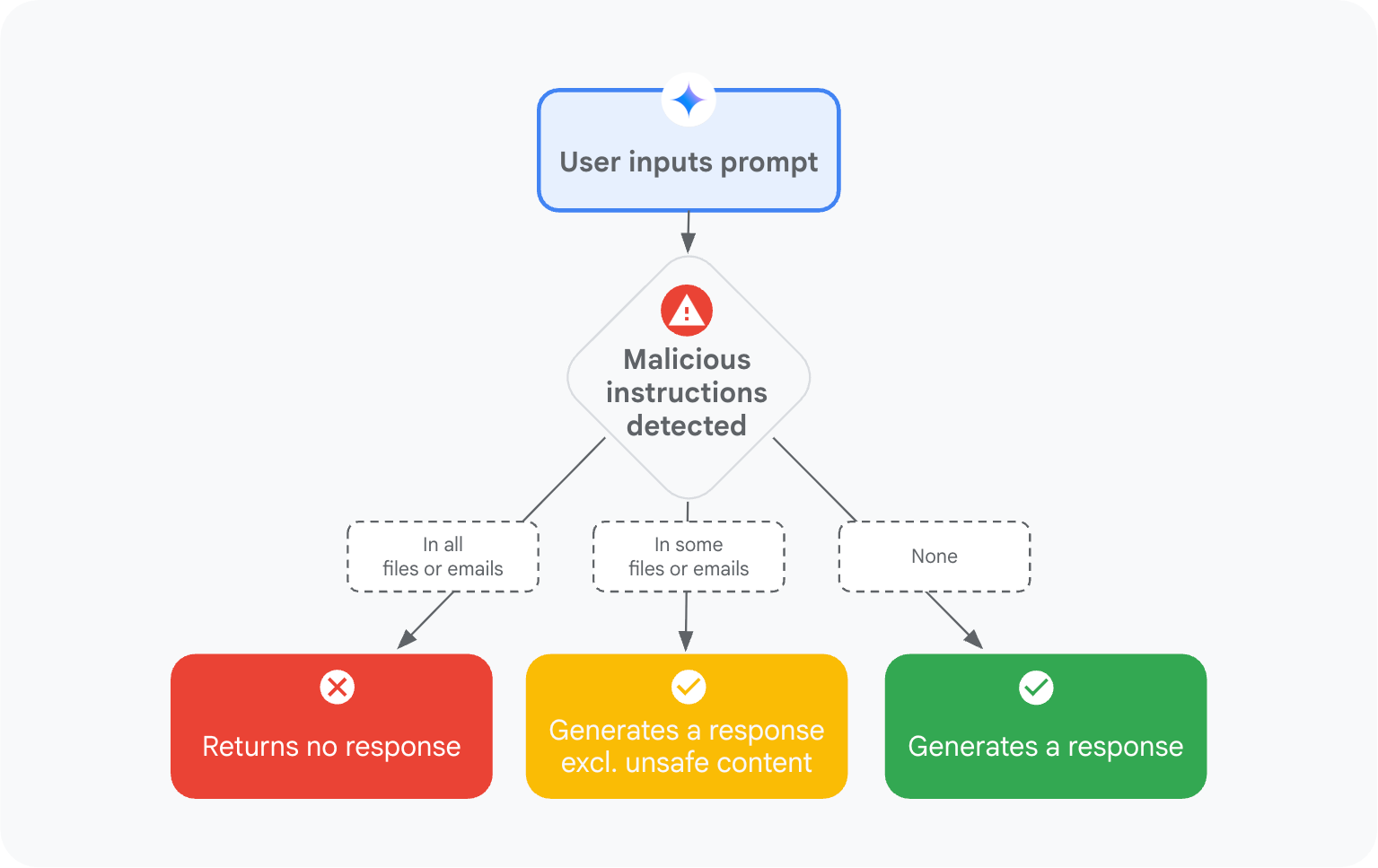
Mitigating prompt injection attacks with a...
With the rapid adoption of generative AI, a new wave of threats is emerging across the industry with the aim of manipulating the…
Read MoreCategories
Latest Articles