
Recent Cyberattacks Highlight Network Vulnerabilities –...
Recent Cyberattacks Highlight Network Vulnerabilities The network is a critical component of enterprise security yet it’s often overlooked by CISOs and security teams.…
Read More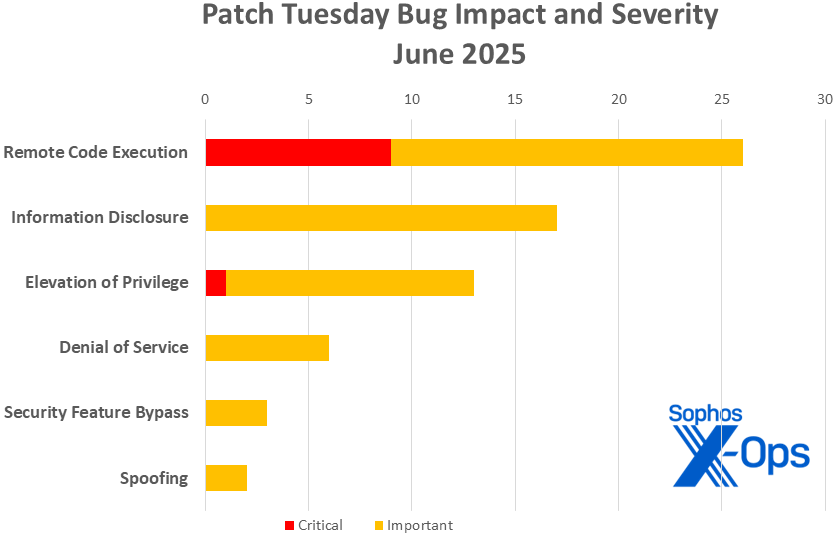
June Patch Tuesday digs into 67...
.Microsoft on Tuesday released 67 patches affecting 12 product families. Ten of the addressed issues, five involving 365 and Office and one involving…
Read More
The Rise of Agentic AI: Uncovering...
In our first post, we introduced the world of AI web agents – defining what they are, outlining their core capabilities, and surveying…
Read More
Google announces Sec-Gemini v1, a new...
Today, we’re announcing Sec-Gemini v1, a new experimental AI model focused on advancing cybersecurity AI frontiers. As outlined a year ago, defenders face…
Read More
The Importance of Effective Joint Commission...
The Joint Commission standards play a crucial role in maintaining high levels of care and safety in healthcare settings. These standards provide guidelines…
Read More
Over 17,000 Fake News Websites Caught...
A newly released report by cybersecurity firm CTM360 reveals a large-scale scam operation utilizing fake news websites—known as Baiting News Sites (BNS)—to deceive…
Read More
A perfect cybersecurity startup idea
Having learned a ton about the state of the industry over the past several years, and having been through the process of ideation,…
Read More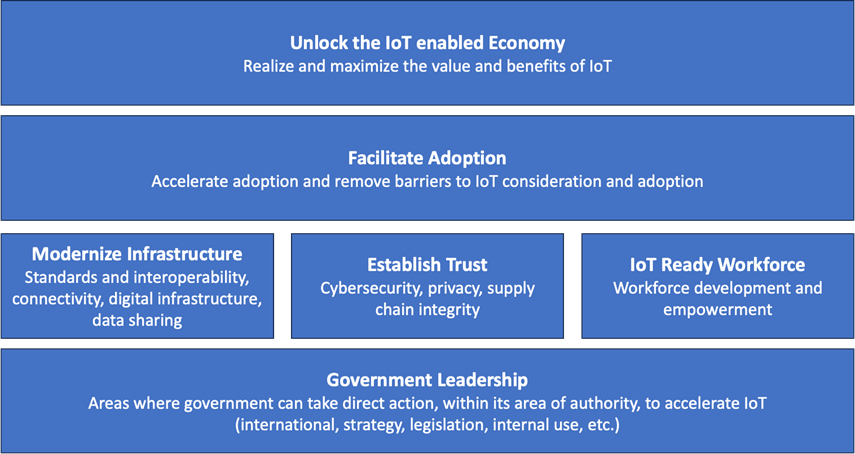
IoT Assignment Completed! Report on Barriers...
The 16 members of the NIST-managed Internet of Things (IoT) Advisory Board have completed their report on barriers to the U.S. receiving the…
Read More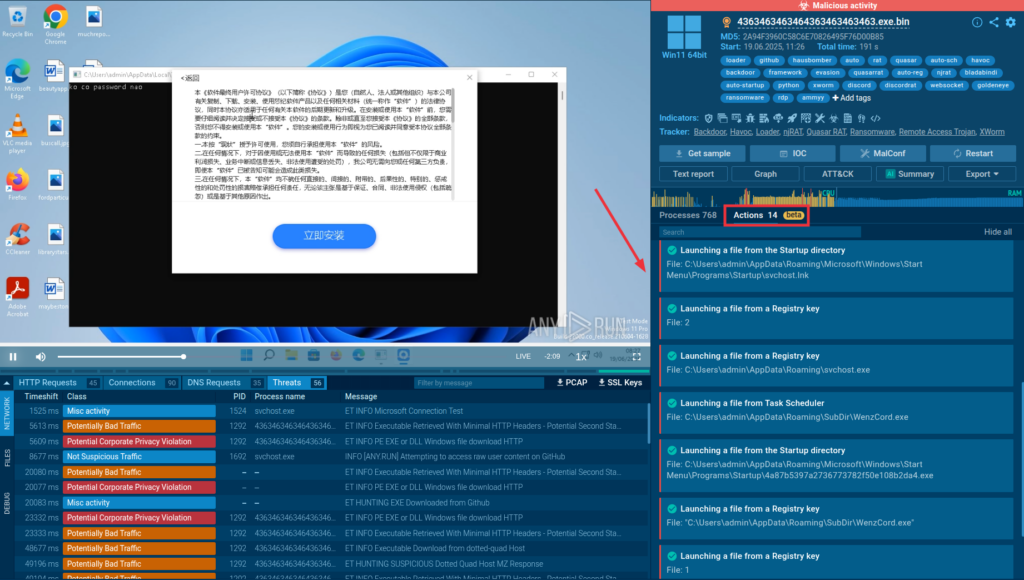
Simplify Threat Analysis and Detection with...
HomeService Updates Simplify Threat Analysis and Boost Detection Rate with Detonation Actions Threat analysis is a complex task that demands full attention, especially…
Read More
Zero Day Security Exploits: How They...
Zero Day Security Exploits: How They Work and How to Stay Safe Zero day vulnerabilities are among the most dangerous threats businesses face…
Read MoreCategories
Latest Articles