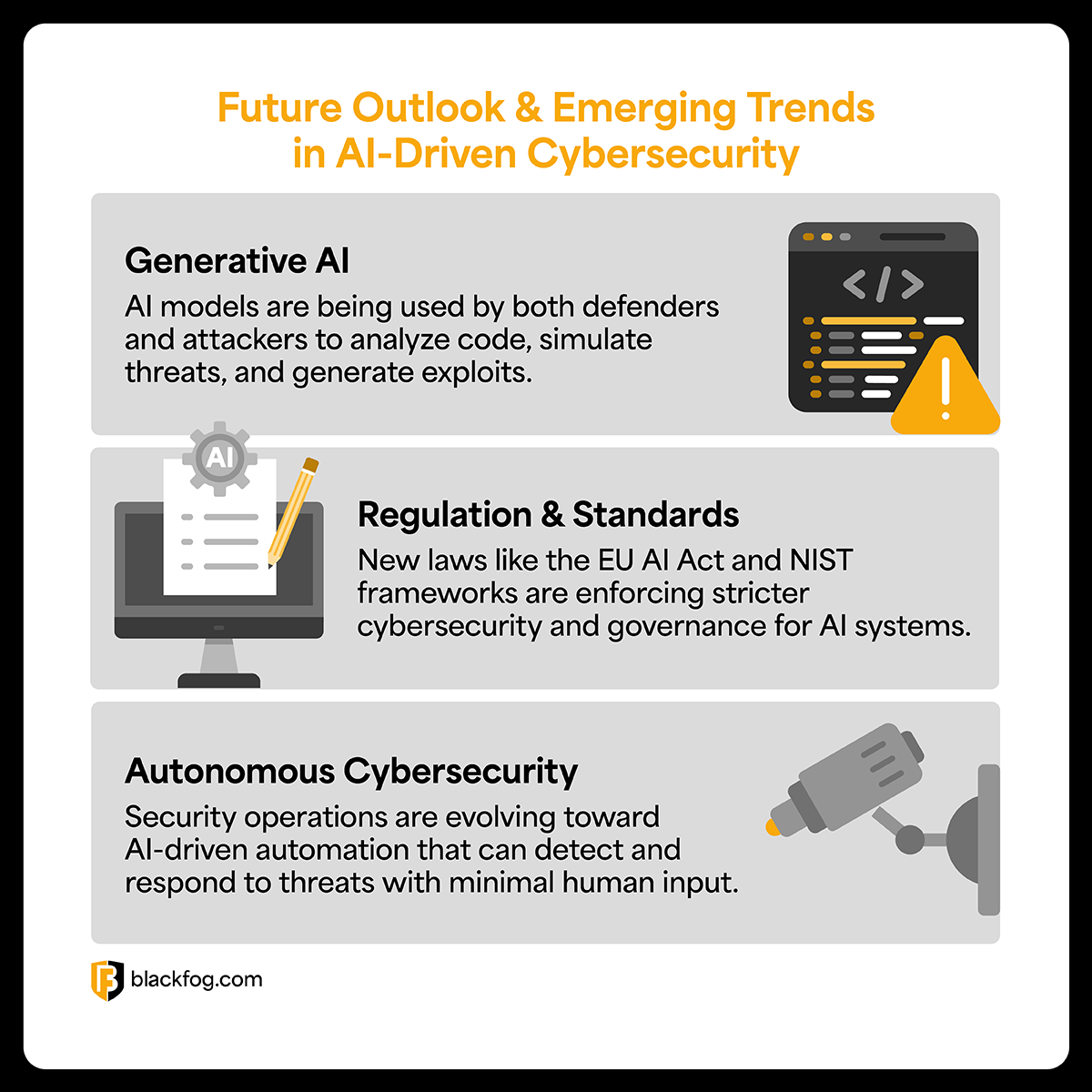
AI in Cybersecurity: The Good, the...
The Good – How AI Is Strengthening Cybersecurity AI systems are helping security teams with faster, smarter threat detection and response. New AI…
Read More
Key Network Questions
I wrote this on 7 December 2018 but never published it until today. The following are the “key network questions” which “would…
Read More
RSAC Fireside Chat: Operationalizing diverse security...
Catastrophic outages don’t just crash systems — they expose assumptions. Related: Getting the most from cyber insurance At RSAC 2025, I met with…
Read More
Key Features for Business Protection
As the threat landscape for businesses continues to grow more complex, ensuring robust cybersecurity has become a critical priority. With an increase in…
Read More
Google announces Sec-Gemini v1, a new...
Today, we’re announcing Sec-Gemini v1, a new experimental AI model focused on advancing cybersecurity AI frontiers. As outlined a year ago, defenders face…
Read More
Zero Day Security Exploits: How They...
Zero Day Security Exploits: How They Work and How to Stay Safe Zero day vulnerabilities are among the most dangerous threats businesses face…
Read More
My Last Email with W. Richard...
In the fall of 1998 I joined the AFCERT. I became acquainted with the amazing book TCP/IP Illustrated, Volume 1: The Protocols by…
Read More
What to Know Before You Commit
When it comes to cybersecurity, protecting your business from evolving threats is a top priority. One of the most effective ways to secure…
Read More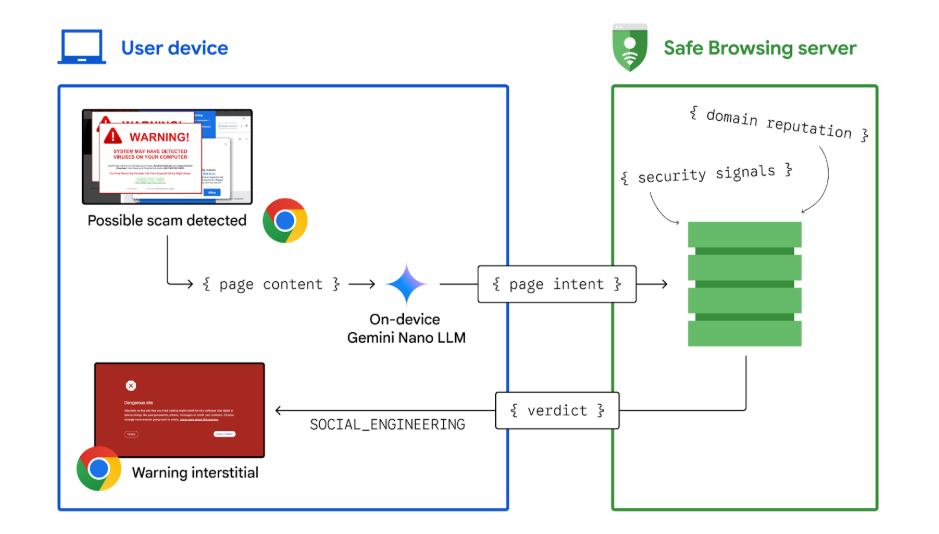
Using AI to stop tech support...
Posted by Jasika Bawa, Andy Lim, and Xinghui Lu, Google Chrome Security Tech support scams are an increasingly prevalent form of cybercrime, characterized…
Read More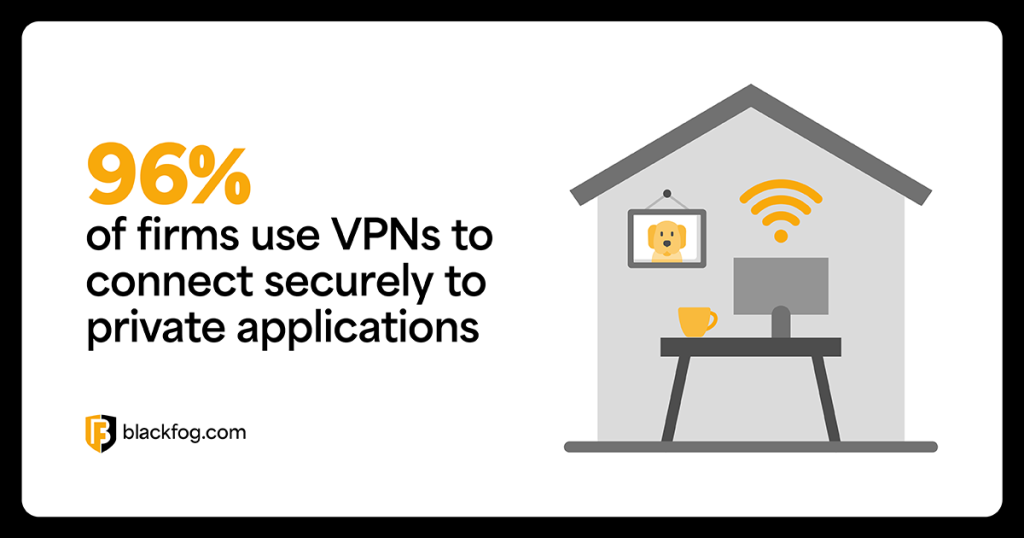
ZTNA vs VPN: Choosing the Right...
ZTNA vs VPN: Choosing the Right Secure Remote Access Solution Today’s businesses are facing a rapidly evolving threat landscape. Cyberattacks have grown more…
Read MoreCategories
Latest Articles