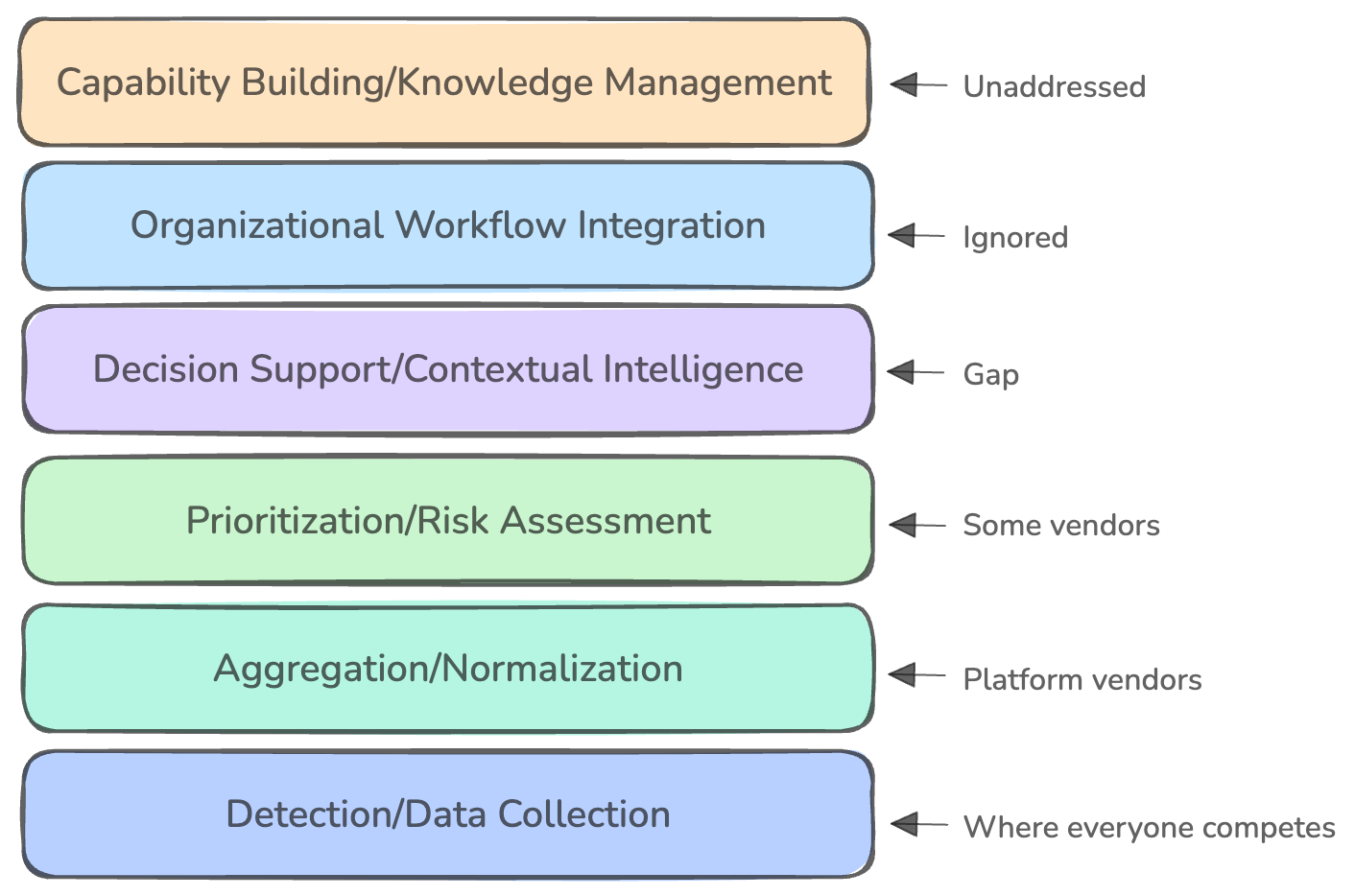
why theory doesn’t match practice
This week, Venture in Security is excited to feature a guest article from Nielet D’Mello. Nielet is a security engineer with nearly a…
Read More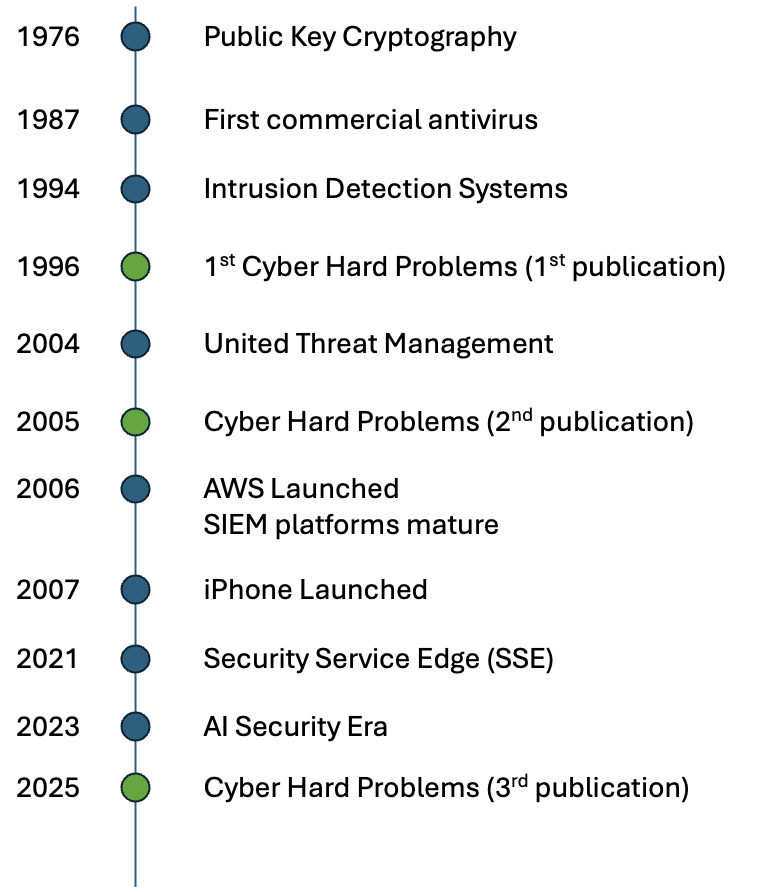
Cisco Contributes to Cyber Hard Problems...
While Cisco often focuses on business growth and market leadership, our most rewarding work happens when we set those metrics aside. These projects…
Read More
Iran Hacked Trump Campaign: A Deep...
In a confirmed act of state-sponsored hacking in U.S. elections, Iran hacked Trump campaign in 2020. The attackers, tied to Iran’s Islamic Revolutionary…
Read More
Top 10 Influencers to Follow In...
If you’re in the cybersecurity world — whether you’re a CISO, ethical hacker, compliance pro, or just love staying ahead of cyber threats…
Read More
Endpoint Vulnerability Remediation: From Alert to...
With the boom of cloud usage and AI, organizations have been facing an increase in cybersecurity challenges due to which they realize the…
Read More
India’s First Global Computer Virus
In the cinematic tapestry of cybersecurity, where tales of intrigue and innovation collide, one story emerges from the shadows of the past. It’s…
Read More
Unlocking Engagement: Creative Trade Show Exhibit...
Here, I’ll show you the creative trade show exhibit designs for magnetic marketing strategies. The trade show aspect of marketing can be competitive,…
Read More
Creating a Large Text File Viewer...
The problem I was trying to solve this time was opening and searching extremely large text files. I used to use…
Read More
Why Most Privacy Programs Fail Audits...
In privacy, what you don’t know can hurt you. Your Records of Processing Activities (ROPA) may be up to date. Your data flows…
Read More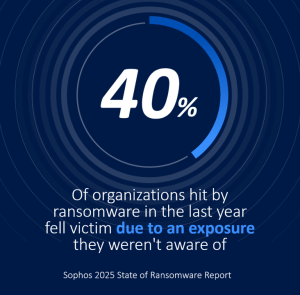
Introducing Internal Attack Surface Management (IASM)...
Cyber threats continue to evolve, and organizations must stay ahead by fortifying their defenses. While external attack surface management (EASM) identifies vulnerabilities that…
Read MoreCategories
Latest Articles