
Small Businesses Create Big Impact: NIST...
This week we’re celebrating National Small Business Week—which recognizes and celebrates the small and medium-sized business (SMB) community’s significant contributions to the nation. SMBs…
Read More
AI Dilemma: Emerging Tech as Cyber...
AI is fundamentally transforming the modern world. It offers previously out-of-reach opportunities for business leaders to anticipate market trends and make better decisions.…
Read More
Public exploits released for Citrix Bleed...
Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is easily…
Read More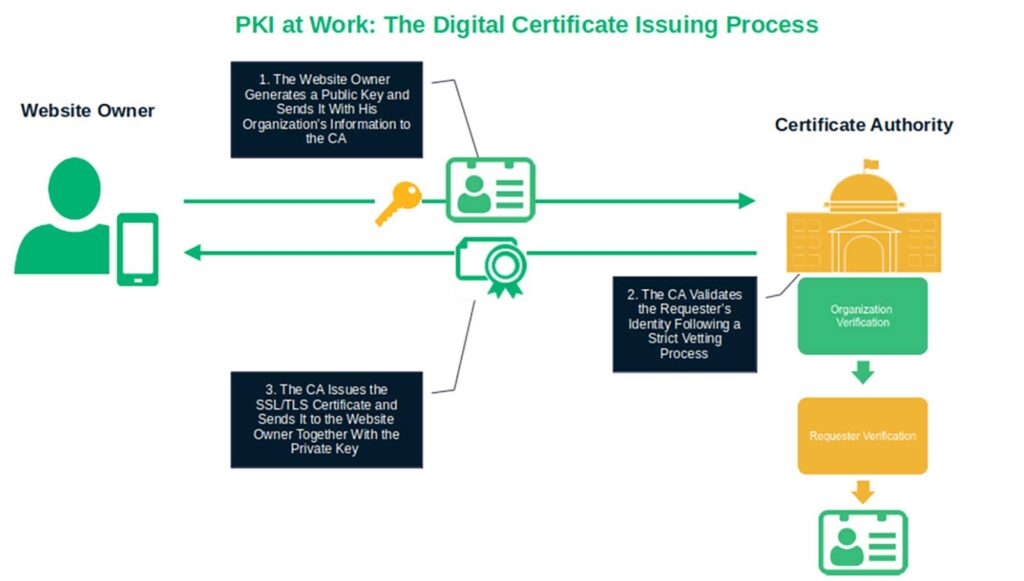
How Does PKI Work? A Look...
You enjoy the benefits of PKI every day, but have you ever wondered what goes on behind the scenes? Learn how public key…
Read More
when you don’t respond to a...
A few years ago I wrote a short article about the Titanic, and the lessons for cyber risk management. However, there’s arguably a…
Read More
Using AI to Write Deterministic Code...
Avoid blanket statements — use the right tool for the job ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code.…
Read More
Cybersecurity Compliance in South Africa
A Continued Cycle South Africa has had a slow approach to compliance with the government regulations and laws set in place. This problem…
Read More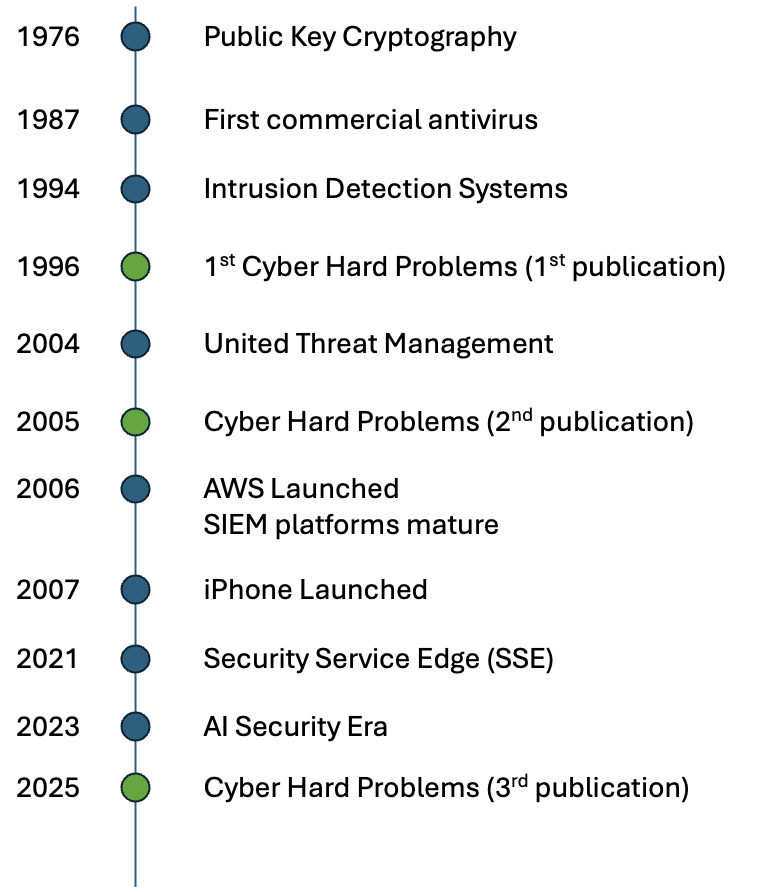
Cisco Contributes to Cyber Hard Problems...
While Cisco often focuses on business growth and market leadership, our most rewarding work happens when we set those metrics aside. These projects…
Read More
The Impact of Artificial Intelligence on...
Credit: NICE The NICE Workforce Framework for Cybersecurity (NICE Framework) was revised in November 2020 as NIST Special Publication 800-181 rev.1 to enable…
Read More
Alleged Chinese hacker tied to Silk...
A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which responsible…
Read MoreCategories
Latest Articles