
The Real Meaning Behind the Jargon...
Cyber security is often conflated with the term confidentiality, but that is not correct. Traditionally, professionals tend to define it as being about…
Read More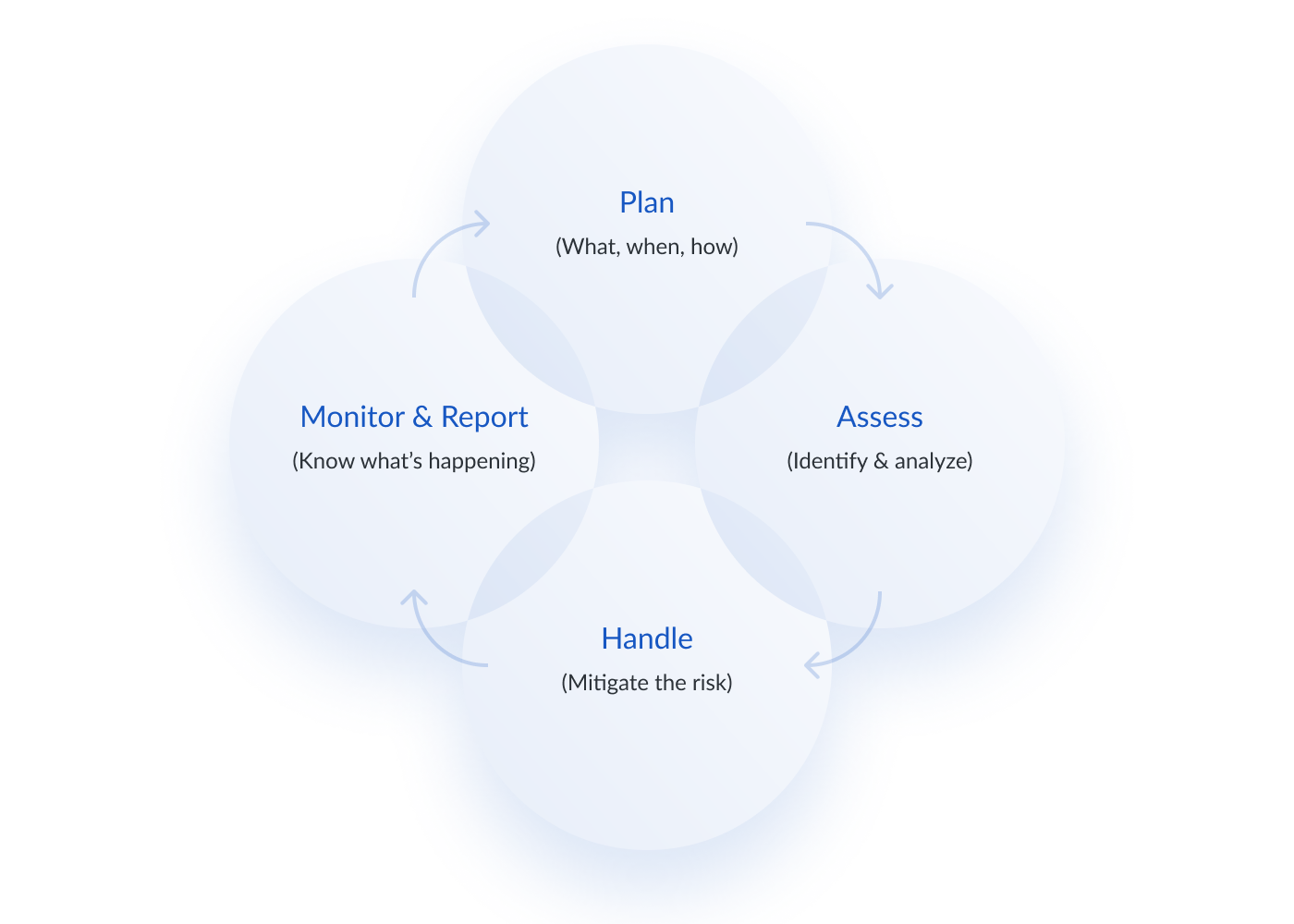
What is Information Risk Management?
Information Risk Management (IRM) is a form of risk mitigation through policies, procedures, and technology that reduces the threat of cyber attacks from vulnerabilities and poor…
Read More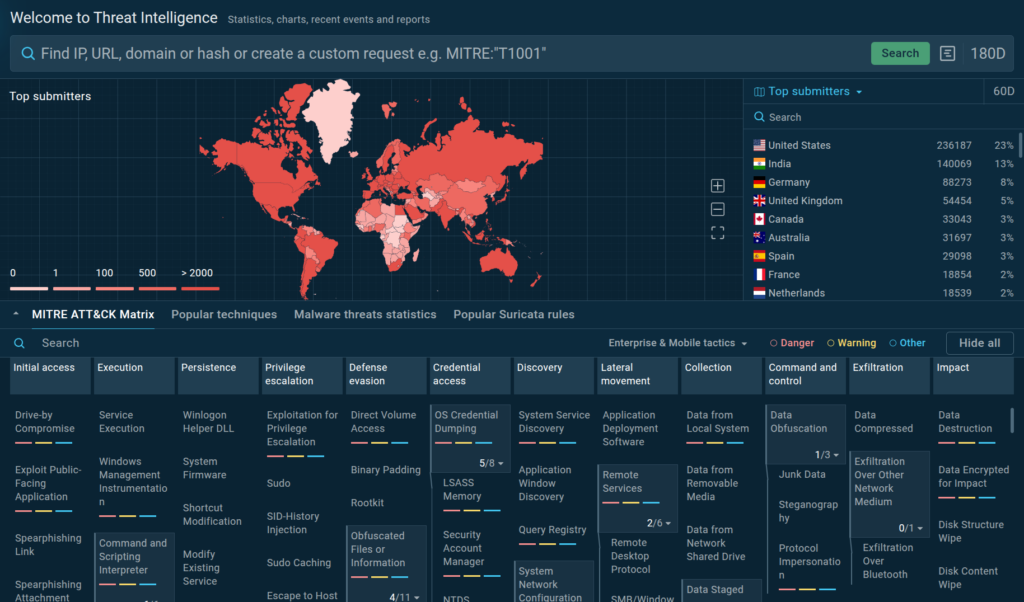
Threat Hunting: Hands-on Tips for SOC...
HomeCybersecurity Lifehacks Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs Editor’s note: The current article is authored by Clandestine, threat researcher and threat…
Read More
RSAC Fireside Chat: Operationalizing diverse security...
Catastrophic outages don’t just crash systems — they expose assumptions. Related: Getting the most from cyber insurance At RSAC 2025, I met with…
Read More
PCI Key Management Operations (KMO) v1.0...
From 16 June to 18 July, eligible PCI SSC stakeholders are invited to review and provide feedback on the draft PCI Key…
Read More
Max McCoy Investigates $47 Million That...
Max McCoy stumbled on a $47 million swindle that starts just north of the Oklahoma panhandle and bounces to Australia before things get…
Read More
How to Get the Most from...
Hello CyberBuilders 🖖 Next week, I am heading to Forum InCyber 2025, and I want to give you a quick preview of what…
Read More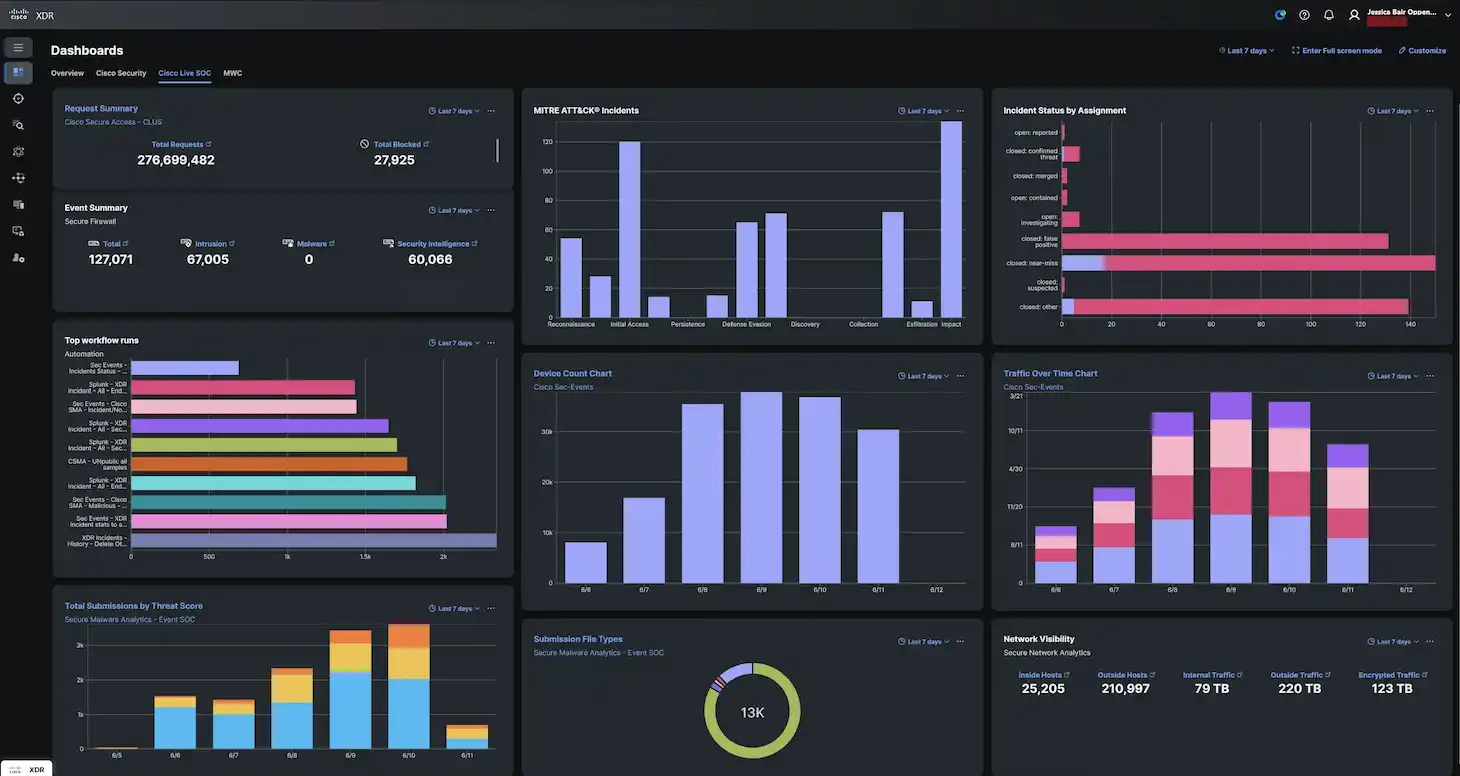
Cisco Live San Diego Case Study:...
Additional Post Contributors: Mindy Schlueter On June 11, the Cisco Live San Diego SOC received a Cisco XDR Incident triggered by two Cisco…
Read More
Deep Fake Detection: Safeguarding Digital Media...
In this post, I will discuss deep fake detection. This will help you in safeguarding digital media authenticity in an AI-generated world. The…
Read More
Key Features for Business Protection
As the threat landscape for businesses continues to grow more complex, ensuring robust cybersecurity has become a critical priority. With an increase in…
Read MoreCategories
Latest Articles