
New Android TapTrap attack fools users...
A novel tapjacking technique can exploit user interface animations to bypass Android’s permission system and allow access to sensitive data or trick users into…
Read More
Don’t Be a Victim! Blackmail Scam...
Sextortion scam emails have become a disturbingly common occurrence in people’s inboxes. These menacing messages claim the sender has hacked your computer, recorded…
Read More
Incogni Vs DeleteMe – Which Is...
Read on for the Incogni vs DeleteMe comparison. Your data on data brokers and people search websites is a huge risk. Anyone can…
Read More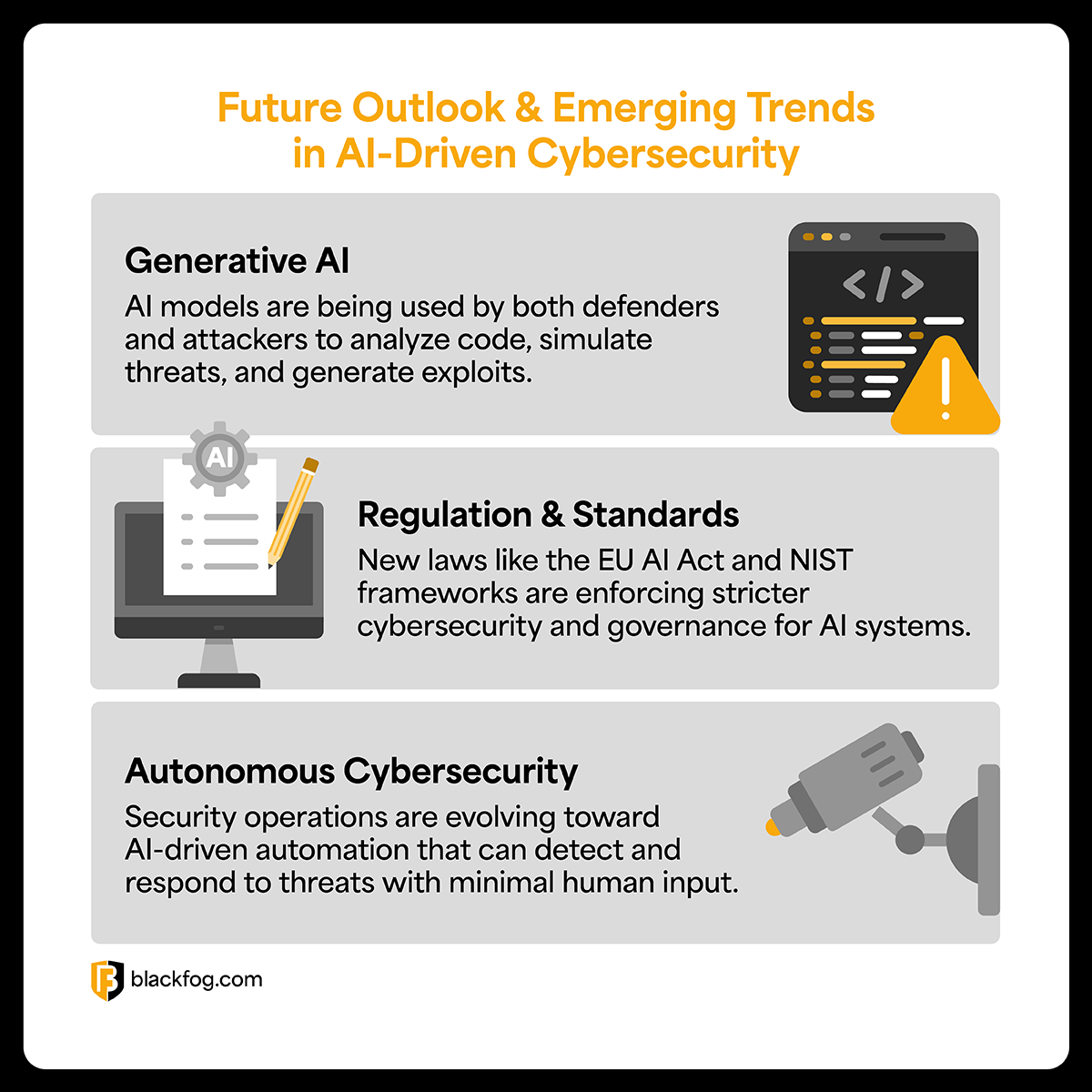
AI in Cybersecurity: The Good, the...
The Good – How AI Is Strengthening Cybersecurity AI systems are helping security teams with faster, smarter threat detection and response. New AI…
Read More
U.S. Sanctions Cloud Provider ‘Funnull’ as...
Image: Shutterstock, ArtHead. The U.S. government today imposed economic sanctions on Funnull Technology Inc., a Philippines-based company that provides computer infrastructure for hundreds…
Read More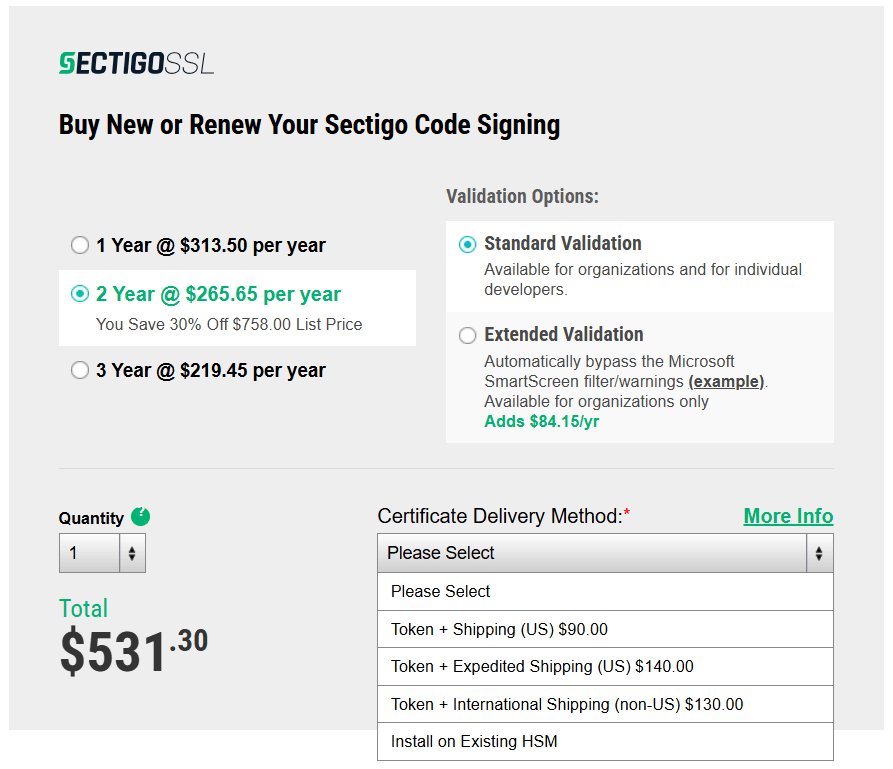
How to Use Google Cloud KMS...
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a Sectigo Code Signing…
Read More
Key Network Questions
I wrote this on 7 December 2018 but never published it until today. The following are the “key network questions” which “would…
Read More
Reinventing Cyber Defence with Proper Licensing
Date: 1 July 2025 Once business goals are set and the appropriate SAP product suite is selected, the next step is to consider…
Read More
Was ist ein Botnet?
Ein Botnetz besteht aus vielen “Zombie”-Rechnern und lässt sich beispielsweise einsetzen, um DDoS-Attacken zu fahren. Das sollten Sie zum Thema wissen. FOTOKINA |…
Read More
a field guide for security people
If you were to ask me three years ago if I think that security professionals should understand how startups work, I’d have answered…
Read MoreCategories
Latest Articles