
Why Nation-States Are Hacking the Power...
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖, In Part 1…
Read More
Best SOC as a Service Providers...
When cyber threats strike from every corner of your infrastructure, turning to experienced SOC as a service providers equips your business with the…
Read More
Scaling Sophos to $1B+ revenue and...
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company that has quietly…
Read More
Enhancing Endpoint Visibility Through a Unified...
It’s easy to miss critical signs when endpoint tools work in isolation. When a laptop shows unusual behavior but its network or cloud…
Read More
When the Grid Gets Smart, the...
Hello Cyber Builders 🖖 This is the third and final post in my series on cybersecurity and power grids. Today, I want to…
Read More
UnderDefense Secures Top Honor at the...
We’re proud of being a winner at the 2025 Global Infosec Awards for MDR Service, recognizing our commitment to advancing cybersecurity innovation and…
Read More
The Generative AI Revolution: Trends That...
The Generative AI Revolution: Trends That Will Shape Your 2025 Strategy Hey there, tech-savvy reader! Let’s admit it—Generative AI is no longer some…
Read More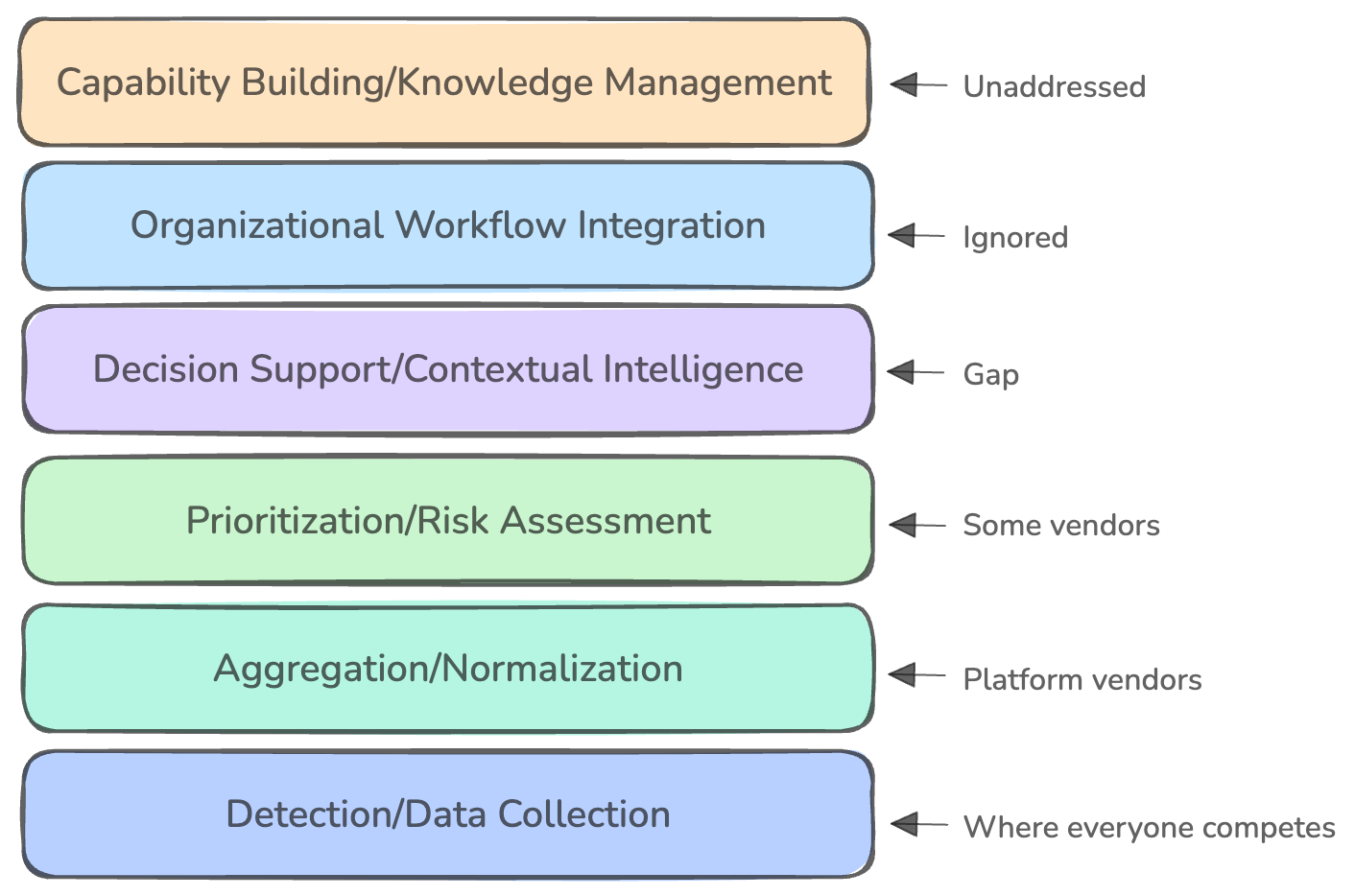
why theory doesn’t match practice
This week, Venture in Security is excited to feature a guest article from Nielet D’Mello. Nielet is a security engineer with nearly a…
Read More
Endpoint Vulnerability Remediation: From Alert to...
With the boom of cloud usage and AI, organizations have been facing an increase in cybersecurity challenges due to which they realize the…
Read More
The Only AI Tool AppSec Needs....
Software quietly runs the systems we rely on—our banks, logistics, communication, and cars. But for many AppSec teams, that software is a tangle…
Read MoreCategories
Latest Articles