
What Are SWIFT Security Controls? Framework,...
SWIFT, the global backbone for secure financial messaging, plays a critical role in enabling fast and reliable cross-border transactions. But as cyber threats…
Read More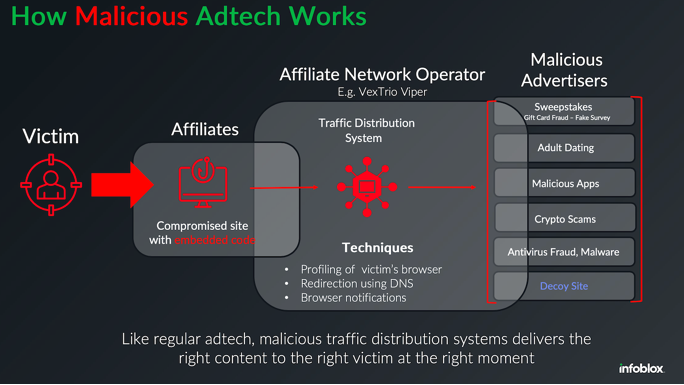
Inside a Dark Adtech Empire Fed...
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same…
Read More
Meet This Year’s North America Community...
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our podcast series, Coffee…
Read More
Five Uncomfortable Truths About LLMs in...
Many tech professionals see integrating large language models (LLMs) as a simple process -just connect an API and let it run. At Wallarm,…
Read More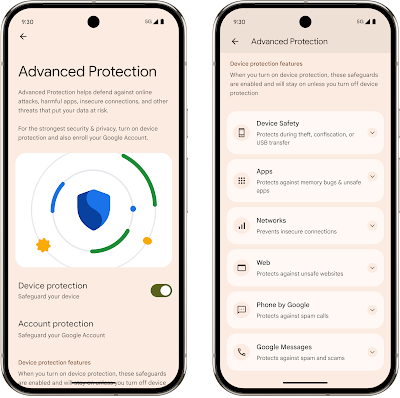
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment at Google, which…
Read More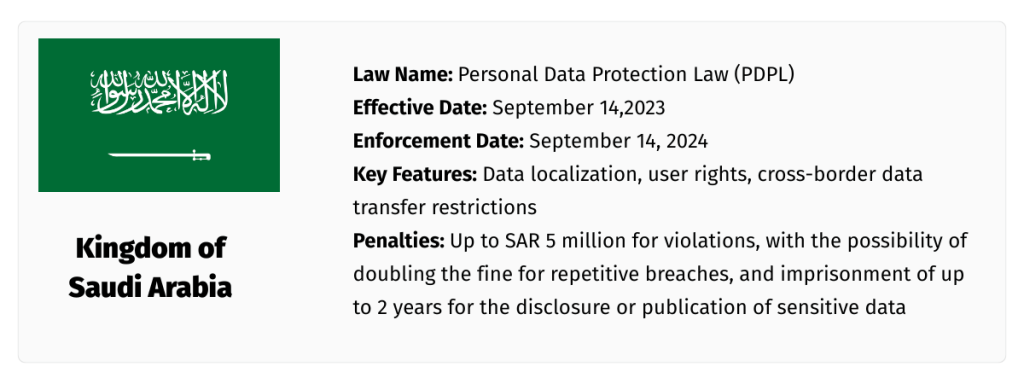
How the Middle East Is Defining...
Middle East Privacy A new chapter in data privacy is being written across the Middle East—one that’s defined by momentum, modernization, and a…
Read More
How a 12-year-old bug in Sudo...
The vulnerability, with a critical CVSS rating of 9.3 out of 10, affects Sudo versions 1.9.14 through 1.9.17, and Stratascale researchers said they…
Read More
My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power infrastructure during early…
Read More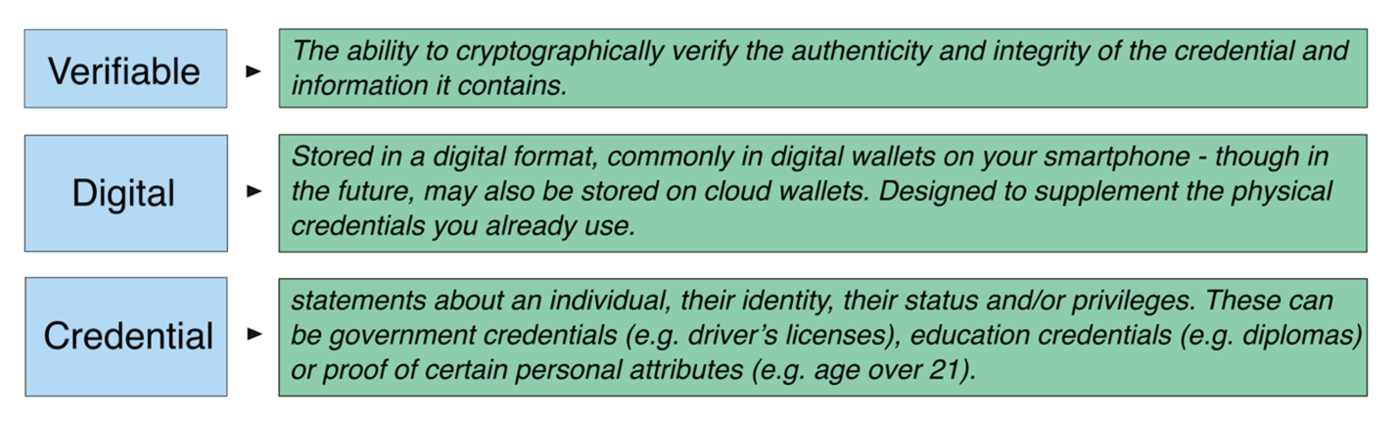
Digital Identities: Getting to Know the...
If you are interested in the world of digital identities, you have probably heard some of the buzzwords that have been floating around…
Read More
Scattered Spider Attacks US Airlines –...
From courtroom breaches to cockpit infiltration, here’s this week’s Cyber Snapshot. Five critical stories you need on your radar, with safety advice included.…
Read MoreCategories
Latest Articles