How government cyber cuts will affect...
Deep cuts in cybersecurity spending risk creating ripple effects that will put many organizations at a higher risk of falling victim to cyberattacks…
Read More
Android malware Anatsa infiltrates Google Play...
The Anatsa banking trojan has sneaked into Google Play once more via an app posing as a PDF viewer that counted more than 50,000 downloads.…
Read More
Password Spraying Attacks Hit Entra ID...
Identity & Access Management , Security Operations Hackers Use TeamFiltration Penetration Testing Tool Prajeet Nair (@prajeetspeaks) • June 12, 2025 Image:…
Read More
How OAuth and device code flows...
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and OAuth application abuse.…
Read More
News alert: Halo Security’s attack surface...
Miami, June 18, 2025, CyberNewswire — Halo Security today announced that its attack surface management solution has been named a 2025 MSP Today…
Read More
Citrix Patch Chaos NetScaler Update Breaks...
Ingram Safepay SafePay ransomware cripples Ingram Micro’s global operations, disrupting IT supp… The technology distribution giant Ingram Micro confirmed on July 6, 2025,…
Read More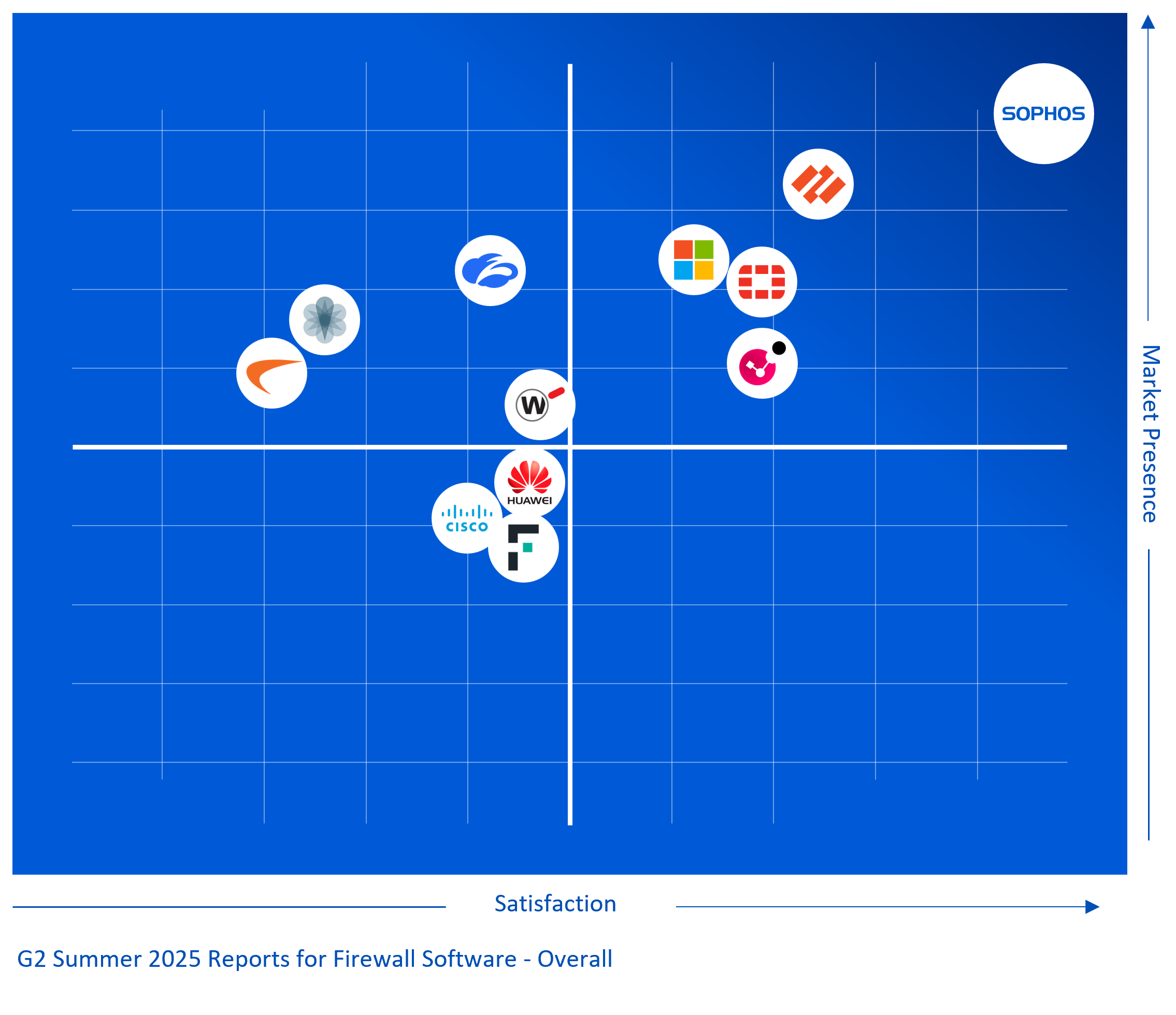
Sophos Firewall Recognized as the #1...
Customers have spoken, and the results are in. G2, a major technology user review platform, has just released their Summer 2025 Reports, where…
Read More
10 immutable laws of security, 25...
Back in 2000, the Microsoft Security Response Center released an article titled “10 Immutable Laws of Security“, describing what they believed were some…
Read More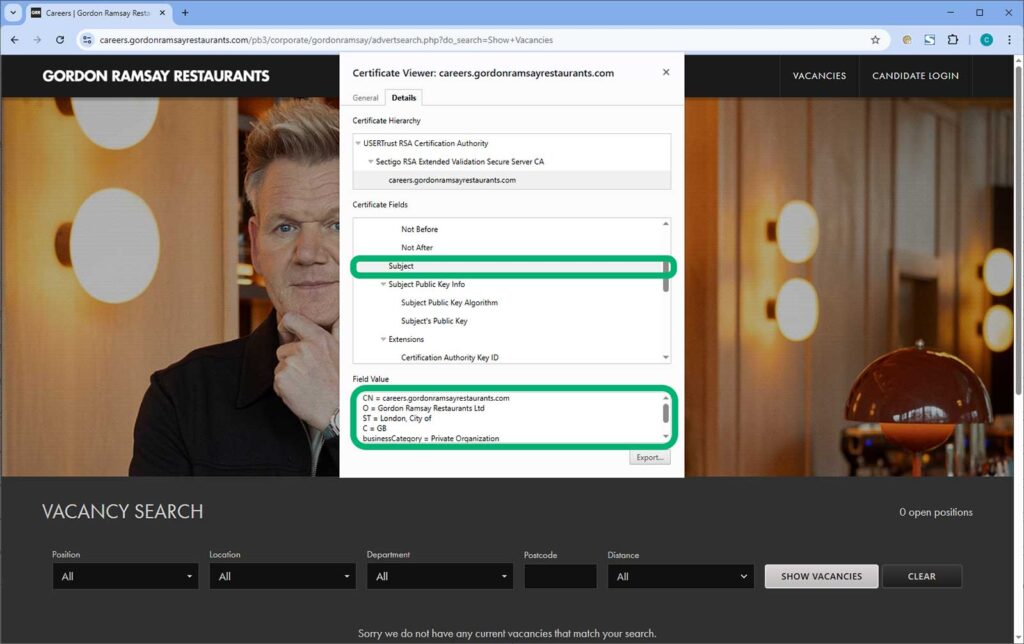
8 Practical PKI Uses & Applications...
More than half of the breaches investigated by Verizon in its 2025 DBIR report stemmed from system intrusions. Discover which PKI use cases…
Read More
Bridging the Security Knowledge Gap: Introducing...
The challenge of maintaining robust web application security often comes down to communication. Security teams frequently spend countless hours explaining WAF blocking decisions…
Read MoreCategories
Latest Articles