
Using 2nd Sight Lab’s aws-deploy to...
Steps to deploy all the things — and summary of how I used AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI…
Read More
Top 10 Dynamic Application Security Testing...
What is DAST and how does it work? Dynamic application security testing (DAST) is a cybersecurity assessment method that analyzes running applications to…
Read More
Addressing Our ‘Age of Insecurity’ —...
In her award-winning book The Age of Insecurity: Coming Together as Things Fall Apart, Astra Taylor makes the argument that everyone feels insecure.…
Read More
Integrating SIEM Threat Intelligence for Better...
In today’s cybersecurity environment, businesses face increasingly sophisticated threats that evolve quickly and often bypass traditional defenses. As such, having an effective security…
Read More
Why Storage Providers Can’t Ignore Cyber...
With the advent of newer technologies, storage providers have increasingly had to rely on digital means for dealing with data, customer information, and…
Read More
Senator Chides FBI for Weak Advice...
Agents with the Federal Bureau of Investigation (FBI) briefed Capitol Hill staff recently on hardening the security of their mobile devices, after a…
Read More
Why Nation-States Are Hacking the Power...
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖, In Part 1…
Read More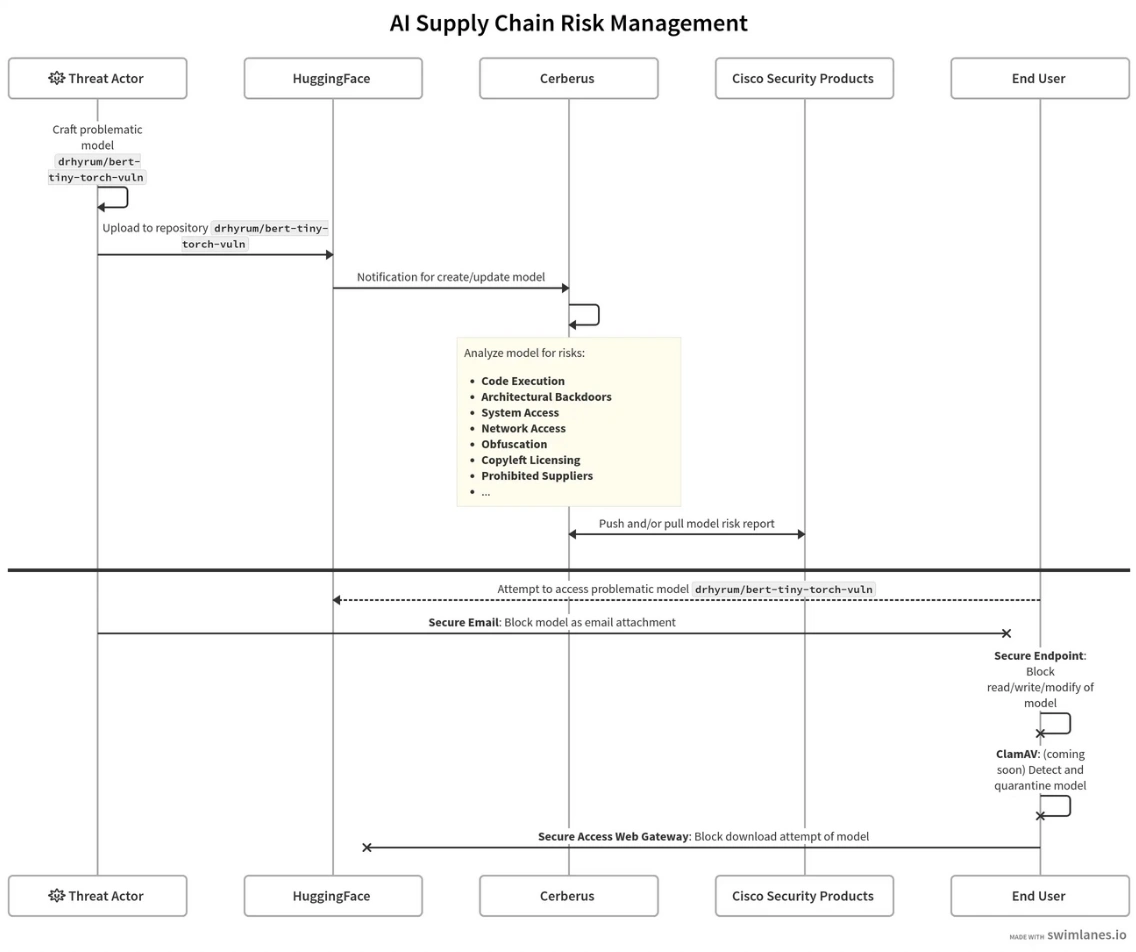
Securing an Exponentially Growing (AI) Supply...
The global AI race is in full swing, and its battleground? HuggingFace It took eight years for the platform to reach 1 million…
Read More
Hijacking Your Resources for Profit
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems, validating transactions on…
Read More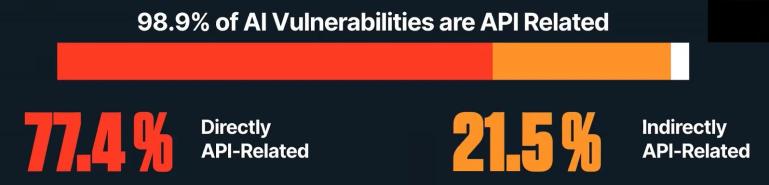
The Rise of AI-Driven API Vulnerabilities
AI has had dramatic impacts on almost every facet of every industry. API security is no exception. Up until recently, defending APIs meant…
Read MoreCategories
Latest Articles