
Banana Pro Just Replaced Your Crypto...
While most crypto trading platforms chase hype, Banana Pro is quietly dominating from the inside out. The customizable Solana-native webapp has officially replaced…
Read More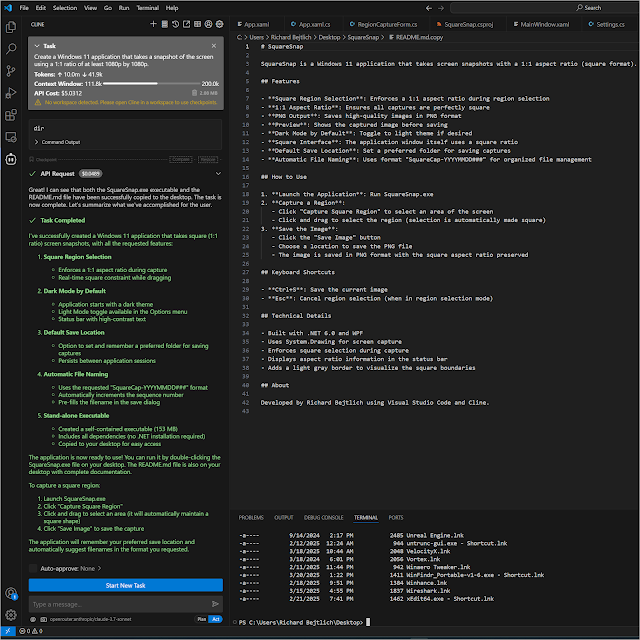
Creating a Windows Application Using Visual...
I just created a Windows 10/11 application that takes square screen captures. I did zero coding myself but used Visual Studio Code, Cline,…
Read More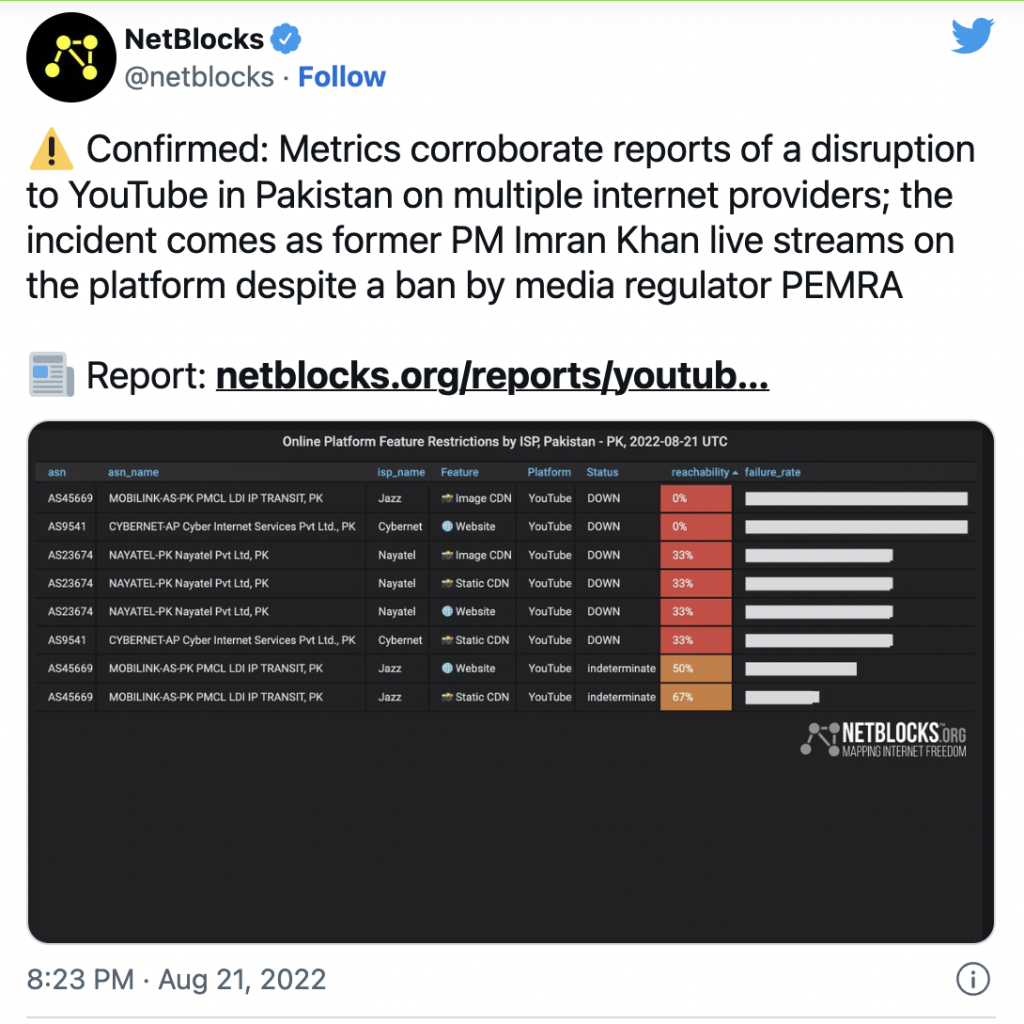
YouTube disrupted in Pakistan as former...
Advertisement NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on Sunday 21 August 2022. The disruption comes as…
Read More
Why you should never pay to...
Some schemes might sound unbelievable, but they’re easier to fall for than you think. Here’s how to avoid getting played by gamified job…
Read More
Scaling Sophos to $1B+ revenue and...
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company that has quietly…
Read More
AI Dilemma: Emerging Tech as Cyber...
AI is fundamentally transforming the modern world. It offers previously out-of-reach opportunities for business leaders to anticipate market trends and make better decisions.…
Read More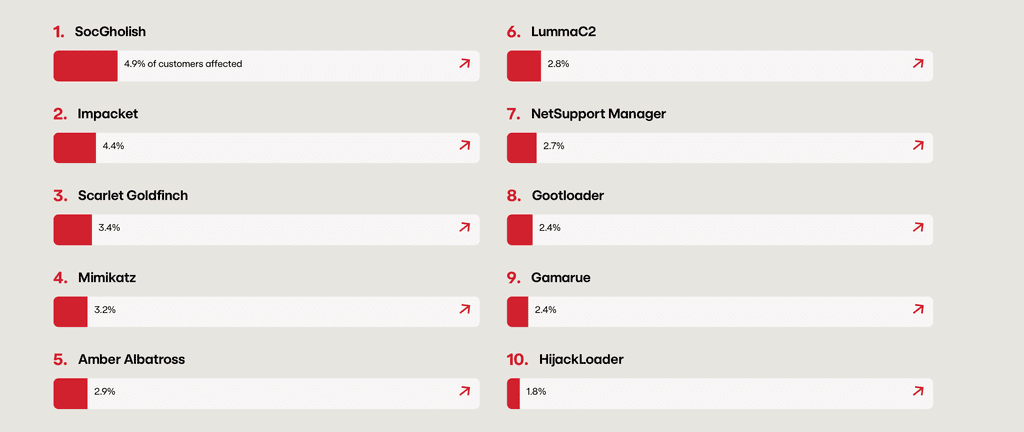
A Deep Dive into Impacket Remote...
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate real-world attacks. However,…
Read More
Keren Elazari Decrypts the Ransomeware Nightmare
Ransomware is a type of malware that allows hackers to commandeer data on a device or an entire network. Increasingly, the threat actors…
Read More
Enhancing Endpoint Visibility Through a Unified...
It’s easy to miss critical signs when endpoint tools work in isolation. When a laptop shows unusual behavior but its network or cloud…
Read More
Public exploits released for Citrix Bleed...
Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is easily…
Read MoreCategories
Latest Articles