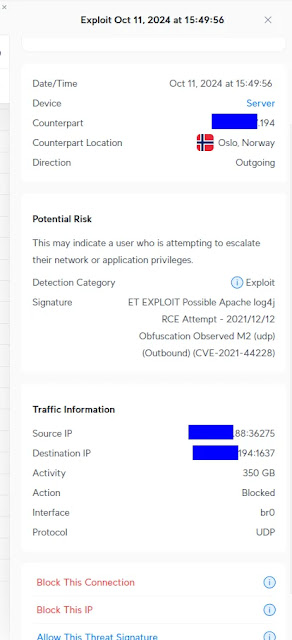
What Are Normal Users Supposed to...
Probably once a week, I see posts like this in the r/Ubiquiti subreddit. Ubiquiti makes network gear that includes an “IDS/IPS” feature. I…
Read More
Everything You Need to Know
The business world runs on email. It’s our primary method of communication, both internally and externally, which makes it both a necessity and…
Read More
Using AI to identify cybercrime masterminds...
Online criminal forums, both on the public internet and on the “dark web” of Tor .onion sites, are a rich resource for threat…
Read More
Is hacktivism acceptable? — Matt Palmer
This week I attended CSO Online’s CSO Security Summit in London, which was tracked into protection and culture tracks. One of the most…
Read More
How To Save Your Children From...
If you’re a parent and haven’t been in touch with gaming for a while, you’d be surprised at how much it has changed.…
Read More
Cybersecurity Advisory: Hackers Exploit Zoom’s Remote...
A newly uncovered cyberattack campaign is exploiting Zoom’s Remote Control feature to infiltrate the systems of cryptocurrency traders and venture capitalists. Named “Elusive…
Read More
MY TAKE: Microsoft takes ownership of...
Last week at Microsoft Build, Azure CTO Mark Russinovich made headlines by telling the truth. Related: A basis for AI optimism In a…
Read More
Bridging the Nursing Workforce Skills Gap...
The US is facing a critical nursing workforce challenge, with increasing shortages and evolving skill demands. As healthcare facilities scramble to fill gaps,…
Read More
Hackers Use Leaked Shellter Tool License...
Jul 08, 2025Ravie LakshmananMalware / Cybercrime In yet another instance of threat actors repurposing legitimate tools for malicious purposes, it has been discovered…
Read More
Competing with layer zero in cybersecurity
I am not aware of anyone who has previously attempted to define the concept of layer zero in security. Chances are, you will…
Read MoreCategories
Latest Articles