
What to Know Before You Commit
When it comes to cybersecurity, protecting your business from evolving threats is a top priority. One of the most effective ways to secure…
Read More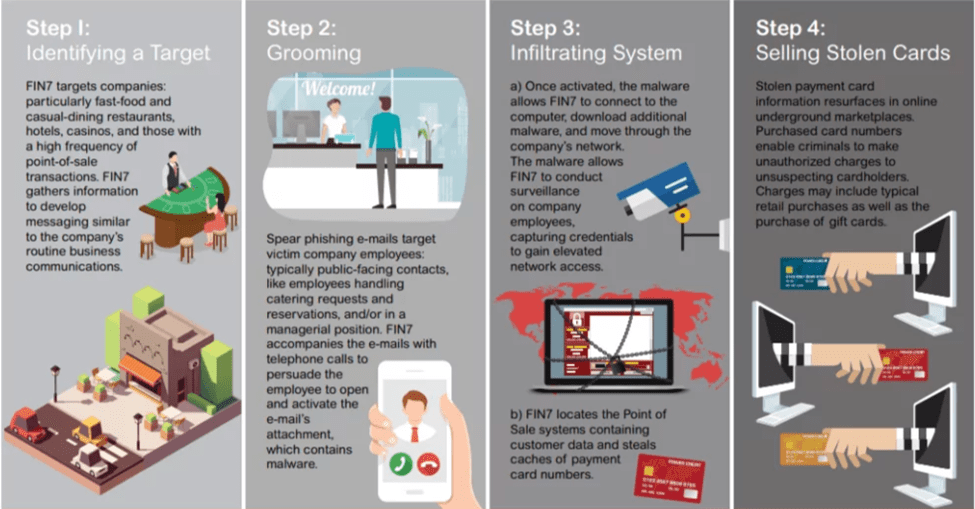
Automated DFIR Rethinking the SOC
Automated DFIR Rethinking the SOC This article is brought to you by Binalyze and is also available on their web site In December…
Read MoreMalware sharing, data wiping and exploits
ESET experts discuss Sandworm’s new data wiper, relentless campaigns by UnsolicitedBooker, attribution challenges amid tool-sharing, and other key findings from the latest APT…
Read More
How to Migrate SVN to GIT...
Today I’d like to share my solution for a common problem a lot of IT companies experience when finally moving from Subversion (SVN)…
Read More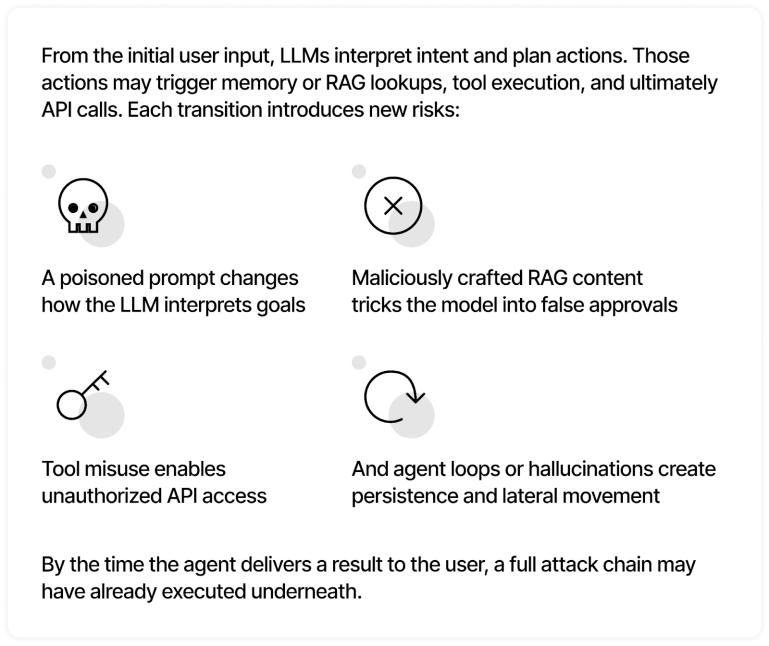
Mapping the Future of AI Security
AI security is one of the most pressing challenges facing the world today. Artificial intelligence is extraordinarily powerful, and, especially considering the advent…
Read More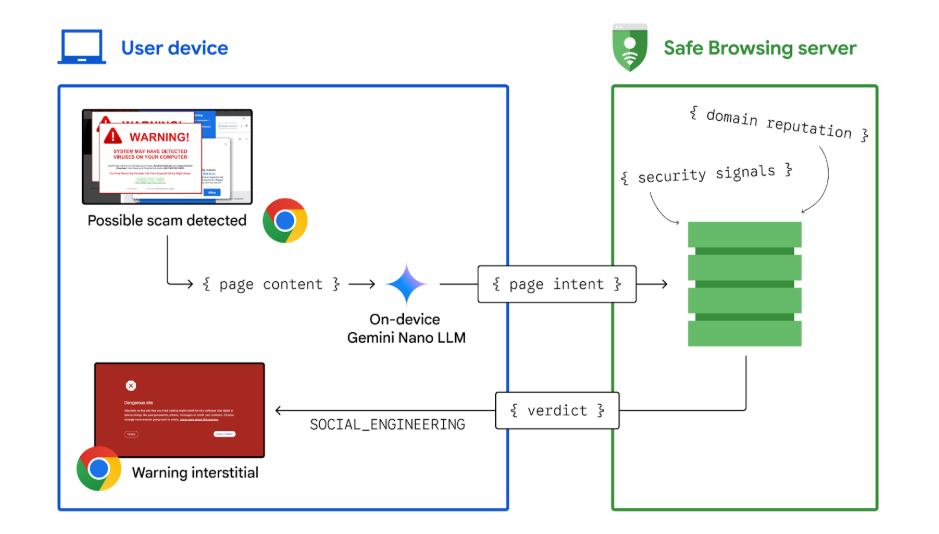
Using AI to stop tech support...
Posted by Jasika Bawa, Andy Lim, and Xinghui Lu, Google Chrome Security Tech support scams are an increasingly prevalent form of cybercrime, characterized…
Read More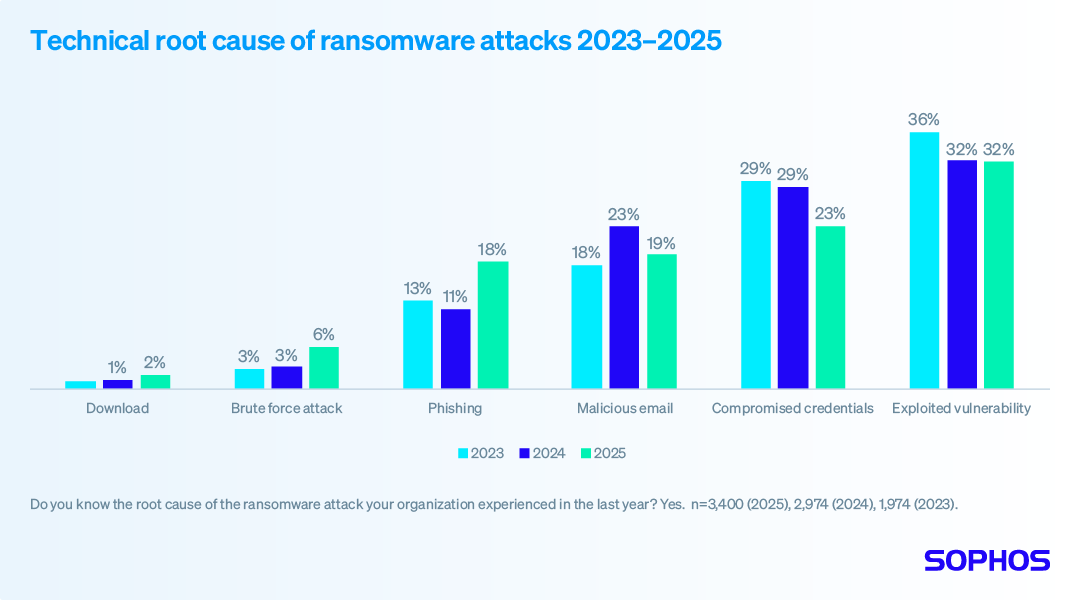
The State of Ransomware 2025 –...
The sixth annual Sophos State of Ransomware report provides fresh insights into the factors that led organizations to fall victim to ransomware and…
Read More
Not Every Task Deserves One
Hello CyberBuilders 🖖 This week, I’m diving into a brilliant video from Mr. Zhang at Anthropic. You might know him as the guy…
Read More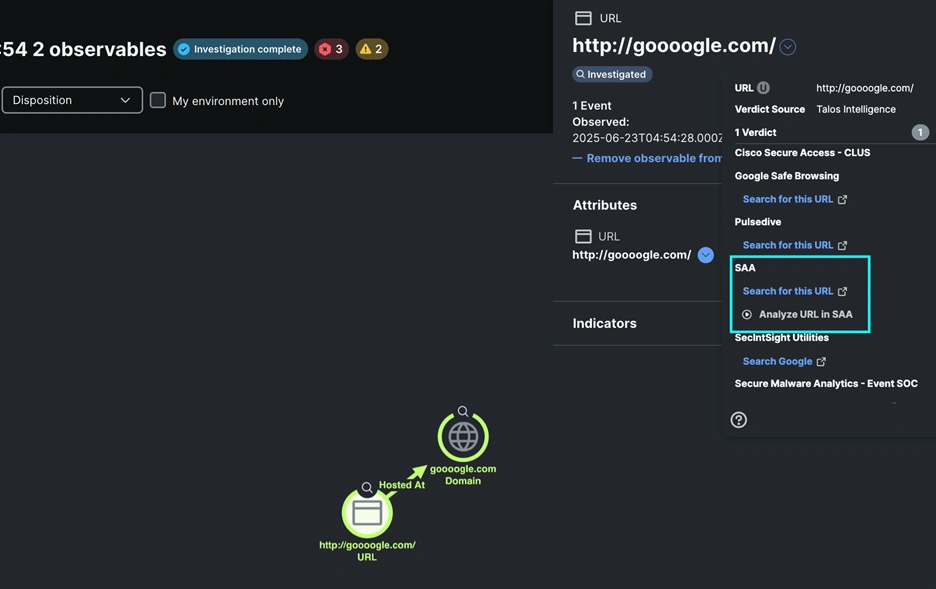
Building an XDR Integration With Splunk...
Cisco XDR is an infinitely extensible platform for security integrations. Like the maturing SOCs of our customers, the event SOC team at Cisco…
Read More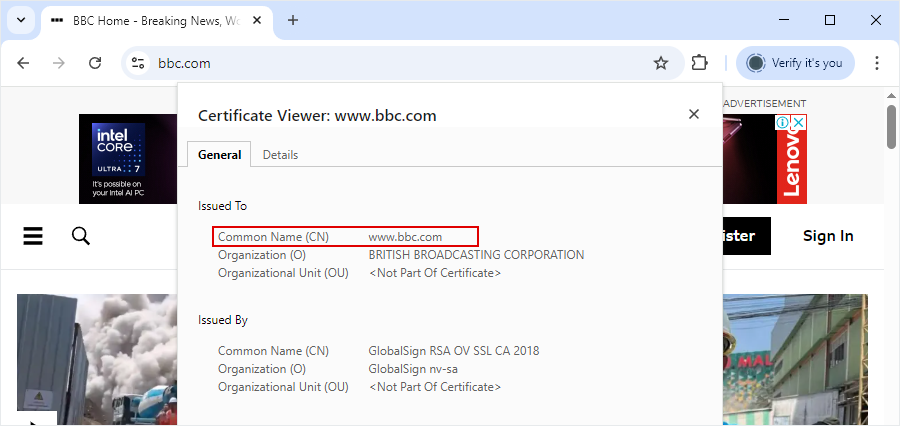
Standard SSL vs. Wildcard SSL Certificate
Securing your domain is a priority – whether you run a personal website, a business site, an e-commerce store, or even a government…
Read MoreCategories
Latest Articles