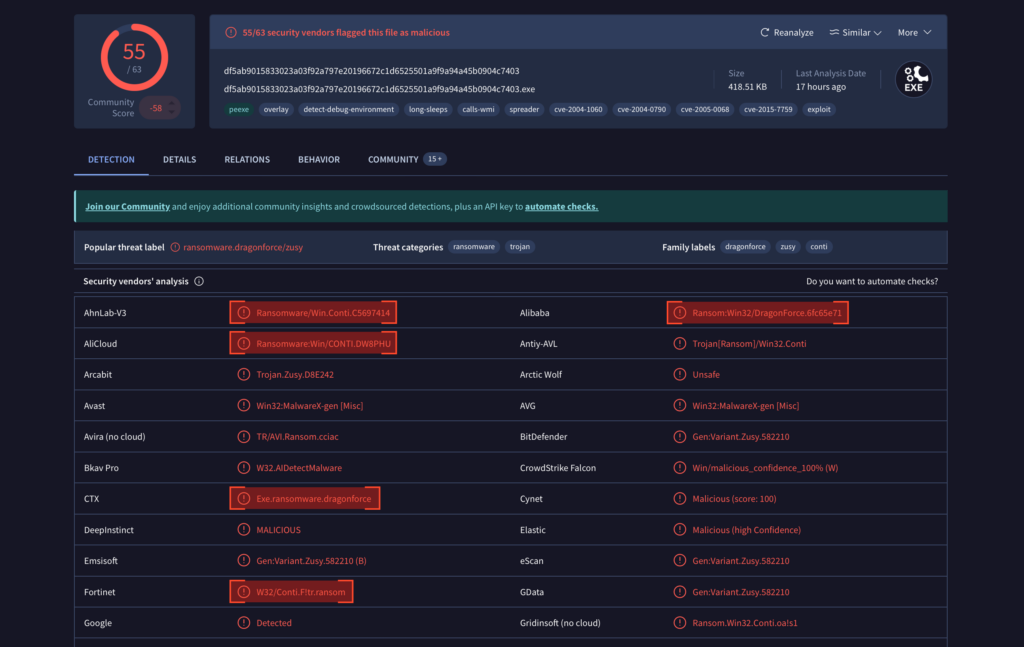
DEVMAN Ransomware: Analysis of New DragonForce...
HomeMalware Analysis DEVMAN Ransomware: Analysis of New DragonForce Variant Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and…
Read More
GUEST ESSAY: The AI illusion: Don’t...
Artificial intelligence is changing everything – from how we search for answers to how we decide who gets hired, flagged, diagnosed, or denied.…
Read More
11 Key Benefits You Should Know
What is SOC 2 Certification? SOC 2 certification is an audit framework developed by the AICPA that evaluates an organization’s ability to design…
Read More
Surveillance, spyware, and self-driving snafus •...
A Mexican drug cartel spies on the FBI using traffic cameras and spyware — because “ubiquitous technical surveillance” is no longer just for…
Read More
GrayAlpha Operation Detection: The Fin7-Affiliated Group...
Defenders have identified a highly sophisticated campaign orchestrated by the GrayAlpha threat actors. In this campaign, hackers employ fake browser updates and other…
Read More
Top Themes at 2025 NASCIO Midyear
“It was the best of times, it was the worst of times.” This famous opening line from Charles Dickens’ novel A Tale of…
Read More
4 Mindset Shifts for Making Zero...
This blog was originally published by Cerby here. Zero Trust has become one of the cybersecurity world’s most misunderstood buzzwords. In theory, it’s…
Read More
Data Privacy Manager Selected for CyberBoost...
We’re proud to share that Data Privacy Manager has been selected for CyberBoost Catalyse, a prestigious accelerator programme backed by the Cyber Security…
Read More
Patch Tuesday, June 2025 Edition –...
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that one of…
Read More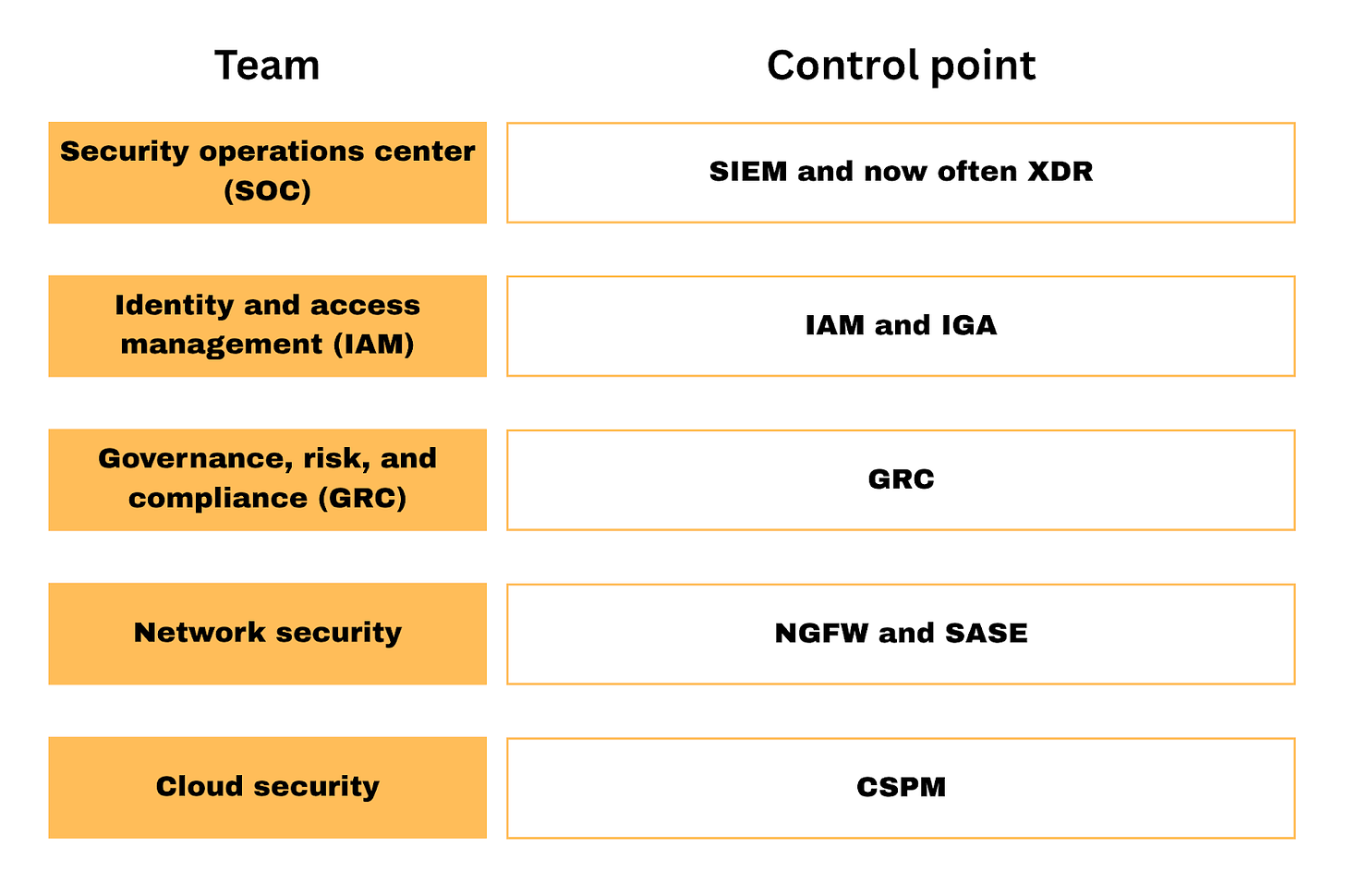
Owning the control point in cybersecurity
Dave Yuan, a venture capitalist at Tidemark who has spent over 20 years investing, likes to discuss the concept of a “control point.”…
Read MoreCategories
Latest Articles