
New Android TapTrap attack fools users...
A novel tapjacking technique can exploit user interface animations to bypass Android’s permission system and allow access to sensitive data or trick users into…
Read More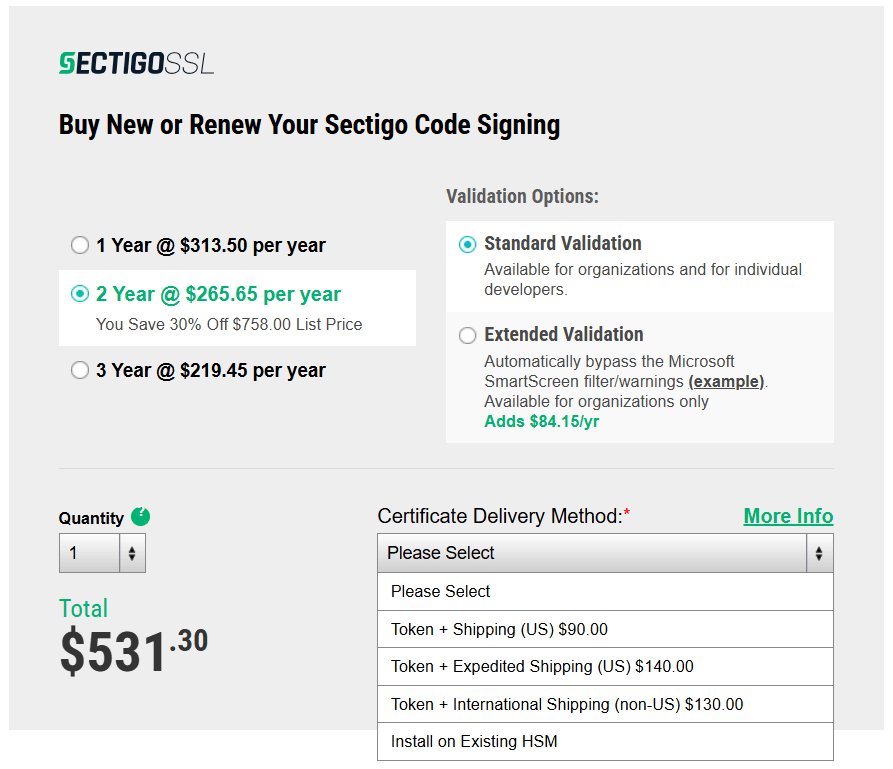
How to Use Google Cloud KMS...
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a Sectigo Code Signing…
Read More
The Real Meaning Behind the Jargon...
Cyber security is often conflated with the term confidentiality, but that is not correct. Traditionally, professionals tend to define it as being about…
Read More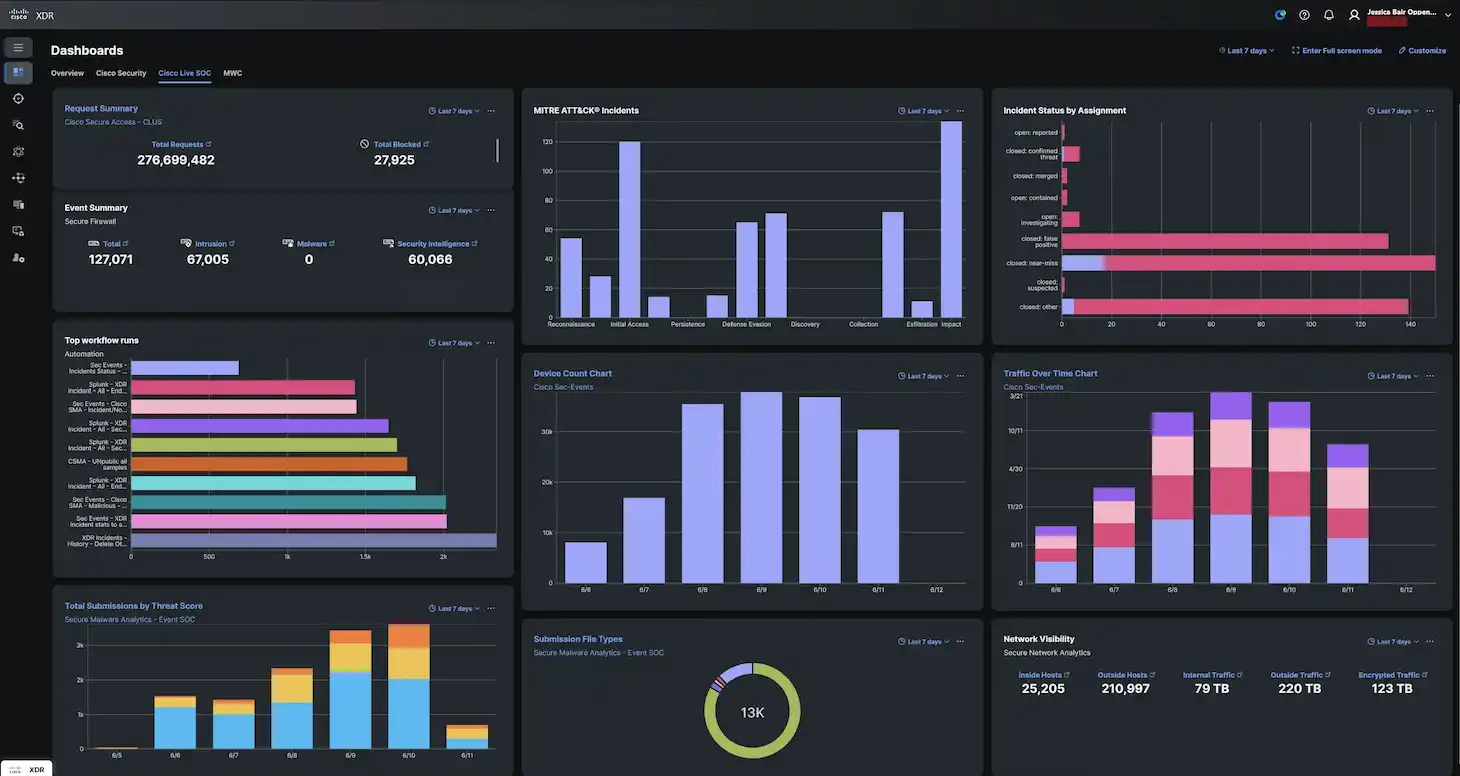
Cisco Live San Diego Case Study:...
Additional Post Contributors: Mindy Schlueter On June 11, the Cisco Live San Diego SOC received a Cisco XDR Incident triggered by two Cisco…
Read More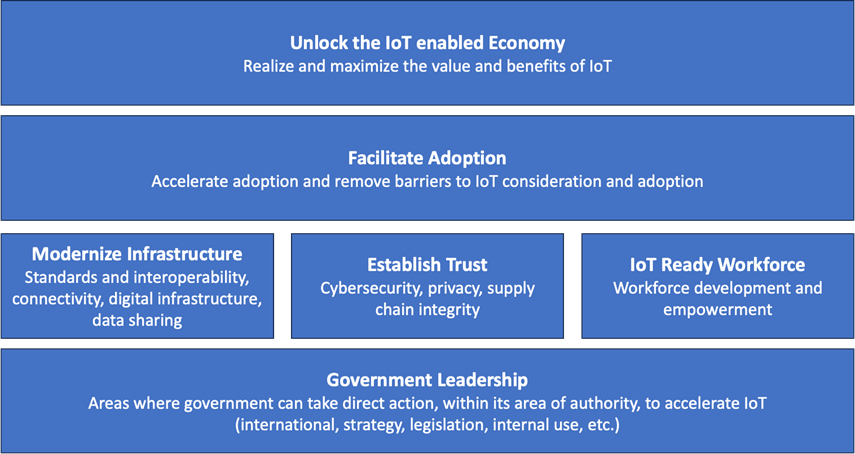
IoT Assignment Completed! Report on Barriers...
The 16 members of the NIST-managed Internet of Things (IoT) Advisory Board have completed their report on barriers to the U.S. receiving the…
Read More
An Investigation of AWS Credential Exposure...
Misconfigured or overly privileged containers in Kubernetes environments can facilitate unauthorized access to sensitive AWS credentials, exposing the environment to privilege escalation and…
Read More
M&S confirms social engineering led to...
M&S confirmed today that the retail outlet’s network was initially breached in a “sophisticated impersonation attack” that ultimately led to a DragonForce ransomware…
Read More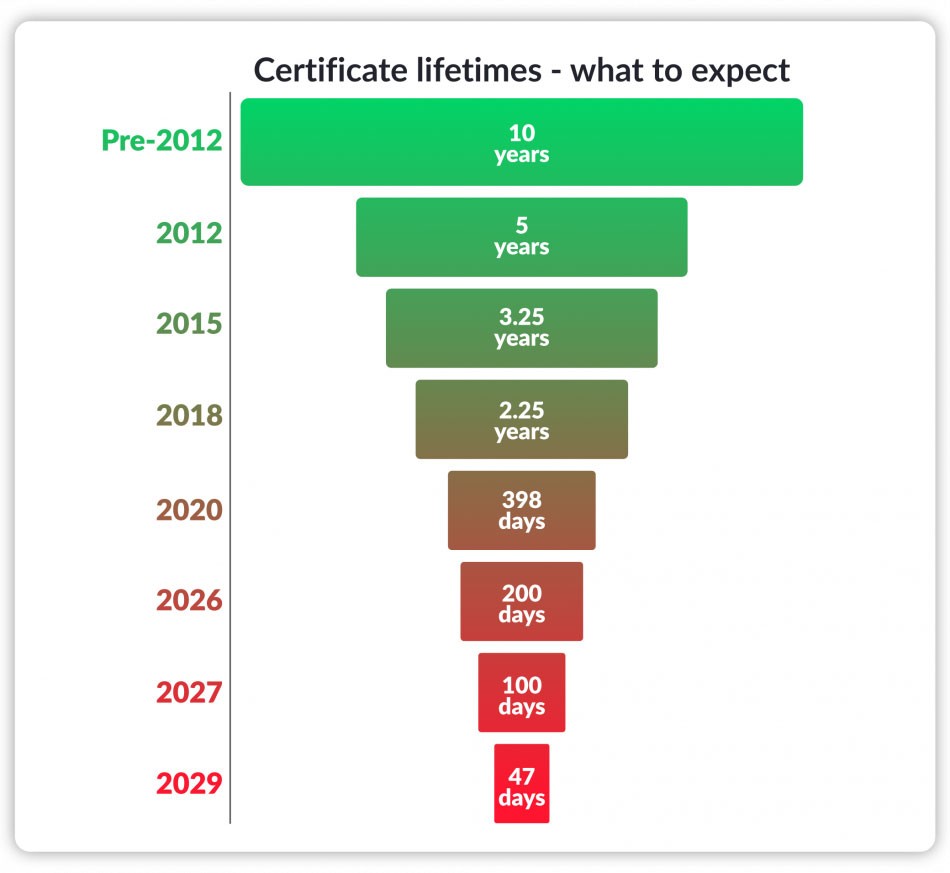
Industry Leaders Approve the Move to...
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate validity period reduction…
Read More
Why We Must Embrace Risk and...
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for the thrill of…
Read More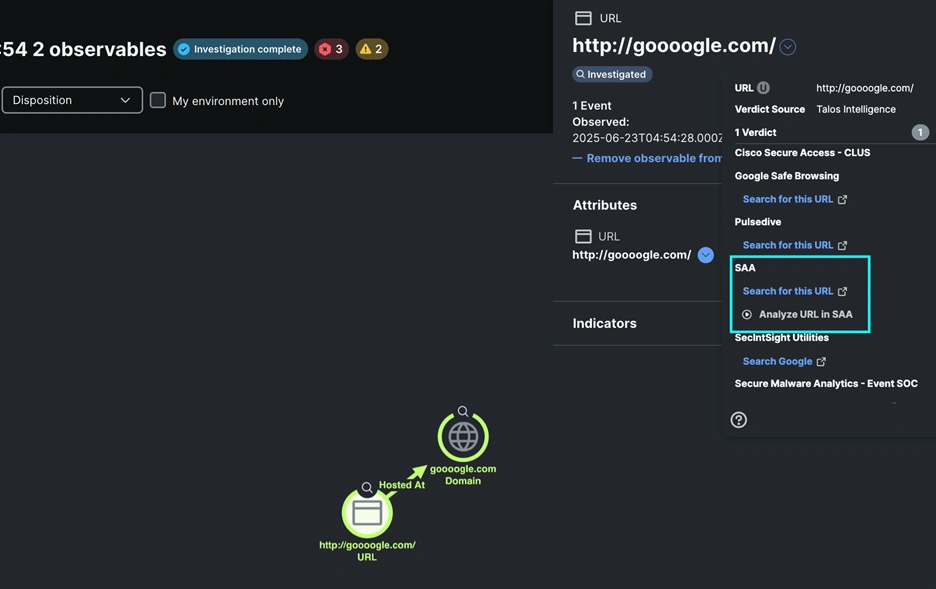
Building an XDR Integration With Splunk...
Cisco XDR is an infinitely extensible platform for security integrations. Like the maturing SOCs of our customers, the event SOC team at Cisco…
Read MoreCategories
Latest Articles