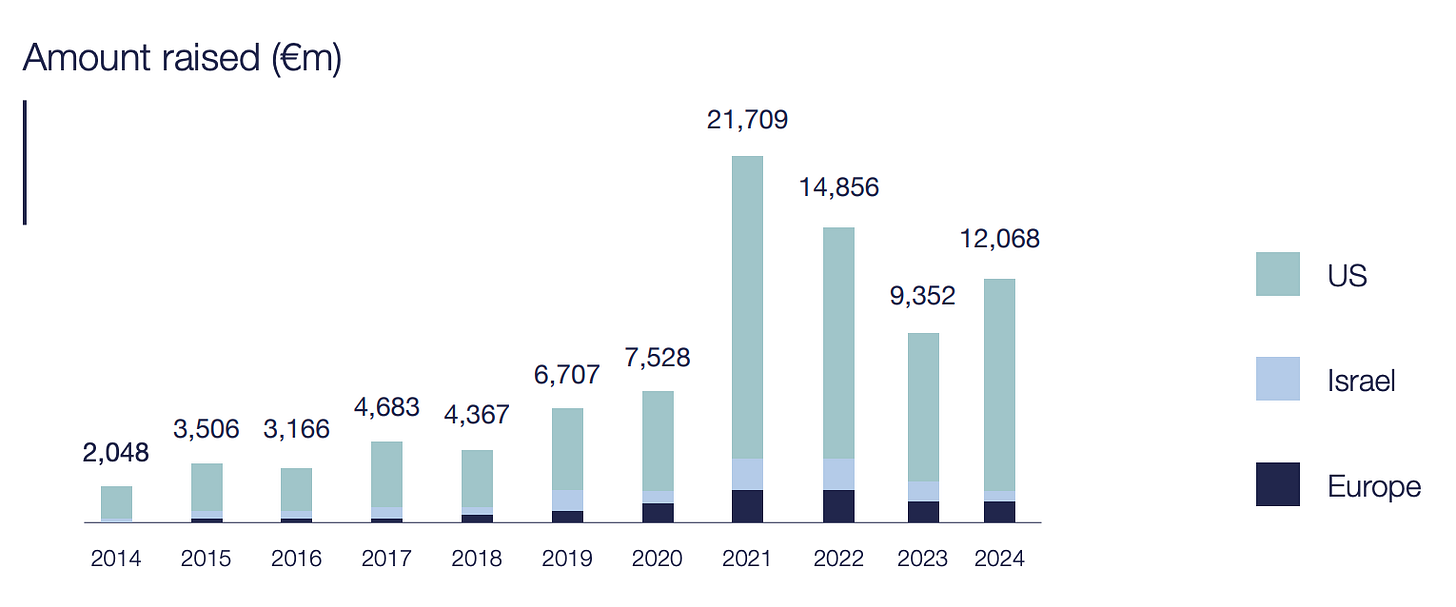
Fewer Cheques, Tougher Checks: Cyber VC...
Hello Cyber Builders 🖖 Cybersecurity is at the top of everyone’s mind, and AI brings more opportunities and threats at the same time.…
Read More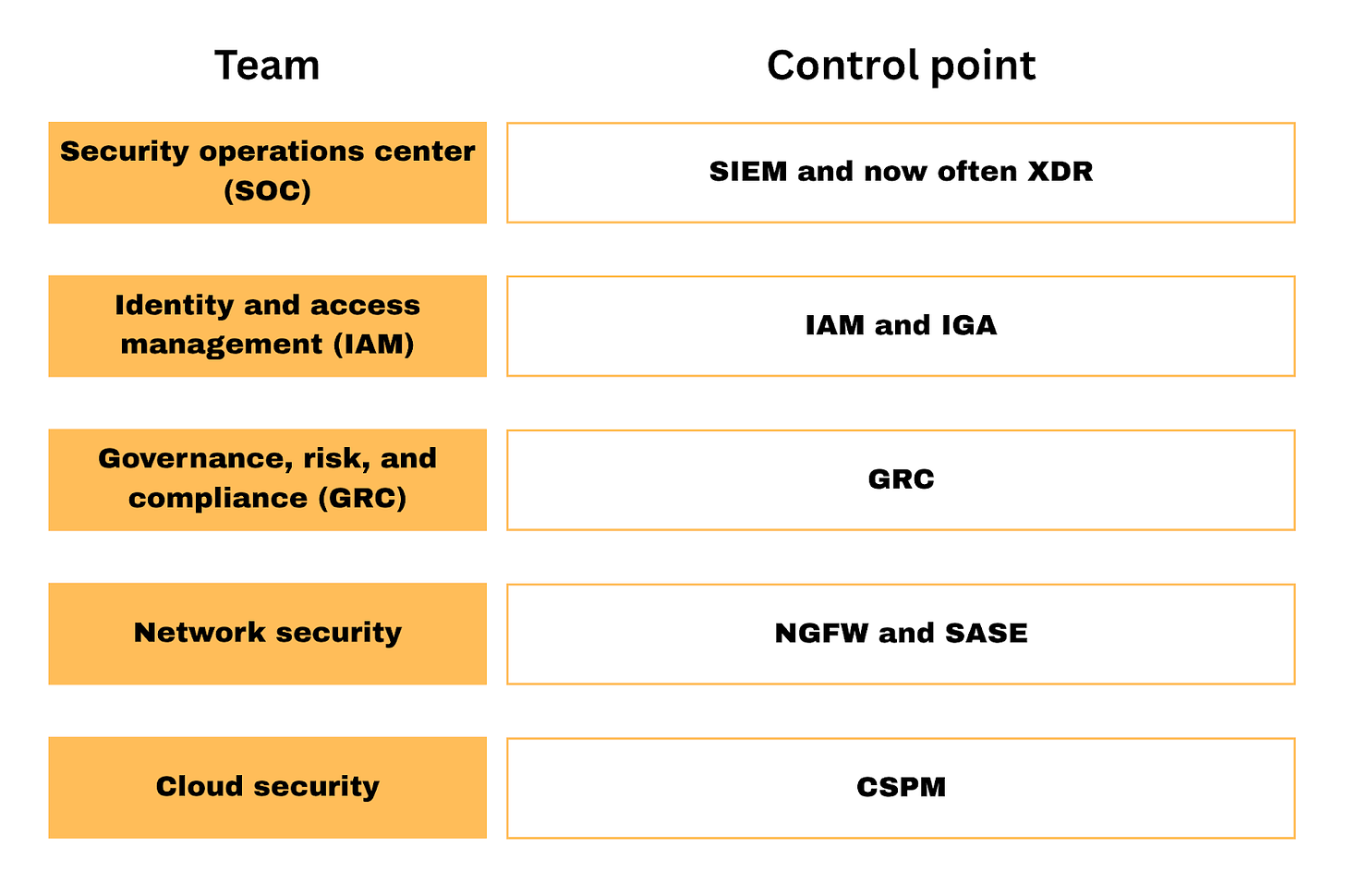
Owning the control point in cybersecurity
Dave Yuan, a venture capitalist at Tidemark who has spent over 20 years investing, likes to discuss the concept of a “control point.”…
Read More
6 Dimensions to Cut Through the...
Hello CyberBuilders 🖖 Let’s talk AI security (don’t stop reading here, give me 2 mins!) It’s the new obsession in the cybersecurity startup…
Read More
Best MSSP Providers You Can Trust
Managed security services providers, or MSSP providers for short, have become essential allies to businesses in the face of soaring cyber attacks. These…
Read More
Competing with layer zero in cybersecurity
I am not aware of anyone who has previously attempted to define the concept of layer zero in security. Chances are, you will…
Read More
How Modern XDR Platforms Spot Insider...
Most people imagine hackers, ransomware, or harmful software when they hear about cybersecurity threats. However, a quieter danger often comes from within —…
Read More
My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power infrastructure during early…
Read More
G2 Spring 2025 Report Awards UnderDefense...
We’re proud to share exciting news! UnderDefense has been recognized as a trustworthy, first-rate cybersecurity service provider with 12 new badges from G2.…
Read More
10 immutable laws of security, 25...
Back in 2000, the Microsoft Security Response Center released an article titled “10 Immutable Laws of Security“, describing what they believed were some…
Read More
How to Achieve DDoS Defense with...
DDoS Defense with up-to-the-minute network analysis has become crucial as these attacks have disrupted network security for almost 20 years. The landscape changed…
Read MoreCategories
Latest Articles