
Password Spraying Attacks Hit Entra ID...
Identity & Access Management , Security Operations Hackers Use TeamFiltration Penetration Testing Tool Prajeet Nair (@prajeetspeaks) • June 12, 2025 Image:…
Read More
Bridging the Security Knowledge Gap: Introducing...
The challenge of maintaining robust web application security often comes down to communication. Security teams frequently spend countless hours explaining WAF blocking decisions…
Read More
Top 10 Dynamic Application Security Testing...
What is DAST and how does it work? Dynamic application security testing (DAST) is a cybersecurity assessment method that analyzes running applications to…
Read More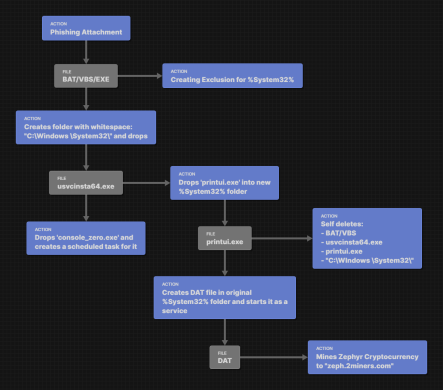
Hijacking Your Resources for Profit
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems, validating transactions on…
Read More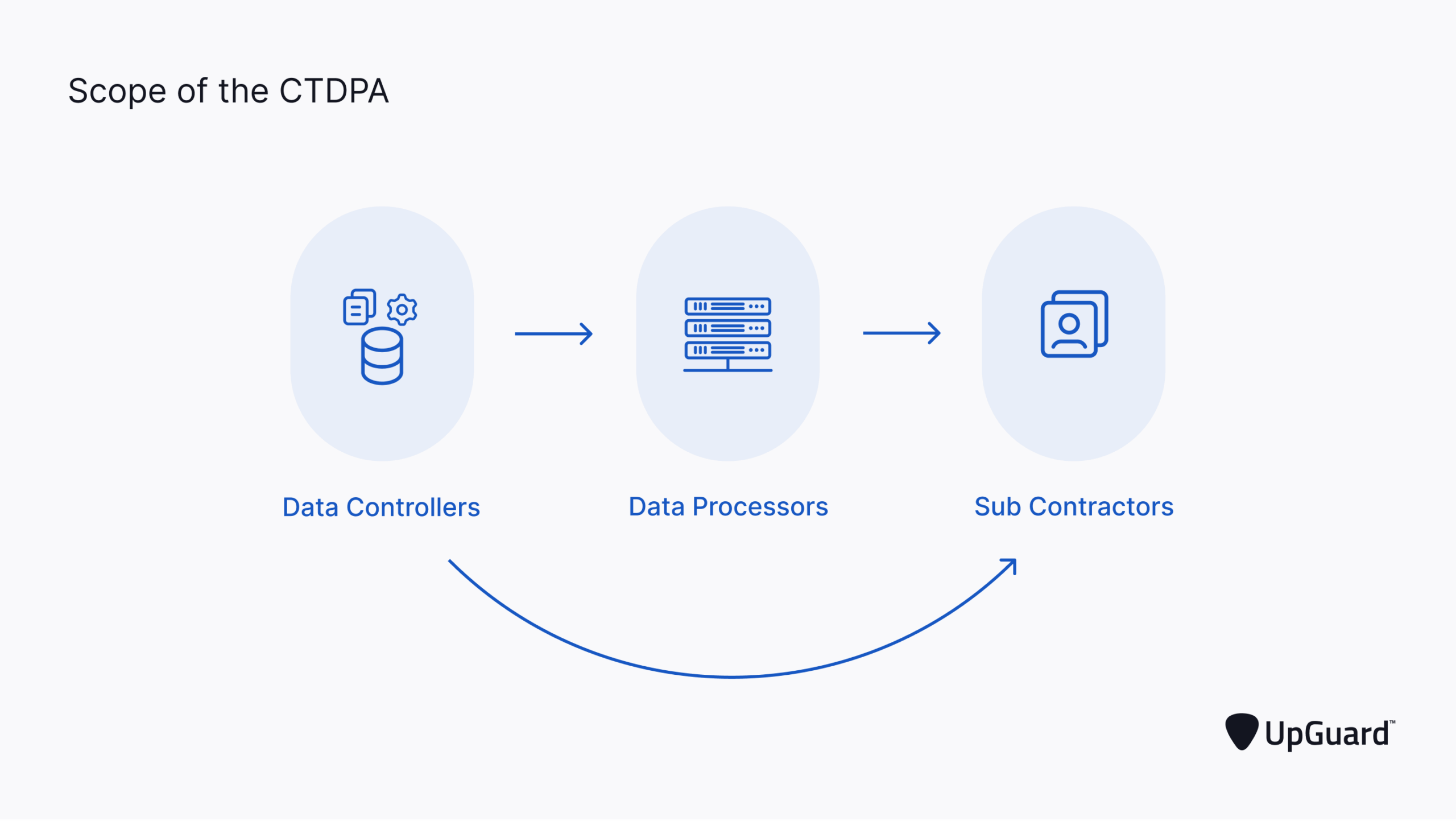
What is the Connecticut Data Privacy...
The Connecticut State Government signed the Connecticut Data Privacy Act (CTDPA) into law on May 10, 2022, and the law became effective on…
Read More
Heimdal’s New Monthly Cybersecurity Intelligence Webinar
At Heimdal, we know there’s no shortage of noise when it comes to cybersecurity news. But what MSP leaders and technical teams really…
Read More
SOC Prime and Anetac | SOC...
Announce Partnership to Optimize Identity Security and Combat Identity-Based Enterprise Threats Boston, MA, USA, 1st July 2025 – SOC Prime, the world’s leading…
Read More
Cybercrime crackdown disrupts malware, infostealers, marketplaces...
As spring gives way to summer, a wave of cybercrime crackdowns has taken root, with law enforcement and private security companies directing a…
Read More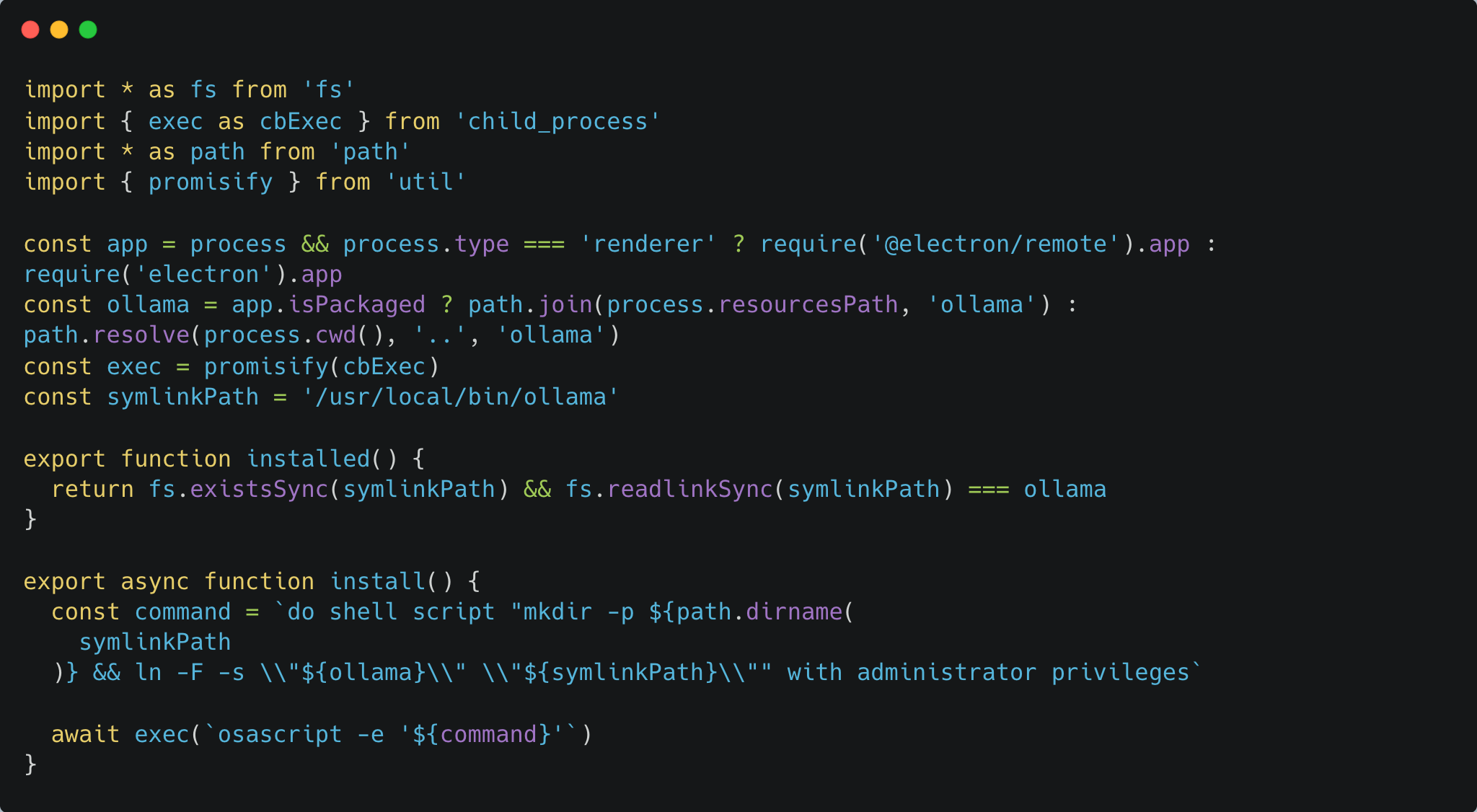
Hijacking Ollama’s Signed Installer for Code...
This blog post is part of an ongoing series exploring how AI related tools aimed at developers can be exploited to compromise their…
Read More
India’s First Global Computer Virus
In the cinematic tapestry of cybersecurity, where tales of intrigue and innovation collide, one story emerges from the shadows of the past. It’s…
Read MoreCategories
Latest Articles