The Role of Automation – Data...
The Saudi Arabian Personal Data Protection Law (PDPL) marks a significant milestone in the kingdom’s efforts to protect individuals’ personal data. For businesses…
Read More
July Patch Tuesday: 14 critical Microsoft...
NOTLogon vulnerability Microsoft also issued a patch for CVE-2025-47978, a denial-of-service (DoS) vulnerability in Microsoft’s Netlogon protocol, a core component of all Windows…
Read More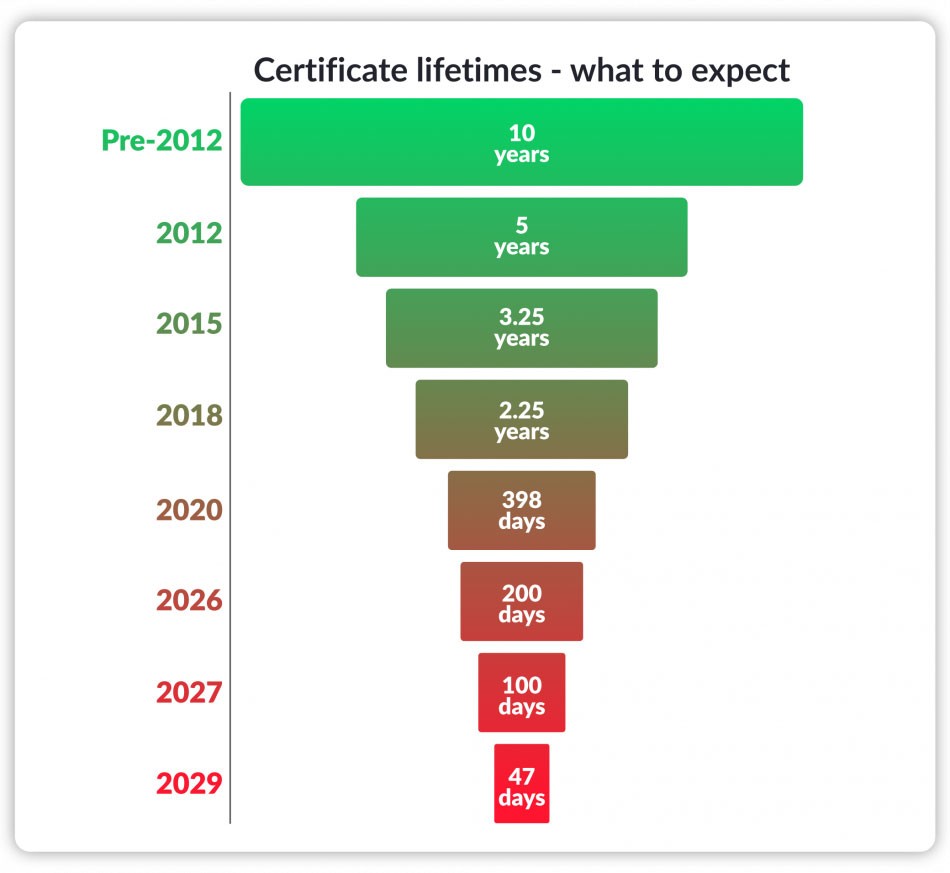
Industry Leaders Approve the Move to...
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate validity period reduction…
Read More
Webinar: Driving value and security to...
29 April 2025, 10:30 CET As a MSSP, delivering value and security to your customers is at the heart of your business.…
Read More
Karen Johnson’s Scam Project Is a...
Karen Johnson is a catfisher-turned-scam avoidance coach turned–you guessed it–catfishing victim. The scam that got her is a classic, opening the door to…
Read More
Weekly Update 455
The bot-fighting is a non-stop battle. In this week's video, I discuss how we're tweaking Cloudflare Turnstile and combining more attributes around how…
Read More
IKEA effect in cybersecurity or why...
Security professionals take a lot of pride in the things they build – playbooks, detections, automations, open source tools, and more. Sharing these…
Read More
Why We Must Embrace Risk and...
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for the thrill of…
Read More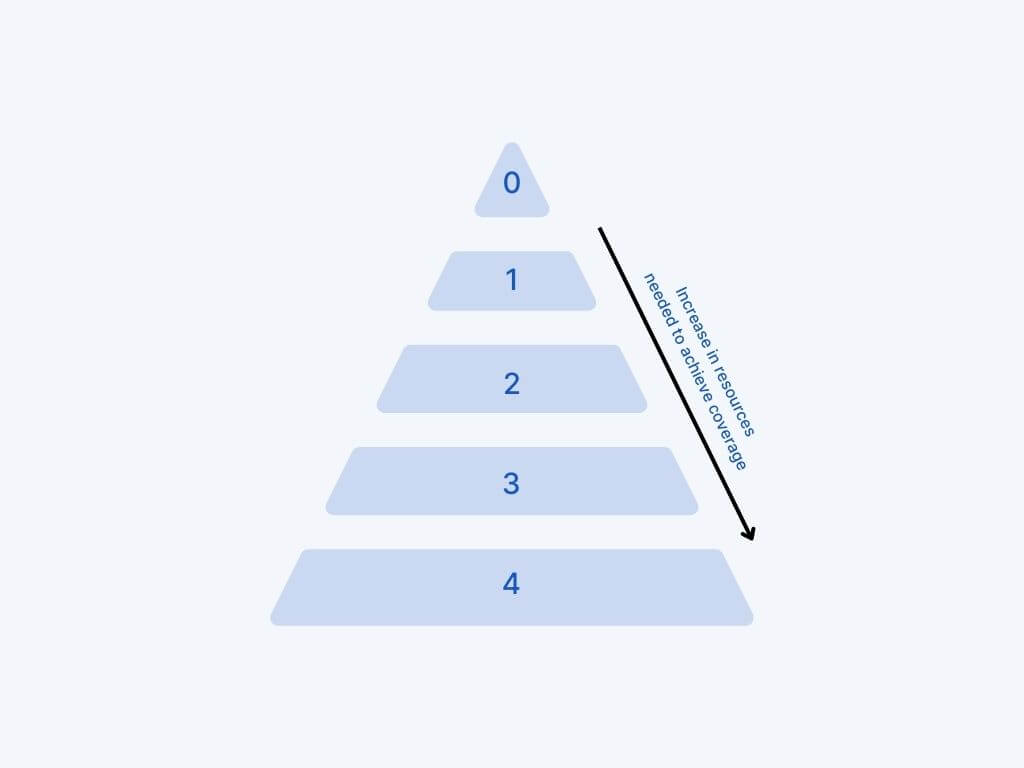
What is IEC/ISA 62443-3-3:2013? Cybersecurity &...
The International Society of Automation (ISA) and the International Electrotechnical Commission (IEC) started creating the 62443 series of standards in 2002. The series,…
Read More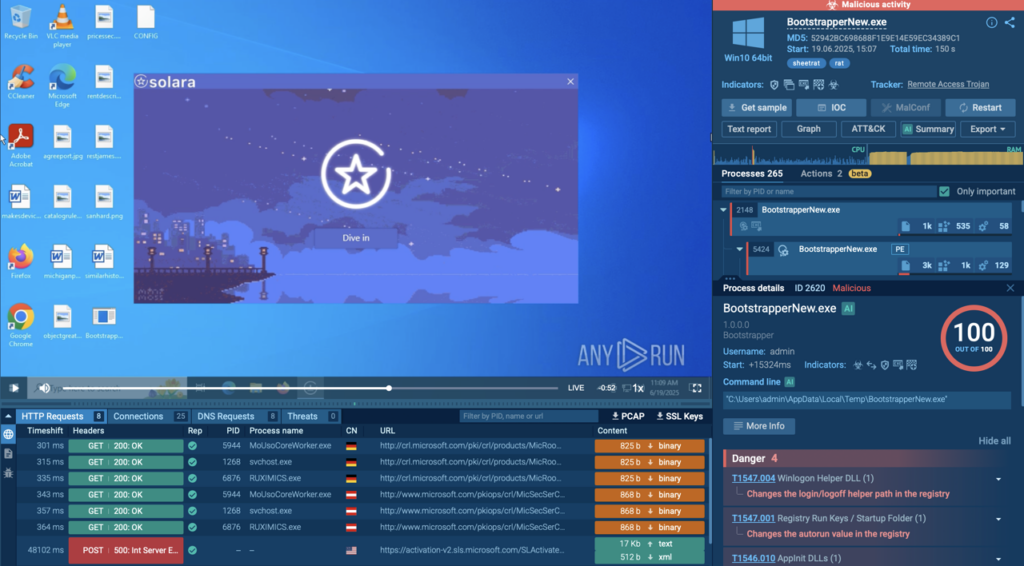
How to Spot Registry Abuse by...
HomeCybersecurity Lifehacks How to Spot Registry Abuse by Malware: Examples in ANY.RUN Sandbox When malware infiltrates a system, it doesn’t always make noise.…
Read MoreCategories
Latest Articles