
Amazon Q For Code to Deploy...
WARNING: Do not blindly create IAM resources with AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The Code. 🔒 Related…
Read More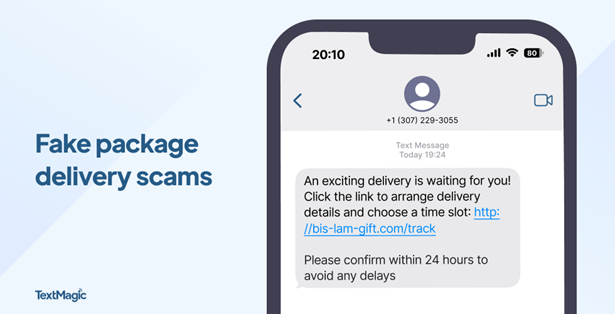
Mobile security matters: Protecting your phone...
It all starts so innocently. You get a text saying “Your package couldn’t be delivered. Click here to reschedule.” Little do you know, clicking…
Read More
A Guide to Developing Security-First Culture...
HomeCybersecurity Lifehacks A Guide to Developing Security-First Culture Powered by Threat Intelligence Security-First Culture (SFC) is an organization-wide commitment where security considerations influence…
Read More
The Impact of Security Breaches on...
This blog was originally published by Bravura here. Educational institutions oversee hundreds or thousands of students and faculty members daily. Therefore, it’s…
Read More
The Importance of Cybersecurity Training for...
Cybersecurity stopped being an IT issue a long time ago. It took precedence as a business priority as cyber attackers began evolving their…
Read More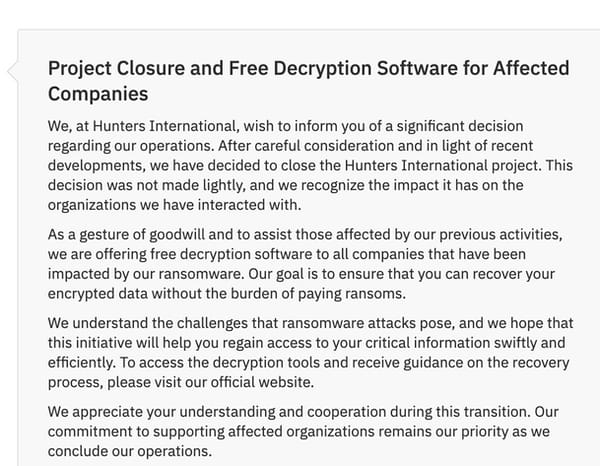
Hunters International ransomware group shuts down
The notorious Hunters International ransomware-as-a-service operation has announced that it has shut down, in a message posted on its dark web leak site.…
Read More
How Modern XDR Platforms Spot Insider...
Most people imagine hackers, ransomware, or harmful software when they hear about cybersecurity threats. However, a quieter danger often comes from within —…
Read More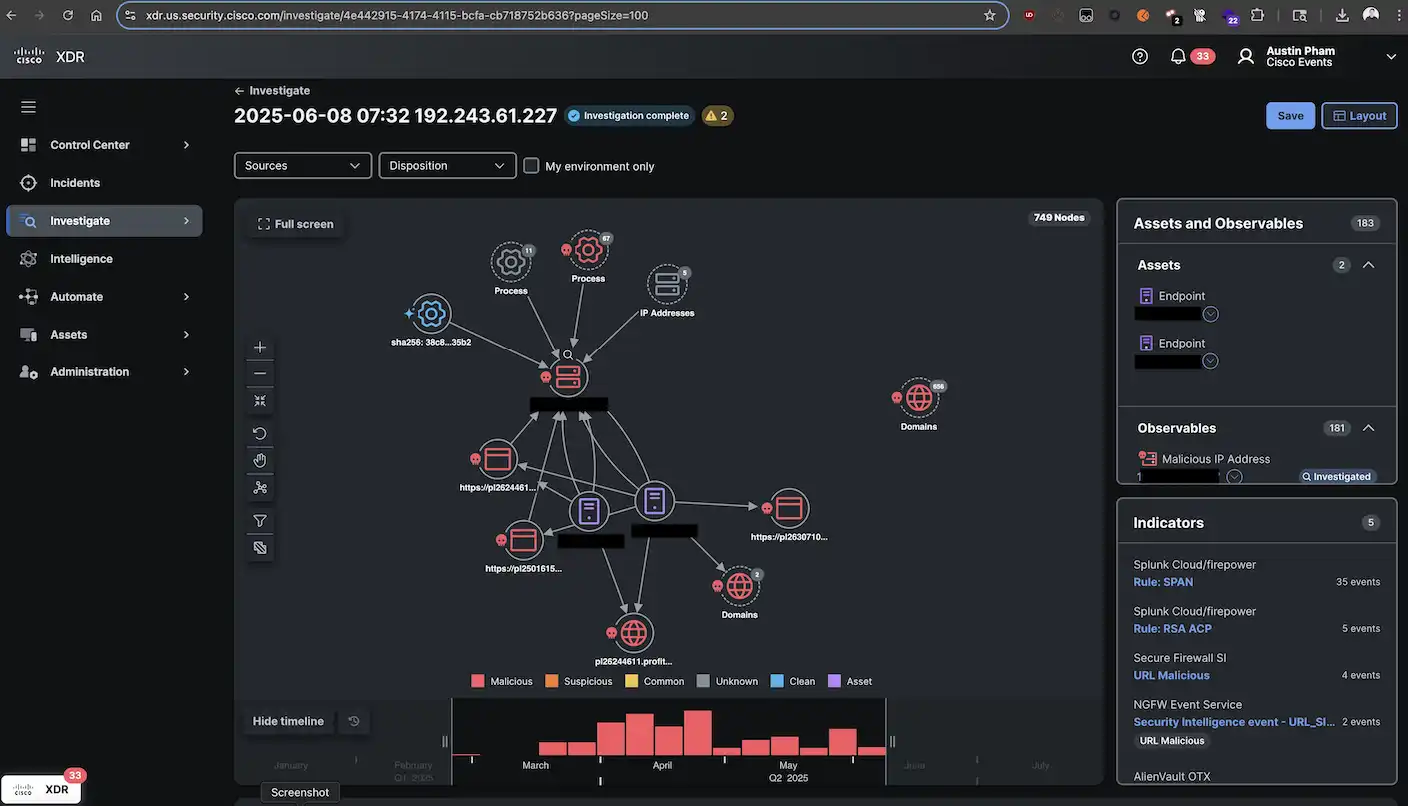
Splunk in Action at the Cisco...
Additional Post Contributors: Austin Pham, Tony Iacobelli Cisco and Splunk, together, elevate the SOC’s Incident Detection and Response experience to the next level…
Read More
Fairfax County, Va., CISO Michael Dent...
I have known Michael Dent, the Fairfax County, Va., chief information security officer, for more than a decade, and his knowledge, expertise, insights,…
Read More
EDR Providers vs Traditional Security Tools:...
With ever-changing cyber threats, businesses need to redefine their security strategy. Although traditional security tools like antivirus software and firewalls have long been…
Read MoreCategories
Latest Articles